Let’s face it, nowadays the normi’s don’t run anything, even if they have power, they run nothing! Machines Do! After from God (who is our creator and is #1) Knowledge is King on this planet, and those that know the machine will prosper in the next generation that is coming! The modern police force will not use guns those dumb shits will be out of a job one day when Cameras, Mic’s and AI can do their work and Protecting Citizens will be from men of intellect! Intelligence and skills from those that can program and protect the machines and their data they hold will be the King/Police Force in one! Just look at how Twitter changed America’s perception of Hunter Biden from one year to the next and now we have a full on conspiracy becoming completely true! The Nerds ran the show!
Google dork query
by Rahul Awati and Ivy Wigmore source
What is a Google dork query?
A Google dork query, sometimes just referred to as a dork, is a search string or custom query that uses advanced search operators to find information not readily available on a website.
Google dorking, also known as Google hacking, can return information difficult to locate through simple search queries. This includes information not intended for public viewing, but that is inadequately protected and can, therefore, be “dorked” by a hacker.
How Google dorking works
Google dorking is a passive attack or hacking method involving the use of a custom query. Hackers use Google to identify websites with security vulnerabilities and/or sensitive information the attacker can use, usually for some malicious purpose.
Around since 2002, dorking usually involves using a search engine as a hacking tool. Google’s tremendous web crawling capabilities facilitate dorking. With a Google dork, attackers can access a lot of information they wouldn’t be able to get with simple queries. This information includes the following:
- usernames and passwords
- email address lists
- sensitive documents
- personally identifiable information
- personally identifiable financial information
- website vulnerabilities
More often than not, this information is used for many types of illegal activities, including cybercrime, cyberterrorism, industrial espionage, identity theft and cyberstalking. Hackers may also sell this data to other criminals on the dark web for large sums of money
If used correctly, it can help in finding:-
Footholds -Queries that can help a hacker gain a foothold into a web server
Web Server Detection
– These links demonstrate Google’s awesome ability to profile web servers.
Files containing usernames
– These files contain usernames, but no passwords. Still, Google finds usernames on a web site.
Sensitive Directories
– Google’s collection of web sites sharing sensitive directories. The files contained in here will vary from sensitive to uber-secret!
Vulnerable Files
– HUNDREDS of vulnerable files that Google can find on websites
Files containing passwords – PASSWORDS, for the LOVE OF GOD!!! Google found PASSWORDS!
Vulnerable Servers
– These searches reveal servers with specific vulnerabilities. These are found in a different way than the searches found in the “Vulnerable Files” section.
Sensitive Online Shopping Info
– Examples of queries that can reveal online shopping info like customer data, suppliers, orders, credit card numbers, credit card info, etc.
Error Messages
– Really retarded error messages that say WAY too much!
Files containing juicy info
– No usernames or passwords, but interesting stuff none the less.
Network or vulnerability data
– These pages contain such things as firewall logs, honeypot logs, network information, IDS logs… all sorts of fun stuff!
Pages containing login portals
– These are login pages for various services. Consider them the front door of a website’s more sensitive functions.
Various Online Devices
– This category contains things like printers, video cameras, and all sorts of cool things found on the web with Google.
Advisories and Vulnerabilities
– These searches locate vulnerable servers. These searches are often generated from various security advisory posts, and in many cases are products or version-specific.
Google Dorks list 2019 can uncover some incredible information such as email addresses and lists, login credentials, sensitive files, website vulnerabilities, and even financial information (e.g. payment card data).
Here could see an example to understand how Google Darks password used by hackers to gain sensitive information from specific websites.
In August 2014, the United States Department of Homeland Security, Federal Bureau of Investigation and National Counterterrorism Center issued a bulletin, warning agencies to guard against Google dorking on their sites. Among the intrusion prevention measures proposed was to conduct Google dorking expeditions using likely attack parameters to discover what type of information an intruder could access.
Metadata and Google dork queries
Multiple parameters can be used in a Google dork query to search for files or information on a website or domain. For the website, https://www.governmentwebsite.gov, this string returns PDF documents with “sensitive but unclassified” anywhere in the text:
“sensitive but unclassified” filetype:pdf site:governmentwebsite.gov
A hacker that gets access to internal documents on a website can potentially also get additional sensitive information. For example, document metadata often contains more information than the author may be aware of, such as name, revision history, deletions, dates, etc.
An intruder knowledgeable about Google dorking and armed with hacking tools can access sensitive information from metadata fairly easily. That’s why it’s a good practice to remove all metadata from documents before publishing them on a website. Document sanitization can also ensure that only authorized users can access the intended information.
Common Google dork operators
A search parameter in a Google dork is applied to a search on the search engine. Google has its own query language built in, and hackers use these queries to find sensitive files, track people and discover web vulnerabilities a simple search does not reveal.
Here are some popular search parameters often used in Google dorks.
| Operator | Function | Example |
| cache: | Returns the cached version of a website | cache:techtarget.com |
| site: | Returns a list of all indexed URLs from a website or domain | site:techtarget.com |
| filetype: | Returns various kinds of files, depending on the file extension provided | filetype:pdf |
| inurl: | Searches for a specific term in the URL | inurl:register.php |
| allinurl: | Returns results whose URL contains all the specified characters | allinurl:clientarea |
| intext: | Locates webpages that contain certain characters or strings inside their text | intext:”Google Dork Query” |
| inanchor: | Searches for an exact anchor text used on any links | inanchor:”cyber attacks” |
| | | Shows all sites that contain either or both specified words in the query | hacking | Google dork |
| + | Concatenates words to detect pages using more than one specific key | hacking + Google dork |
| – | Used to avoid displaying results containing certain words | hacking – dork |
Examples of Google dorks
Here are some ways attackers use Google dorks to extract sensitive information from websites via Google.
1. To extract log files
Many kinds of error logs, access logs and application log types are available in the public Hypertext Transfer Protocol (HTTP) space of websites. Attackers can use a Google dork to find these files and any information the site may contain about its PHP version, content management system paths, admin credentials, user credentials, etc.
Example search query
allintext:password filetype:log after:2010
To prevent hackers from using such dorks to access important logs, website owners and admins must properly configure the robots.txt file.
2. To open and exploit FTP servers
Google indexes both HTTP-based and open File Transfer Protocol servers, which enables attackers to explore public FTP servers. Weak access permissions on FTP servers can result in sensitive information getting published unintentionally.
Example search query
intitle: “index of” inurl:ftp
3. To find SSH private keys and decrypt information
Secure Shell private keys decrypt information exchanged in the SSH protocol. These keys should not be shared with anyone — hence the term private. However, a hacker may use a Google dork to find and exploit the SSH private keys indexed by Google to decrypt and read sensitive information an authorized user would want to protect.
4. To find HTTP websites
Attackers can use a Google dork to discover websites or forums using the less secure HTTP protocol.
Example search query
intitle:”index of” inurl:http after:2015
They can also search for websites or specific educational or governmental organizations with the .edu or .gov domain extensions using this query:
“inurl:.”domain”/”dorks””
5. To hack into online cameras
Public closed-circuit television cameras are usually plugged in to the internet and are, therefore, a common target of hackers and cybercriminals. With Google dorking, hackers can fetch live camera webpages unrestricted by IP. Sometimes, they may also be able to control the admin panel remotely and even reconfigure the cameras.
Example search query
inurl:top.htm inurl:currenttime
Zoombombing has also become prevalent in the post-COVID-19 world. This is when a hacker disrupts a Zoom meeting using a Google dork query, like the following:
inurl:zoom.us/j and intext:scheduled for
How to prevent Google dork queries
When sensitive information must be protected, it’s crucial to prevent dorking. These steps can help:
- Implement IP-based restrictions and password authentication to protect private areas.
- Encrypt all sensitive information, like user IDs, passwords, email addresses, phone numbers, etc.
- Run vulnerability scans to find and disable Google dorks.
- Run regular dork queries to discover loopholes and sensitive information before attacks occur.
- Request the removal of sensitive content using Google Search Console.
- Hide and block sensitive content using the robots.txt file, located in the root-level website directory.
Google Dorks – Ethical Hacking and Penetration Testing for IT Professionals
Google Dorks List “Google Hacking” is mainly referred to pull the sensitive information from Google using advanced search terms that help users to search the index of a specific website, specific file type and some interesting information from unsecured Websites.
Google Dorks list 2020 can uncover some incredible information such as email addresses and lists, login credentials, sensitive files, website vulnerabilities, and even financial information (e.g. payment card data).
now for some help to all the smart people trying to better themselves and protect society here is your lesson…….
