MIMO Fake Cell Towers Allow mobile interception device can intercept cellular data to Keep Track of You
Fake Cell Towers Allow the NSA and Police to Keep Track of You
The Internet is abuzz with reports of mysterious devices sprinkled across America—many of them on military bases—that connect to your phone by mimicking cell phone towers and sucking up your data. There is little public information about these devices, but they are the new favorite toy of government agencies of all stripes; everyone from the National Security Agency to local police forces are using them.
These fake towers, known as “interceptors,” were discovered in July by users of the CryptoPhone500, one of the ultra-secure cell phones released after Edward Snowden’s leaks about NSA snooping. The phone is essentially a Samsung Galaxy S3 customized with high-level encryption that costs around $3,500. While driving around the country, CryptoPhone users plotted on a map every time they connected to a nameless tower (standard towers run by wireless service providers like Verizon usually have names) and received an alert that the device had turned off their phone’s encryption (allowing their messages to be read).
Map showing the location of rogue cell towers identified by the firewall on CryptoPhones in August via ESD America, a defense and law enforcement technology provider based in Las Vegas.
While the abilities of these interceptors vary, the full-featured versions available to government agencies are capable of a panoply of interceptions. For example, the VME Dominator can capture calls and texts, and can even control the intercepted phone. (In an interview with NBC, Snowden revealed that with this kind of technology the NSA is capable of turning on a powered-down phone and essentially using it as a bug.)
This NSA-style surveillance is spreading to local cops. A growing number of police departments are using tower-mimicking devices, “stingrays,” to track a cell phone’s location and extract call logs. Though little is known about the use of these devices, watchdog groups have scored small victories in their attempts to punch through this veil of secrecy. The map below, courtesy of the ACLU, shows how the use of stingrays is spreading. The map also shows that despite the ALCU’s greatest efforts, it is unable to uncover information about stingray use in most of the country.
A recent case provided a glimpse into what stingrays can do and how they are being used.
Awesome Resources explains how anyone with a mobile interception device can intercept cellular data
Mobile networks are dominant in the age of communication and are used to relay mobile communication signals to Public Switched Telephone Networks (PSTN). There is a lot of information that is exchanged on a daily basis. But is your mobile network confidential?
| Your mobile phone can be used for industrial espionage, unauthorized transfer of data, or for trading secrets of the enterprises. All this is done through interception of mobile signals, voice calls or using your mobile as a bug. You’d be surprised to hear what’s to follow in this article.
We bring you devices, types, and techniques for mobile interception. Sit tight as we prepare you against being a victim of malicious interception practices. What is mobile interception?Mobile interception technology is the storage, recording, tracking, and interception of cellular communications like phone calls, internet usage, SMS, etc. This technology is primarily used for gathering intelligence regarding terrorist or criminal activities. |
Even though it started out as an ethical technology for security, there are reports about the misuse of the technology doing the rounds.
However, for those concerned about their privacy during calls, using tools like Call Recorder iCall can provide an added layer of security by recording and securely storing conversations.
How does mobile interception work?
There are three types of mobile networks – NGN (Next Generation Networks like 3G, 4G, and 5G), GSM (Global System for Mobile communications) and CDMA (Code Division Multiple Access). All three of them are targets of multiple surveillance technologies.
When the mobile phone data travels over these networks, they are passively intercepted between the mobile phone and the base station it is communicating to. Both uplink signal (outgoing voice or data) and downlink (incoming voice or data) signals can be intercepted.