-
Username and passwords
-
Admin login pages
-
Sensitive documents
-
Govt/military data
-
Email lists
-
Bank account details
-
Vulnerable websites
-
So much more …
-
intitle:the title you are looking
-
inurl:the website URL you are targeting
-
site:
-
phonebook:
-
maps:
-
book:
-
info:
-
movie:
-
weather:
-
link:
- cited
Top 20 Google Hacking Techniques
What is a Google Dork?
A Google Dork, also known as Google Dorking or Google hacking, is a valuable resource for security researchers. For the average person, Google is just a search engine used to find text, images, videos, and news. However, in the infosec world, Google is a useful hacking tool.
How would anyone use Google to hack websites?
Well, you can’t hack sites directly using Google, but as it has tremendous web-crawling capabilities, it can index almost anything within your website, including sensitive information. This means you could be exposing too much information about your web technologies, usernames, passwords, and general vulnerabilities without even knowing it.
In other words: Google “Dorking” is the practice of using Google to find vulnerable web applications and servers by using native Google search engine capabilities.
Unless you block specific resources from your website using a robots.txt file, Google indexes all the information that is present on any website. Logically, after some time any person in the world can access that information if they know what to search for. You can also access the Google Hacking Database (GHDB) which is the full Google dork list containing all Google dorking commands.
Important note: while this information is publicly available on the Internet, and it is provided and encouraged to be used by Google on a legal basis, people with the wrong intentions could use this information to harm your online presence.
Be aware that Google also knows who you are when you perform this kind of query. For this reason and many others, it’s advised to use it only with good intentions, whether for your own research or while looking for ways to defend your website against this kind of vulnerability.
While some webmasters expose sensitive information on their own, this doesn’t mean it’s legal to take advantage of or exploit that information. If you do so you’ll be marked as a cybercriminal. It’s pretty easy to track your browsing IP, even if you’re using a VPN service. It’s not as anonymous as you think.
Before reading any further, be aware that Google will start blocking your connection if you connect from a single static IP. It will ask for captcha challenges to prevent automated queries.
Popular Google Dork operators
Google’s search engine has its own built-in query language. The following list of queries can be run to find a list of files, find information about your competition, track people, get information about SEO backlinks, build email lists, and of course, discover web vulnerabilities.
Let’s look at the most popular Google Dorks and what they do.
cache: this dork will show you the cached version of any website, e.g.cache:securitytrails.comallintext: searches for specific text contained on any web page, e.g.allintext: hacking toolsallintitle: exactly the same as allintext, but will show pages that contain titles with X characters, e.g.allintitle:"Security Companies"allinurl: it can be used to fetch results whose URL contains all the specified characters, e.g:allinurl:clientareafiletype: used to search for any kind of file extensions, for example, if you want to search for pdf files you can use:email security filetype: pdfinurl: this is exactly the same asallinurl, but it is only useful for one single keyword, e.g.inurl:adminintitle: used to search for various keywords inside the title, for example,intitle:security toolswill search for titles beginning with “security” but “tools” can be somewhere else in the page.inanchor: this is useful when you need to search for an exact anchor text used on any links, e.g.inanchor:"cyber security"intext: useful to locate pages that contain certain characters or strings inside their text, e.g.intext:"safe internet"site: will show you the full list of all indexed URLs for the specified domain and subdomain, e.g.site:securitytrails.com*: wildcard used to search pages that contain “anything” before your word, e.g.how to * a website, will return “how to…” design/create/hack, etc… “a website”.|: this is a logical operator, e.g."security" "tips"will show all the sites which contain “security” or “tips,” or both words.+: used to concatenate words, useful to detect pages that use more than one specific key, e.g.security + trails–: minus operator is used to avoiding showing results that contain certain words, e.g.security -trailswill show pages that use “security” in their text, but not those that have the word “trails.”
If you’re looking for the complete set of Google operators, you can follow this SEJ post which covers almost every known dork available today.
Google Dork examples
Let’s take a look at some practical examples of the best Google hacks. You’ll be surprised how easy is to extract private information from any source just by using Google hacking techniques.
Log files
Log files are the perfect example of how sensitive information can be found within any website. Error logs, access logs and other types of application logs are often discovered inside the public HTTP space of websites. This can help attackers find the PHP version you’re running, as well as the critical system path of your CMS or frameworks.
For this kind of dork we can combine two Google operators, allintext and filetype, for example:
allintext:username filetype:log
This will show a lot of results that include username inside all *.log files.
In the results we discovered one particular website showing an SQL error log from a database server that included critical information:
MyBB SQL Error
SQL Error: 1062 - Duplicate entry 'XXX' for key 'username'
Query:
INSERT
INTO XXX (`username`,`password`,`salt`,`loginkey`,`email`,`postnum`,`avatar`,`avatartype`,`usergroup`,`additionalgroups`,`displaygroup`,`usertitle`,`regdate`,`lastactive`,`lastvisit`,`website`,`icq`,`aim`,`yahoo`,`msn`,`birthday`,`signature`,`allownotices`,`hideemail`,`subscriptionmethod`,`receivepms`,`receivefrombuddy`,`pmnotice`,`pmnotify`,`showsigs`,`showavatars`,`showquickreply`,`showredirect`,`tpp`,`ppp`,`invisible`,`style`,`timezone`,`dstcorrection`,`threadmode`,`daysprune`,`dateformat`,`timeformat`,`regip`,`longregip`,`language`,`showcodebuttons`,`away`,`awaydate`,`returndate`,`awayreason`,`notepad`,`referrer`,`referrals`,`buddylist`,`ignorelist`,`pmfolders`,`warningpoints`,`moderateposts`,`moderationtime`,`suspendposting`,`suspensiontime`,`coppauser`,`classicpostbit`,`usernotes`)
VALUES ('XXX','XXX','XXX','XXX','XXX','0','','','5','','0','','1389074395','1389074395','1389074395','','0','','','','','','1','1','0','1','0','1','1','1','1','1','1','0','0','0','0','5.5','2','linear','0','','','XXX','-655077638','','1','0','0','0','','','0','0','','','','0','0','0','0','0','0','0','')
This Google hack example exposed the current database name, user login, password and email values to the Internet. We’ve replaced the original values with “XXX”.
Vulnerable web servers
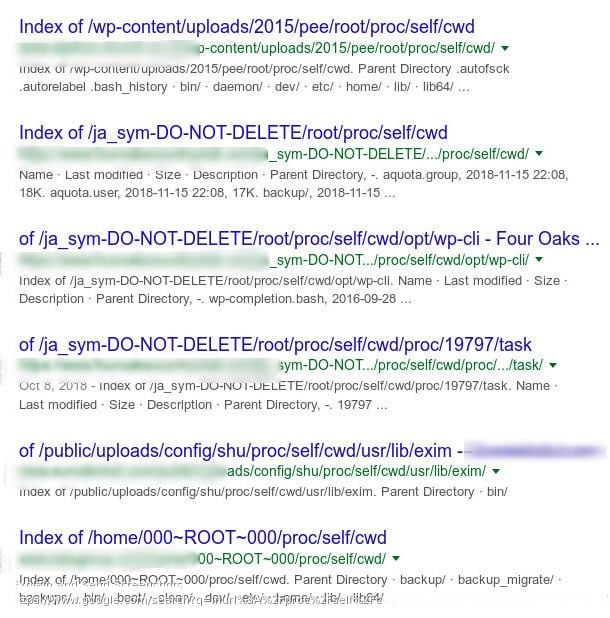
The following Google Dork can be used to detect vulnerable or hacked servers that allow appending “/proc/self/cwd/” directly to the URL of your website.
inurl:/proc/self/cwd
As you can see in the following screenshot, vulnerable server results will appear, along with their exposed directories that can be surfed from your own browser.
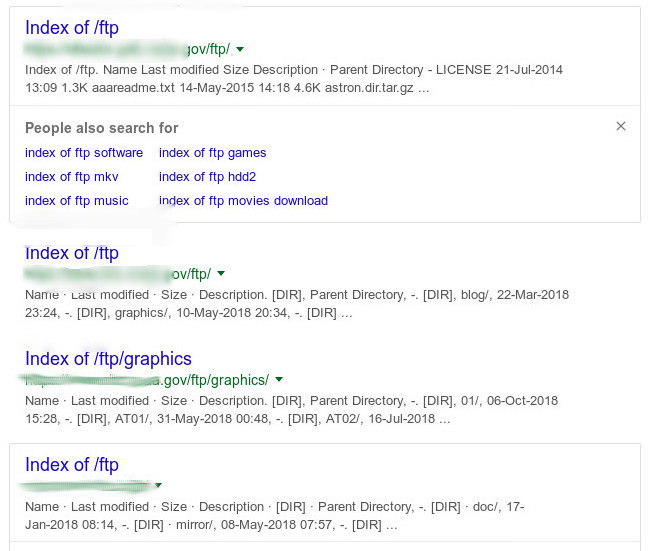
Open FTP servers
Google does not only index HTTP-based servers, it also indexes open FTP servers.