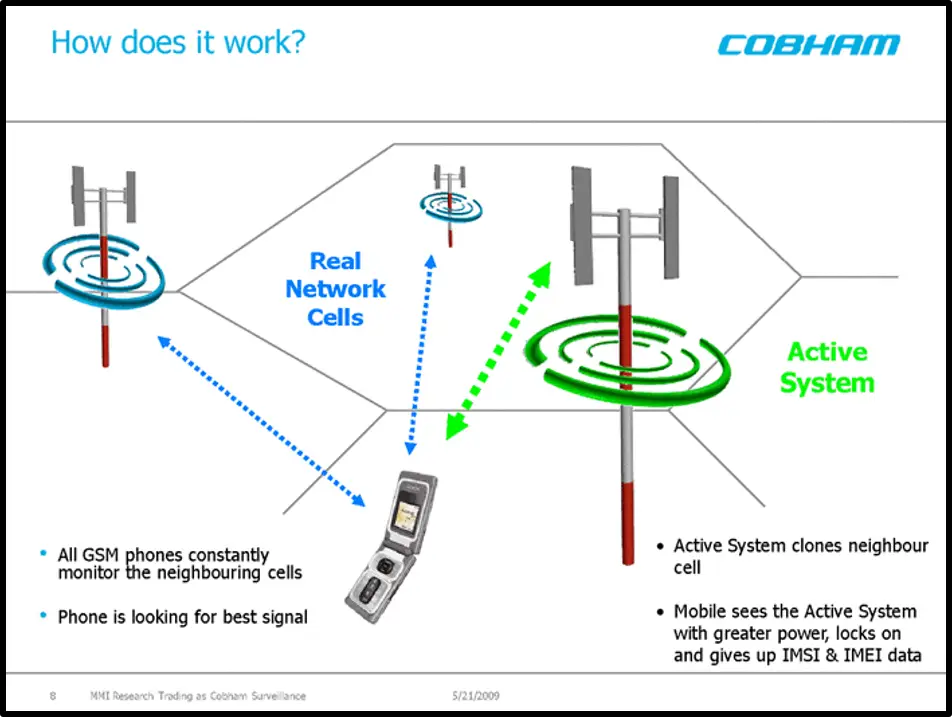
Source: Cobham Survaillance
Who can intercept your mobile signal?
Mobile Interception technology is extensively used by law enforcement agencies, military & defense, or authorities like government and federal & local law enforcement agencies (LEAs). These are also termed as Lawful Interceptions. But there are unauthorized intercepts too!
Our expert Sam Tilston from AwesomeResources.co.uk, a professional in cyber security for more than 20 years believes that anyone with a mobile interception device can intercept cellular information like- voice, data transmission, and metadata.
Lawful Interception (LI) – The modern legal interception protocol
Lawful Interception or LI refers to a specific facility in telecommunications where LEA or government with court orders or legal authorization can intercept mobile signals. In common parlance it’s also called selective wiretapping or authorized wiretapping.
Lawful interception is different from the dragnet-type mass surveillance and is usually carried out by intelligence agencies. The data is merely passed through a fiber-optic splice where its extracted and filtered.
Many countries follow local, national, and global standards for lawful interception laid down by ESTI. Governments and authorities require PSPs (Public Service Providers) to install a (LIG) legal interception gateway and LIN (legal interception nodes) for real-time interception.
Lawful Interception architecture
Currently the global standard for Lawful Interception and its architecture is provided by ESTI. The standard architecture in recent use is 3GPP Evolved Packet System (EPS) that provides IP based services.
The ESP architecture attempts to define an extensible and systematic means by which LEAs and network operators can interact. There are three stages in the architecture:
- Collection: target-related call content and data are extracted from these PSP networks.
- Mediation: data is formatted to match the specific standard.
- Delivery: The content and data are delivered to the law enforcement agencies.
Delivery function in the architecture is what is used to hide your sensitive interceptions from Intercepting Control Element (ICE). Even when there are multiple targets on the same number, the authorities have no idea about it.
What is the need for mobile interception?
Apart from the malicious effects like snooping and eavesdropping, mobile interception can be used for security. Want to know the uses?
1. Administration Security
The Administrative function (ADMF) keeps all the intercept activities of individual LEAs separate and interfaces to the intercepting network.
After configuring authorized user access within the network, password protection can be enabled using one of the following security mechanisms:
- CUG/VPN
- COLP
- CLIP
- Authentication & Encryption
2. IRI (Intercept Related Information) security
In case of communication failures, IRI can be buffered in the 3G network. After successfully transmitting IRI, the content buffer and total buffer can be deleted via a command or a timer. This prevents the IRI data from being exposed to illegal use.