With the following dork, you’ll be able to explore public FTP servers, which can often reveal interesting things.
intitle:"index of" inurl:ftp
In this example, we found an important government server with their FTP space open. Chances are that this was on purpose — but it could also be a security issue.
ENV files
.env files are the ones used by popular web development frameworks to declare general variables and configurations for local and online dev environments.
One of the recommended practices is to move these .env files to somewhere that isn’t publicly accessible. However, as you will see, there are a lot of devs who don’t care about this and insert their .env file in the main public website directory.
As this is a critical dork we will not show you how do it; instead, we will only show you the critical results:
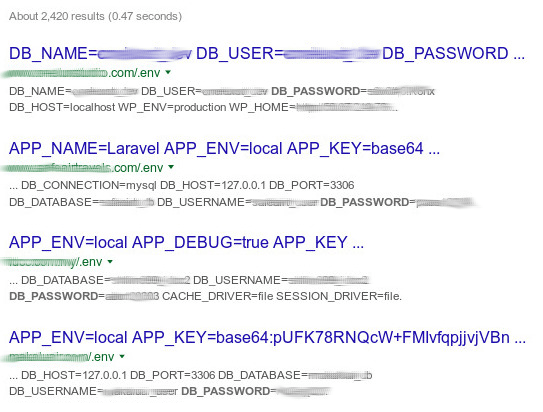
You’ll notice that unencrypted usernames, passwords and IPs are directly exposed in the search results. You don’t even need to click the links to get the database login details.
SSH private keys
SSH private keys are used to decrypt information that is exchanged in the SSH protocol. As a general security rule, private keys must always remain on the system being used to access the remote SSH server, and shouldn’t be shared with anyone.
With the following dork, you’ll be able to find SSH private keys that were indexed by uncle Google.
intitle:index.of id_rsa -id_rsa.pub
Let’s move on to another interesting SSH Dork.
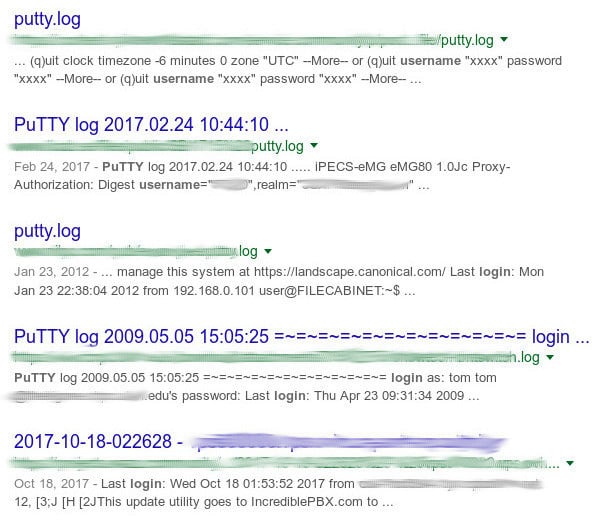
If this isn’t your lucky day, and you’re using a Windows operating system with PUTTY SSH client, remember that this program always logs the usernames of your SSH connections.
In this case, we can use a simple dork to fetch SSH usernames from PUTTY logs:
filetype:log username putty
Here’s the expected output:
Email lists
It’s pretty easy to find email lists using Google Dorks. In the following example, we are going to fetch excel files which may contain a lot of email addresses.
filetype:xls inurl:"email.xls"
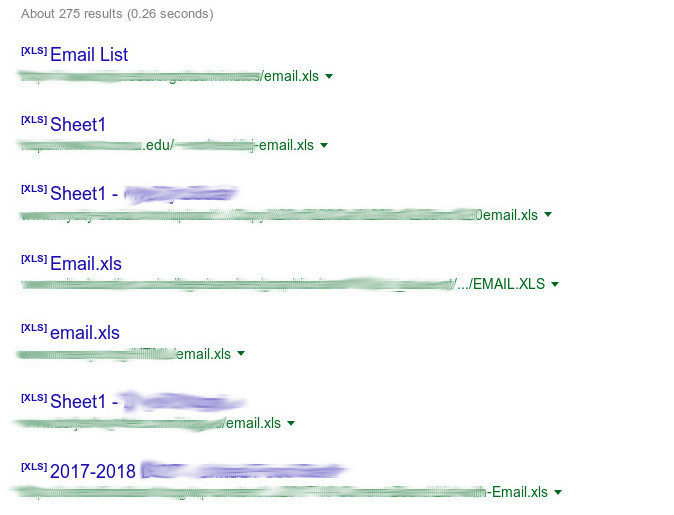
We filtered to check out only the .edu domain names and found a popular university with around 1800 emails from students and teachers.
site:.edu filetype:xls inurl:"email.xls"
Remember that the real power of Google Dorks comes from the unlimited combinations you can use. Spammers know this trick too, and use it on a daily basis to build and grow their spamming email lists.
Live cameras
Have you ever wondered if your private live camera could be watched not only by you but also by anyone on the Internet?
The following Google hacking techniques can help you fetch live camera web pages that are not restricted by IP.
Here’s the dork to fetch various IP based cameras:
inurl:top.htm inurl:currenttime
To find WebcamXP-based transmissions:
intitle:"webcamXP 5"
And another one for general live cameras:
inurl:"lvappl.htm"
There are a lot of live camera dorks that can let you watch any part of the world, live. You can find education, government, and even military cameras without IP restrictions.
If you get creative you can even do some white hat penetration testing on these cameras; you’ll be surprised at how you’re able to take control of the full admin panel remotely, and even re-configure the cameras as you like.

MP3, Movie, and PDF files
Nowadays almost no one downloads music after Spotify and Apple Music appeared on the market. However, if you’re one of those classic individuals who still download legal music, you can use this dork to find mp3 files:
intitle: index of mp3
The same applies to legal free media files or PDF documents you may need:
intitle: index of pdf intext: .mp4
Weather
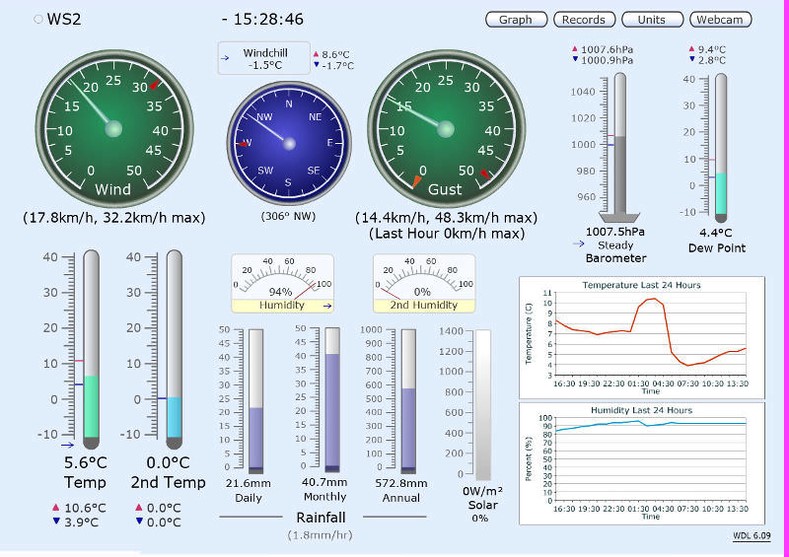
Google hacking techniques can be used to fetch any kind of information, and that includes many different types of electronic devices connected to the Internet.
In this case, we ran a dork that lets you fetch Weather Wing device transmissions. If you’re involved in meteorology stuff or merely curious, check this out:
intitle:"Weather Wing WS-2"
The output will show you several devices connected around the world, which share weather details such as wind direction, temperature, humidity and more.