3. CC (Call Content) security
Data inconsistency, log files, and critically important data like billing information can be suppressed to be viewed by only a fraction of the users over the network. This data can also be deleted after successful transmission to the required personnel.
Can your mobile be intercepted?
If you’re in the crosshairs of the authorities, then chances are that you may be under surveillance right now. Don’t worry, if you’re under one, then you’re not alone!
Lawful interceptions are very common, in fact there are 2000-3000 mobile signals being intercepted and analyzed every day. In fact, if you have a few selected smartphone models from Samsung, chances are that your calls are being intercepted.
The presence of Shannon-branded baseband chips, a tracing IC (integrated circuit) and RF (radio frequency) transceiver make it a device that can be easily intercepted. Calls and messages can be intercepted by creating a proxy base station by frankly anyone with a device.
What is the future of mobile interception market?
The market of mobile interception is estimated at $1.8 billion globally, and $ 226.1 million in the U.S. alone. The market is estimated to grow at a tremendous rate of 5.8% annually for the next decade.
With new developments of communication frequencies, networks and channels, integration with newer interception systems will create a little hurdle. New and portable devices are being deployed every day across the world to hamper the mobile interception market.
In summary
Mobile interception is a debatable topic. On one hand, you are always on someone’s radar and that’s something that you can’t live with knowing. On the other hand, it’s a crucial and apt technology for intercepting malicious calls and threats.
As hard as it may sound, it’s hard to negate the importance of mobile interception, as long as it’s legal, and meets the global standards of lawful interception.
Hey, as long as it continues to save millions of lives by combating increasing criminal activities and security threats, it’s always a handy technology and probably will be in the future too. source
Understanding MIMO (Multiple Input, Multiple Output) – Cellular Speed & Booster Implications
The Wonders of MIMO
For RVers and Cruisers, understanding what MIMO technology is, how it works, and how it can be used to enhance cellular speeds has the potential to make finding great mobile internet on the road an easier experience.
For anyone who knows a thing or two about wireless communications, modern 4G/LTE and 5G cellular radios are borderline miraculous.
Consider the first iPhone – which launched in 2007 with a maximum theoretical cellular speed of around 500 Kbps using AT&T’s 2G EDGE cellular network.
A decade and a half later – the latest flagship cellular devices were able to support maximum theoretical speeds of over 2,000 Mbps.
That’s more than a 4,000x increase!
And as the 5G era has matured and become more mainstream, we see peak theoretical speeds are approaching 10 Gbps, another 10x increase!
Of course, theory rarely equals reality – and the cellular networks need to be substantially upgraded and built out to even come close to being able to deliver speeds like this to real people outside of a lab.
And in the real world – you will be sharing this speed with perhaps hundreds or thousands of others connected to the same cell tower.

But real-world 4G/LTE speeds over 50Mbps are actually not at all uncommon, and speeds over 100Mbps are now widely reported, and things just keep getting faster. Mid band 5G is has become lot more common on most of the carriers and we are now seeing the gap between really good LTE and good mid band 5G become way more prevalent in everyday connectivity. If you are in a mmWave 5G area, the speeds can be blazing fast.
One of the key technologies making these sorts of speeds possible is known as MIMO (Multiple Input, Multiple Output) – an incredibly clever technique for putting multiple antennas to work to increase both data transmission speed and reliability.
MIMO technology is fundamental to both 4G/LTE, 5G, and WI-Fi radios – but cellular boosters and MIMO have some… challenges… working together.
Read on to get a grasp of what MIMO is, how it works, and how you can use a little bit of MIMO awareness to potentially increase your cellular speeds.
MIMO In A Nutshell
MIMO is one of the core technologies enabling 4G/LTE and 5G cellular, and almost every modern mobile device (whether a phone or a hotspot) has two or more cellular antennas on board to enable the magic of MIMO.
On the other end of the line – cell towers typically have multiple antennas working together in tight synchronization to communicate with you.
With more antennas transmitting a signal, there are more possible echoes and reflections (read the “how it works” section below to understand the magic here) for the receiving device to catch a signal.
The ability to make multiple connections on the cell tower the better the transmit speeds, even with weak signals.
The cell tower will have a number of transmit/receive antennas and many LTE devices had two antennas. This allows those devices to utilize 2×2 MIMO.
Devices with four antennas for 4×4 MIMO is now common, with consumer devices such as flagship hotspots such as the AT&T Netgear Nighthawk M6 Pro Hotspot Pro, the Verizon & T-Mobile MiFi X Pro 5G hotspots, plus all the the latest flagship smartphones from Apple, Samsung, and Google.
Although the latest cellular standards (Category 18 & higher) support 8×8 MIMO, consumer devices with 8 antennas are not common.
These antennas connect to a cell tower that will usually have at least four antennas – and as many as 128! The number of antennas on the tower gives devices more options to get a good, high-performing connection.
This figure illustrates a relatively simple 4×2 MIMO deployment. In this case, 4×2 means four transmit/receive antennas on the tower, and two on the user device:
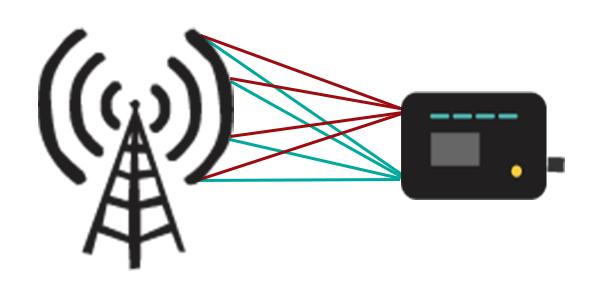
This 4×2 configuration isn’t the only one possible, however, upgraded cell towers can have many more transmit/receive antenna elements. The latest devices typically have four antennas to better take advantage of the cell towers antenna array.
MIMO is one of the key technologies that allow these devices to have such great performance – it really is pretty darn amazing stuff! source
MIMO vs Boosters Video
The program has existed since 2007, and is operated by the U.S. Marshals Service’s Technical Operations Group. It deploys Cessna aircraft from at least five airports that, combined, have a flying range that covers most of the U.S. population.
According to the Journal story, by Devlin Barrett, the planes carry a device called a “dirtbox” — the name is inspired by Digital Receiver Technology Inc., the Boeing subsidiary that makes the device — that acts like a cellphone communications tower.
Cellphones register user locations with towers every few minutes, even if they aren’t making a call.
By intercepting these signals, the dirtboxes can identify phones’ unique registration information — even phones with encryption like the new iPhone 6.
The device can pinpoint the location of a cellphone within 10 feet and manipulate the phone by jamming its signal. It can extract text messages and photos from phones, too.
Instead of asking cellphone companies for subscriber information, which law enforcement has done with increased frequency in recent years, agencies can now find it themselves.
In a single flight, the device can collect information about tens of thousands of cellphones. People familiar with the program told the Journal the device can identify phones linked to criminal suspects and keep that information, but “lets go” of information from other phones.
It’s unclear whether the government is keeping data about non-suspects gathered by the device.
Describing it as a “a dragnet surveillance program,” Christopher Soghoian, chief technologist at the American Civil Liberties Union, told the Journal: “It’s inexcusable and it’s likely — to the extent judges are authorizing it — [that] they have no idea of the scale of it.”
Courts are still catching up to technology like cellphone scanners. The Supreme Court has never considered whether this type of surveillance is a search requiring a warrant.
Earlier this year, the U.S. Court of Appeals for the 11th Circuit ruled law enforcement needs a warrant to get people’s phone location histories. However, the 5th Circuit took the opposite view last year.
The most recent Supreme Court case is United States v. Jones, a 2012 decision involving a GPS tracking device attached to a suspect’s car for month with no warrant. The Court decided attaching a device that gathered detailed information over time was a search, but didn’t say whether a warrant was required.
Civil liberties groups have already sued to challenge law enforcement use of similar devices, such as the Stingray, used on the ground by law enforcement to gather mobile data in a given area.