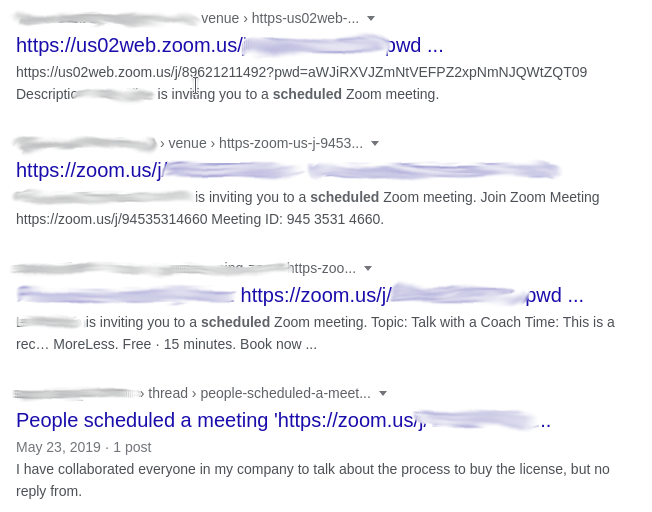
Zoom videos
“Zoom-bombing” became a popular means of disrupting online meetings in 2020 during the initial lockdown. The company has since placed some restrictions to make it harder to find/disrupt Zoom meetings, but long as a URL is shared, a Zoom meeting can still be found:
inurl:zoom.us/j and intext:scheduled for
The only drawback to this is the speed at which Google indexes a website. By the time a site is indexed, the Zoom meeting might already be over.
SQL dumps
Misconfigured databases are one way of finding exposed data. Another way is to look for SQL dumps that are stored on servers and accessible via a domain/IP.
Sometimes, these dumps appear on sites through incorrect backup mechanisms used by site admins who store backups on web servers (assuming that they aren’t indexed by Google). To find a zipped SQL file, we use:
"index of" "database.sql.zip"
We’ve omitted screenshots to avoid exposing any possible data breaches.
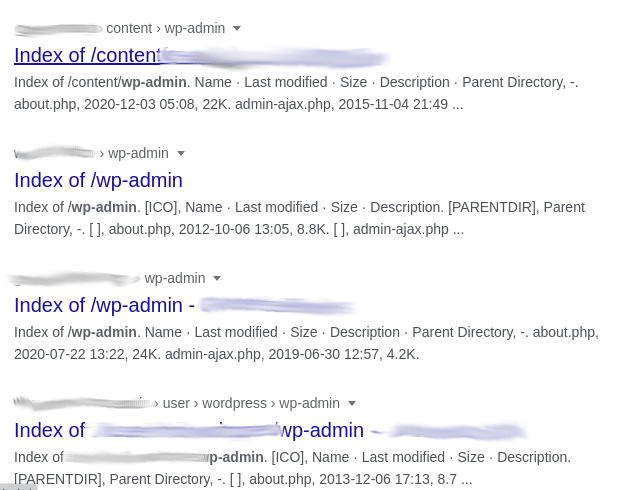
WordPress Admin
The view on whether to obfuscate your WordPress login page has arguments on both sides. Some researchers say it’s unnecessary and using tools like a web application firewall (WAF) can prevent attacks much better than obfuscation would.
Finding WP Admin login pages is not too difficult with a dork:
intitle:"Index of" wp-admin
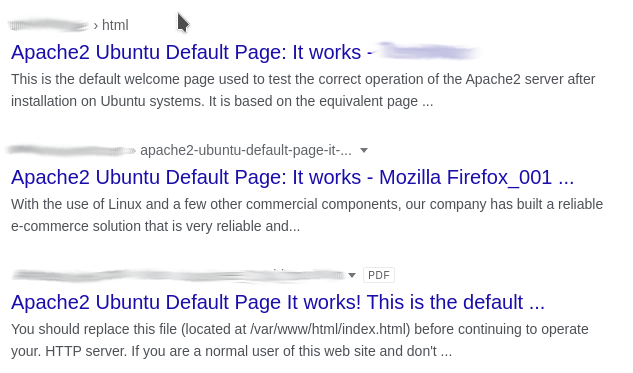
Apache2
This can be considered a subset of “vulnerable web servers” mentioned above, but we’re discussing Apache2 specifically because:
- LAMP (Linux, Apache, MySQL, PHP) is a popular stack for hosted apps/websites
- These Apache servers could be misconfigured/forgotten or in some stage of being setup, making them great targets for botnets
Find Apache2 web pages with the following dork:
intitle:"Apache2 Ubuntu Default Page: It works"
phpMyAdmin
Another risky yet frequently discovered tool on LAMP servers is phpMyAdmin software. This tool is another method of compromising data, as phpMyAdmin is used for the administration of MySQL over the web. The dork to use is:
"Index of" inurl:phpmyadmin
JIRA/Kibana
Google dorks can also be used to find web applications hosting important enterprise data (via JIRA or Kibana).
inurl:Dashboard.jspa intext:"Atlassian Jira Project Management Software"
inurl:app/kibana intext:Loading Kibana
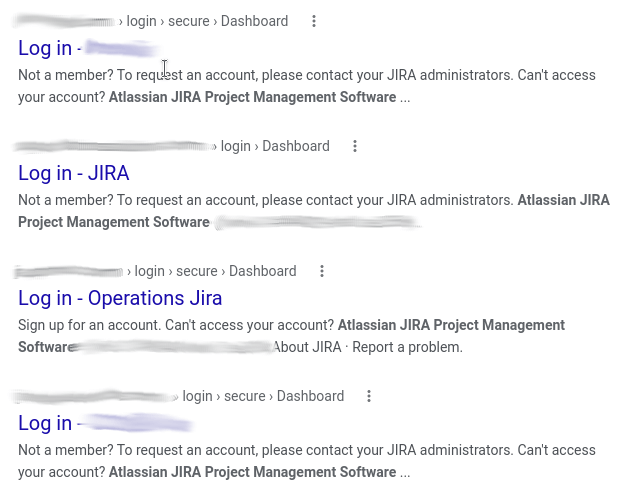
An easier way to find JIRA instances is to use a tool like SurfaceBrowser™, which can identify subdomains as well as the applications on those subdomains (besides JIRA, there are many other applications).
cPanel password reset
Another dork that can be used as the first step in reconnaissance is to hosted cPanels and then exploit various weaknesses in password resets to take over the cPanel (along with all the websites hosted on it). The dork for this purpose is:
inurl:_cpanel/forgotpwd
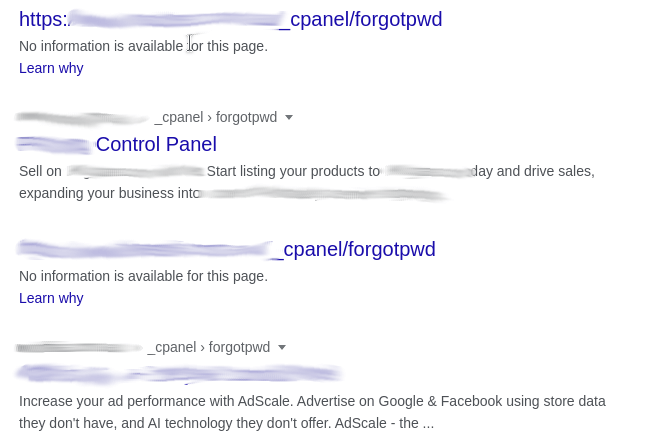
Government documents
Sensitive government documents are the last thing that should be exposed on the internet, but with dorks they aren’t too hard to find, as shown below:
allintitle: restricted filetype:doc site:gov
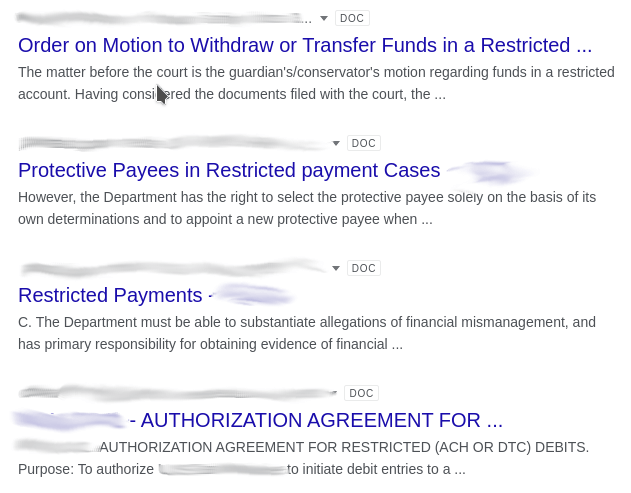
Preventing Google Dorks
There are a lot of ways to avoid falling into the hands of a Google Dork.
These measures are suggested to prevent your sensitive information from being indexed by search engines.
- Protect private areas with a user and password authentication and also by using IP-based restrictions.
- Encrypt your sensitive information (user, passwords, credit cards, emails, addresses, IP addresses, phone numbers, etc).
- Run regular vulnerability scans against your site, these usually already use popular Google Dorks queries and can be pretty effective in detecting the most common ones.
- Run regular dork queries against your own website to see if you can find any important information before the bad guys do. You can find a great list of popular dorks at the Exploit DB Dorks database.
- If you find sensitive content exposed, request its removal by using Google Search Console.
- Block sensitive content by using a robots.txt file located in your root-level website directory.
Using robots.txt configurations to prevent Google Dorking
One of the best ways to prevent Google dorks is by using a robots.txt file. Let’s see some practical examples.
The following configuration will deny all crawling from any directory within your website, which is pretty useful for private access websites that don’t rely on publicly-indexable Internet content.
User-agent: *
Disallow: /
You can also block specific directories to be excepted from web crawling. If you have an /admin area and you need to protect it, just place this code inside:
User-agent: *
Disallow: /admin/
This will also protect all the subdirectories inside.
Restrict access to specific files:
User-agent: *
Disallow: /privatearea/file.htm
Restrict access to dynamic URLs that contain ‘?’ symbol
User-agent: *
Disallow: /*?
To restrict access to specific file extensions you can use:
User-agent: *
Disallow: /*.php$/
In this case, all access to .php files will be denied.
our Cyber Source
Find Passwords in Exposed Log Files with Google Dorks
Posted by source
You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it’s possible to find files that are exposed accidentally and contain critical information for anyone to see.
The advanced application of Google search operators is Google Dorking — using search operators to hunt for specific vulnerable devices through targeted search strings. If we assume that Google has indexed most devices accidentally exposed to the internet, we can use the text we know appears in their login or administrative pages to find them.
What Kinds of Things Do Dorks Connect to the Internet?
You would be amazed. Everything from the pool controller of Yachts in the ocean to configuration interfaces for critical systems is connected to the internet by well-meaning people with the assumption that no one will ever find them.
So how could this happen to you? Imagine getting a new security camera that provides the ability to watch it on your phone whenever you want. You set it up, connect it to your Wi-Fi, and download an app that asks for you to sign in. After that, you can access your camera from anywhere!
What’s going on in the background isn’t so simple. The camera calls a Chinese server and streams video in real-time, allowing you to log in by accessing the video feed hosted on the server in China from your phone. That server may require no password to access the feed from your webcam, making your camera accessible to anyone who searches for text contained in the viewing page of the camera.
Unfortunately, Google is ruthlessly effective at hunting down any devices on the internet running HTTP and HTTPS servers. Because most of these devices host a server to configure them, it means that many things that aren’t supposed to be on Google end up there.
Which Dorks Are the Most Powerful?
By far, the most severe kind of exposed file we can find is one that leaks the credentials to user accounts or the entire service itself. Usually, this will happen in one of two ways. In the first, a server or other service is set up incorrectly and exposes its administrative logs to the internet. When passwords are changed, or a user fails to log in correctly, these logs can leak the credentials being used to the internet.
The other way this happens is when configuration files that contain the same information are exposed. These are files that are supposed to be internal but are often leave critical information out in the open. Either one of these mistakes can cause the entire service to be taken over by an attacker who happens to chance upon the information.
We’ll be using Google dorks to find not only these files, but also things like file transfer servers that may contain interesting information, email lists, and my personal favourite, exposed webcams.
What You’ll Need
To follow along, you’ll need a browser with internet access. The beautiful thing about using Google dorks is that we can use tools accessible by nearly anyone to find vulnerable systems.
Once you have a browser open, navigate to Google.com, and we can get started.
Step 1. Finding FTP Servers & Websites Using HTTP
To start, we’ll use the following dork to search for file transfer servers published sometime this year. Searching for these servers can allow us to find files that are supposed to be internal, but were unknowingly made public.
intitle:"index of" inurl:ftp after:2018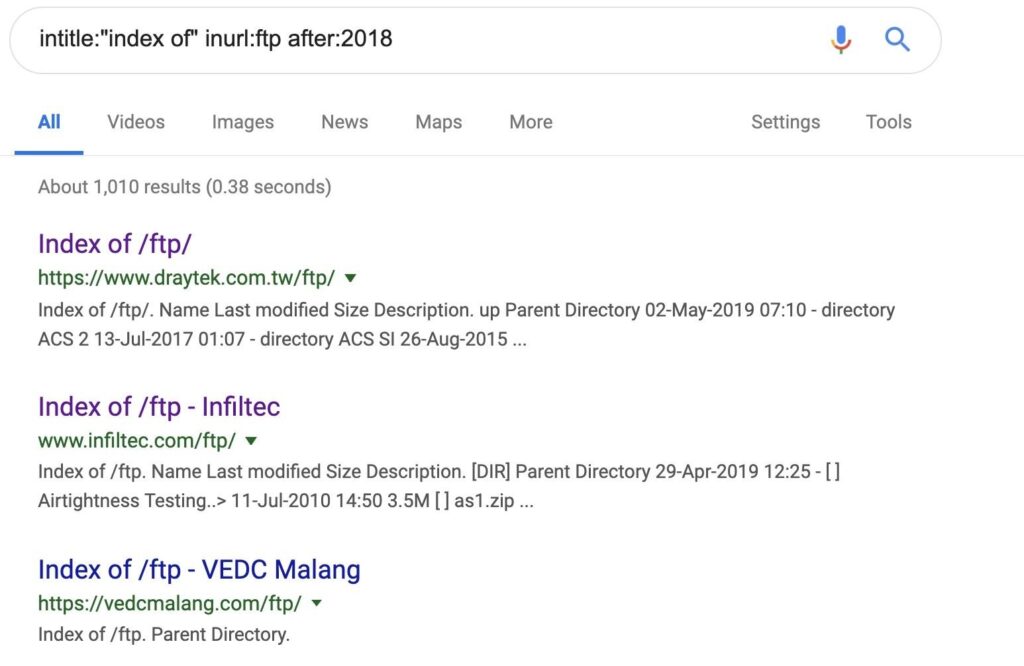
These servers become public because the index file of their FTP server is the kind of data that Google loves to scan — a fact people tend to forget. Google’s scanning leads to a complete list of all the files contained within the server being searchable on Google.
If we want to find insecure webpages still using HTTP to poke at, we can modify the command slightly to do so by changing the “ftp” to “http” and re-running the search.
intitle:"index of" inurl:http after:2018Searching that string should produce a list of lots and lots of websites using HTTP, ready to be attacked. But if we’re looking for a specific type of site, we can go even further.
If we want to start attacking some easy targets, we can be more specific and search for online forms still using HTTP by changing the text in the search title.
intitle:"forum" inurl:http after:2018We can keep adding search operators like AND inurl:”registration” to get more specific and hunt down the registration pages of insecure form websites.
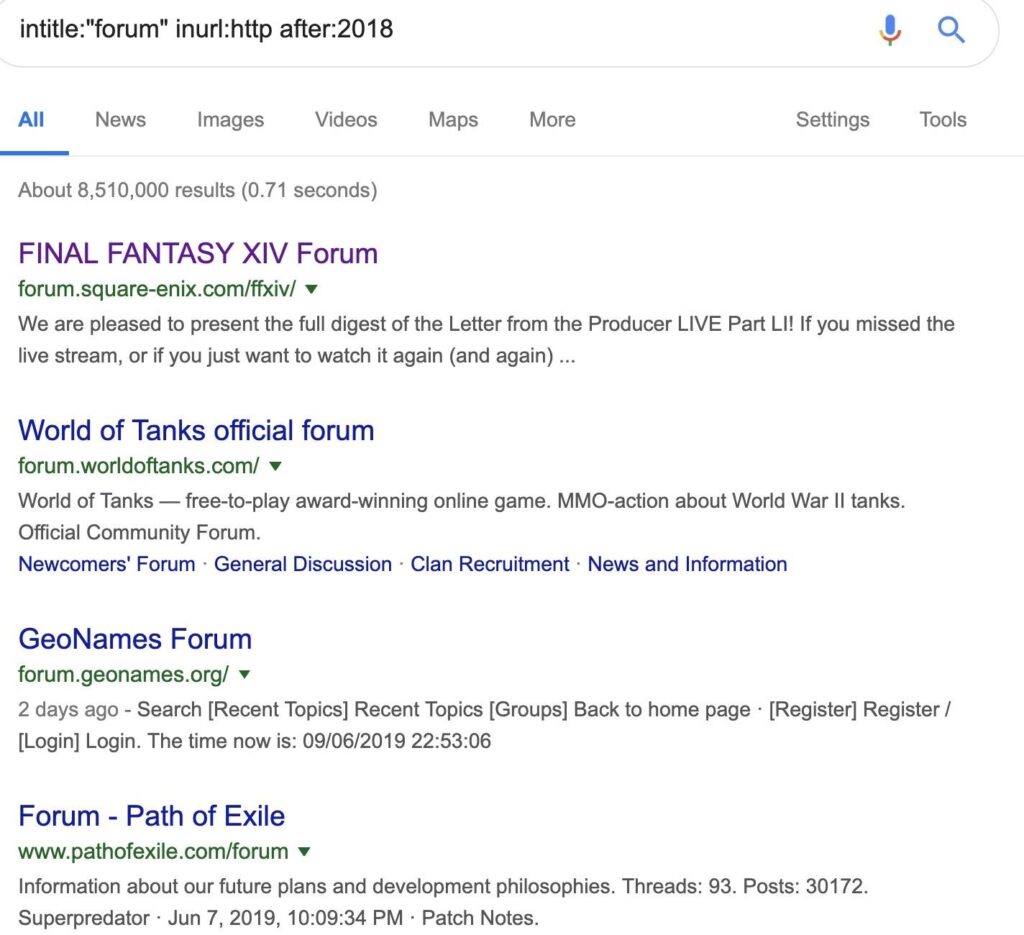
Here you can see we’ve found a list of vulnerable online forums using HTTP.
Step 1Find Log Files with Passwords
The next step will be to search for files of the .LOG type. Searching for LOG files will allow us to look for clues about what the credentials to the system or various user or admin accounts might be.
The dork we’ll be using to do this is as follows.
allintext:password filetype:log after:2018When searching for current log files exposed to the internet, we find this almost immediately.
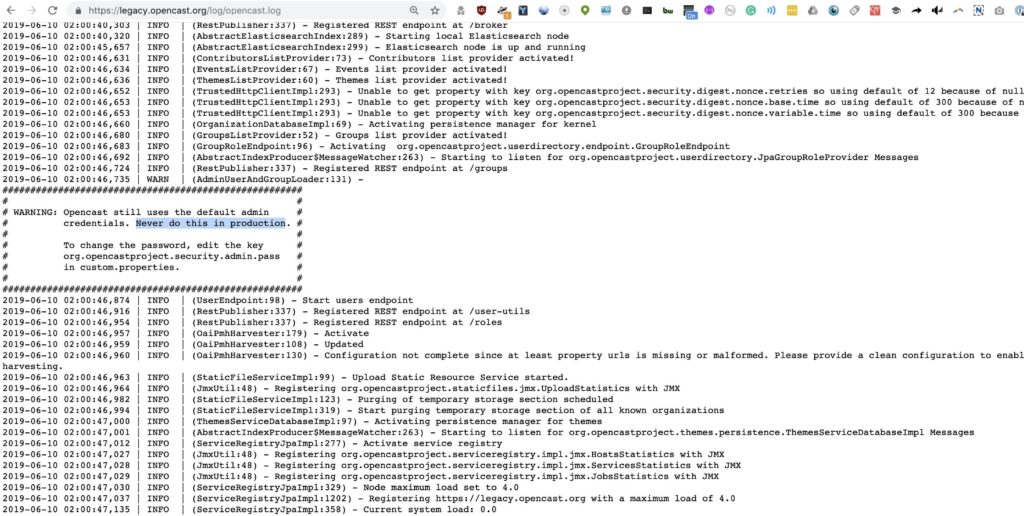
This log states that the password is the default one, which takes just a simple Google search of the OpenCast Project website to discover. With one search, we’ve possibly found the credentials to this system without hacking anything at all.
Step 2. Find Configuration Files with Passwords
Configuration files should not be public pretty much ever, and .ENV files are great examples of this. If we search for .ENV files that contain a string for the database password, we instantly find the password to this database we’ve discovered.
filetype:env "DB_PASSWORD" after:2018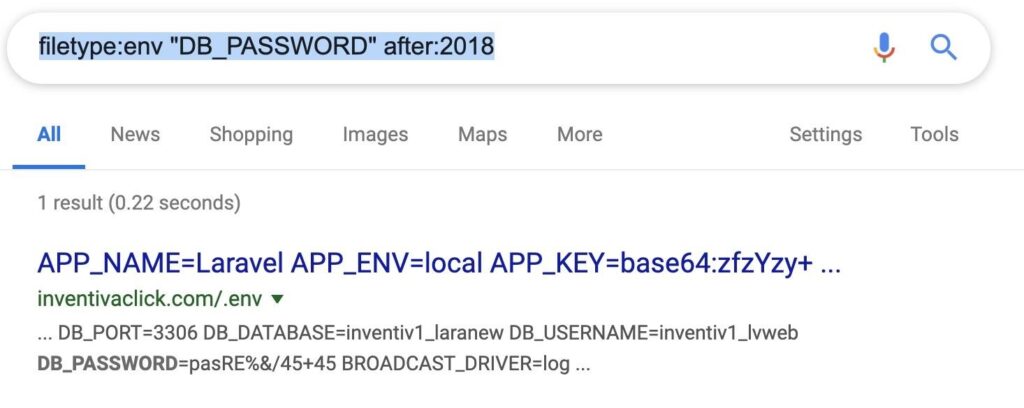
If we remove the after:2018 we can see older log files also exposing services to the internet.
Step 3. Find Email Lists
Email lists are a great way of scraping email addresses and trying to find information on corporate or school targets. These lists are frequently exposed by companies or schools that are trying to organize email lists for their members.
To find them, we’ll be looking for spreadsheet .XLS file type with the string “email.xls” in the URL.
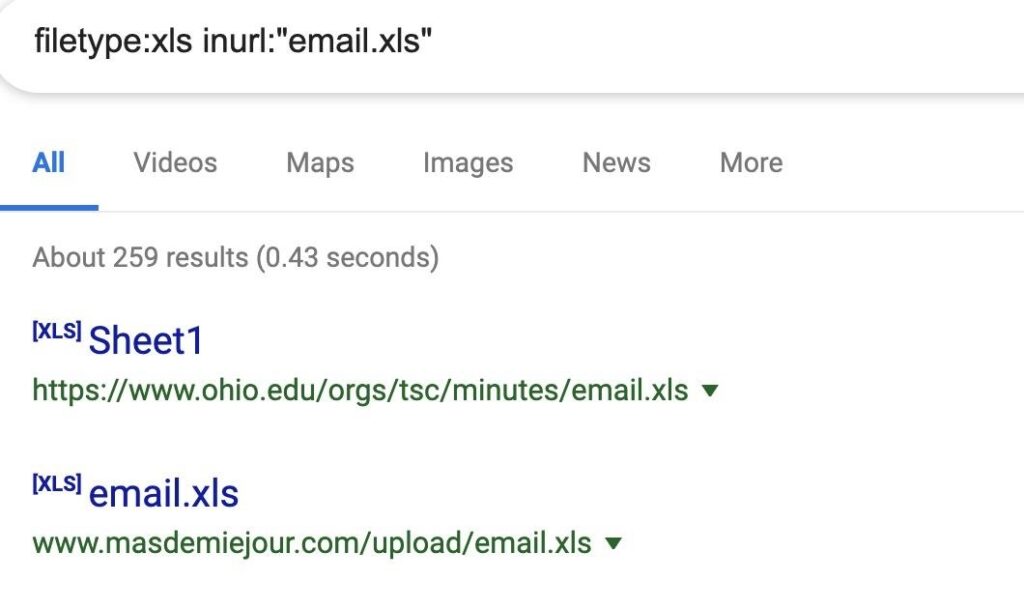
While these results are useful, be careful not to download any file without first considering if it’s a honeypot. Many people will take popular dorks and then leave a server hosting a file that looks vulnerable but could instead contain malware.
Step 4. Find Open Cameras
Finally, if you thought Shodan was the only service that can find weird open cameras, you were dead wrong. Camera login and viewing pages are usually HTTP, meaning Google is happy to index them and provide them for viewing if you know the right search string.
One common format for webcam strings is searching for “top.htm” in the URL with the current time and date included. You’ll find a lot of results this way.
inurl:top.htm inurl:currenttime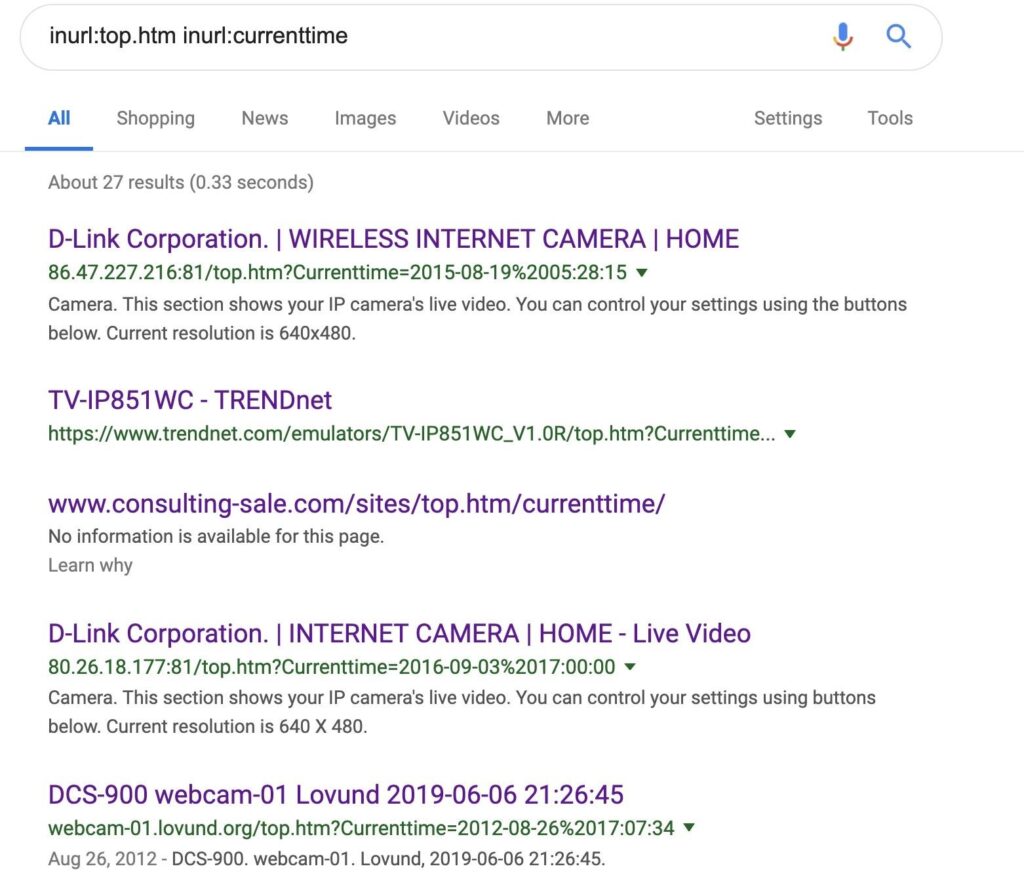
The first result is a webcam that appears to be the Windows XP background from another angle in Belmullet, Ireland.

Another dork for cameras that produces outstanding results searches for a common live-view page hosted on routers.
inurl:"lvappl.htm"Using this dork, I was able to locate the best camera of all, the birdcam1.
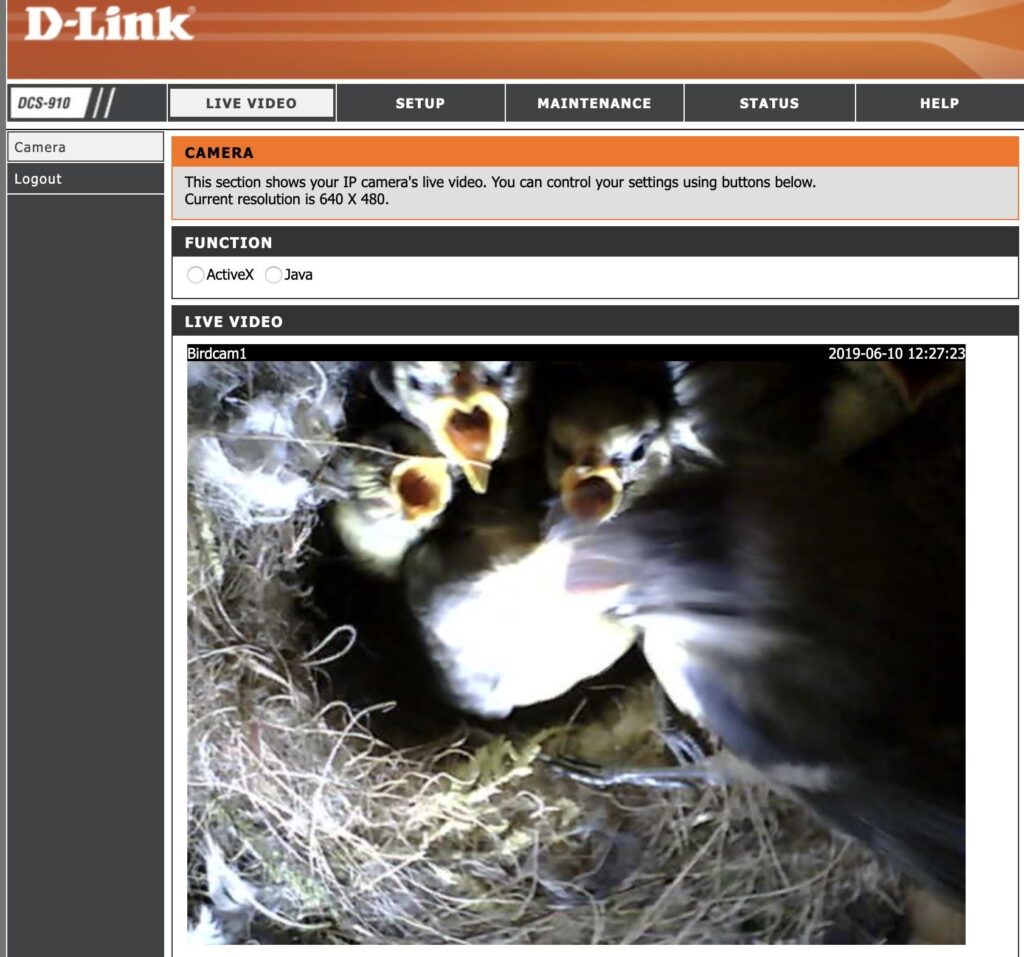
Please do not hack the bird cam, but feel free to enjoy it here. Many other cameras are available, though all are less interesting than birdcam1.

Many cameras also monitor inside factories or industrial areas.
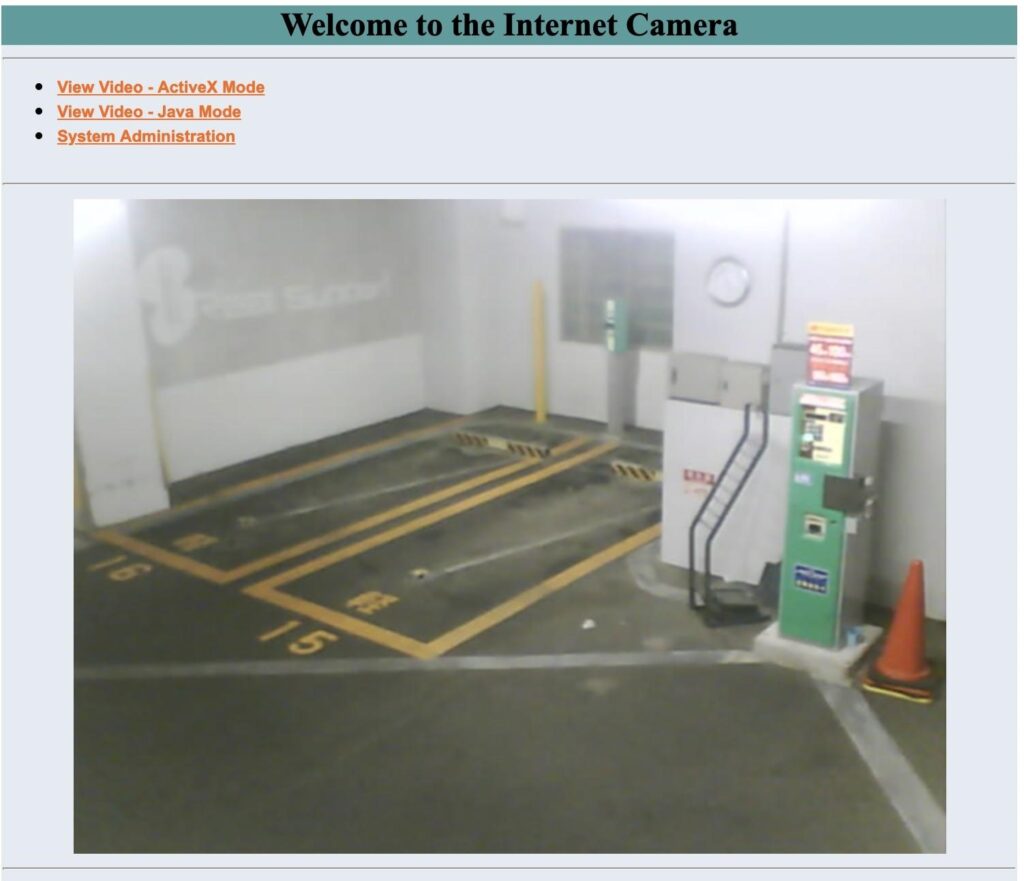
While you can view the cameras I demonstrated without a password; many dorks look for webcam login pages that have a well-known default password. This tactic, while illegal, allows easy access to many webcams not intended for public viewing.
Google Dorks Allow Easy Hacking of Exposed Services
Thanks to the way Google indexes nearly everything connected to the internet that offers a web interface, there’s no shortage of misconfigured services that leave critical elements exposed to the internet. Make sure you don’t log in to any of these services even if the password is exposed, as this could get you into trouble because you don’t have permission. If you have a service online, it’s smart to run a few common dorks on your domains to see what turns up, just in case you’ve accidentally left something exposed that a hacker might find useful.
Most Important Google Dorks list
_news/news.php?id=
-site:php.net -"The PHP Group" inurl:source inurl:url ext:pHp
!Host=*.* intext:enc_UserPassword=* ext:pcf
?action=
?cat=
?id=
?intitle:index.of? mp3 artist-name-here
?intitle:index.of? mp3 name
?page=
?pagerequested=
?pid=
" -FrontPage-" ext:pwd inurl:(service | authors | administrators | users)
": vBulletin Version 1.1.5"
"# -FrontPage-" ext:pwd inurl:(service | authors | administrators | users) "# -FrontPage-" inurl:service.pwd
"#mysql dump" filetype:sql
"#mysql dump" filetype:sql 21232f297a57a5a743894a0e4a801fc3
"A syntax error has occurred" filetype:ihtml
"About Mac OS Personal Web Sharing"
"access denied for user" "using password"
"allow_call_time_pass_reference" "PATH_INFO"
"An illegal character has been found in the statement" -"previous message"
"apricot - admin" 00h
"ASP.NET_SessionId" "data source="
"AutoCreate=TRUE password=*"
"bp blog admin" intitle:login | intitle:admin -site:johnny.ihackstuff.com
"Can't connect to local" intitle:warning
"Certificate Practice Statement" inurl:(PDF | DOC)
"Chatologica MetaSearch" "stack tracking:"
"Chatologica MetaSearch" "stack tracking"
"detected an internal error [IBM][CLI Driver][DB2/6000]"
"Duclassified" -site:duware.com "DUware All Rights reserved"
"duclassmate" -site:duware.com
"Dudirectory" -site:duware.com
"dudownload" -site:duware.com
"Dumping data for table"
"DUpaypal" -site:duware.com
"Elite Forum Version *.*"
"Emergisoft web applications are a part of our"
"Error Diagnostic Information" intitle:"Error Occurred While"
"error found handling the request" cocoon filetype:xml
"Establishing a secure Integrated Lights Out session with" OR intitle:"Data Frame - Browser not HTTP 1.1 compatible" OR intitle:"HP Integrated Lights-
"Fatal error: Call to undefined function" -reply -the -next
"ftp://" "www.eastgame.net"
"Host Vulnerability Summary Report"
"HostingAccelerator" intitle:"login" +"Username" -"news" -demo
"html allowed" guestbook
"HTTP_FROM=googlebot" googlebot.com "Server_Software="
"http://*:*@www" domainname
"iCONECT 4.1 :: Login"
"IMail Server Web Messaging" intitle:login
"Incorrect syntax near"
"Index of /" +.htaccess
"Index of /" +passwd
"Index of /" +password.txt
"Index of /admin"
"Index of /backup"
"Index of /mail"
"Index Of /network" "last modified"
"Index of /password"
"index of /private" -site:net -site:com -site:org
"index of /private" site:mil
"Index of" / "chat/logs"
"index of/" "ws_ftp.ini" "parent directory"
"inspanel" intitle:"login" -"cannot" "Login ID" -site:inspediumsoft.com
"Installed Objects Scanner" inurl:default.asp
"Internal Server Error" "server at"
"intitle:3300 Integrated Communications Platform" inurl:main.htm
"intitle:index of"
"Invision Power Board Database Error"
"Link Department"
"liveice configuration file" ext:cfg
"liveice configuration file" ext:cfg -site:sourceforge.net
"Login - Sun Cobalt RaQ"
"login prompt" inurl:GM.cgi
"Login to Usermin" inurl:20000
"MacHTTP" filetype:log inurl:machttp.log
"Mecury Version" "Infastructure Group"
"Microsoft (R) Windows * (TM) Version * DrWtsn32 Copyright (C)" ext:log
"Microsoft ® Windows * ™ Version * DrWtsn32 Copyright ©" ext:log
"Microsoft CRM : Unsupported Browser Version"
"More Info about MetaCart Free"
"Most Submitted Forms and s?ri?ts" "this section"
"Most Submitted Forms and Scripts" "this section"
"mysql dump" filetype:sql
"mySQL error with query"
"Network Host Assessment Report" "Internet Scanner"
"Network Vulnerability Assessment Report"
"not for distribution" confidential
"not for public release" -.edu -.gov -.mil
"OPENSRS Domain Management" inurl:manage.cgi
"ORA-00921: unexpected end of SQL command"
"ORA-00933: SQL command not properly ended"
"ORA-00936: missing expression"
"ORA-12541: TNS:no listener" intitle:"error occurred"
"Output produced by SysWatch *"
"parent directory " /appz/ -xxx -html -htm -php -shtml -opendivx -md5 -md5sums
"parent directory " DVDRip -xxx -html -htm -php -shtml -opendivx -md5 -md5sums
"parent directory " Gamez -xxx -html -htm -php -shtml -opendivx -md5 -md5sums
"parent directory " MP3 -xxx -html -htm -php -shtml -opendivx -md5 -md5sums
"parent directory " Name of Singer or album -xxx -html -htm -php -shtml -opendivx -md5 -md5sums
"parent directory "Xvid -xxx -html -htm -php -shtml -opendivx -md5 -md5sums
"parent directory" +proftpdpasswd
"Parse error: parse error, unexpected T_VARIABLE" "on line" filetype:php
"pcANYWHERE EXPRESS Java Client"
"phone * * *" "address *" "e-mail" intitle:"curriculum vitae"
"Phorum Admin" "Database Connection" inurl:forum inurl:admin
"phpMyAdmin MySQL-Dump" "INSERT INTO" -"the"
"phpMyAdmin MySQL-Dump" filetype:txt
"phpMyAdmin" "running on" inurl:"main.php"
"Please authenticate yourself to get access to the management interface"
"please log in"
"Please login with admin pass" -"leak" -sourceforge
"PostgreSQL query failed: ERROR: parser: parse error"
"powered | performed by Beyond Security's Automated Scanning" -kazaa -example
"Powered by mnoGoSearch - free web search engine software"
"powered by openbsd" +"powered by apache"
"Powered by UebiMiau" -site:sourceforge.net
"produced by getstats"
"Request Details" "Control Tree" "Server Variables"
"robots.txt" "Disallow:" filetype:txt
"Running in Child mode"
"Select a database to view" intitle:"filemaker pro"
"set up the administrator user" inurl:pivot
"sets mode: +k"
"sets mode: +p"
"sets mode: +s"
"Shadow Security Scanner performed a vulnerability assessment"
"site info for" "Enter Admin Password"
"SnortSnarf alert page"
"SQL Server Driver][SQL Server]Line 1: Incorrect syntax near"
"SquirrelMail version" "By the SquirrelMail development Team"
"Supplied argument is not a valid MySQL result resource"
"Supplied argument is not a valid PostgreSQL result"
"Syntax error in query expression " -the
"SysCP - login"
"Thank you for your order" +receipt
"The following report contains confidential information" vulnerability -search
"The s?ri?t whose uid is " "is not allowed to access"
"The script whose uid is " "is not allowed to access"
"The statistics were last upd?t?d" "Daily"-microsoft.com
"There are no Administrators Accounts" inurl:admin.php -mysql_fetch_row
"There seems to have been a problem with the" " Please try again by clicking the Refresh button in your web browser."
"This is a restricted Access Server" "Javas?ri?t Not Enabled!"|"Messenger Express" -edu -ac
"This is a Shareaza Node"
"this proxy is working fine!" "enter *" "URL***" * visit
"This report lists" "identified by Internet Scanner"
"This report was generated by WebLog"
"This section is for Administrators only. If you are an administrator then please"
"This summary was generated by wwwstat"
"Traffic Analysis for" "RMON Port * on unit *"
"ttawlogin.cgi/?action="
"Unable to jump to row" "on MySQL result index" "on line"
"Unclosed quotation mark before the character string"
"Version Info" "Boot Version" "Internet Settings"
"VHCS Pro ver" -demo
"VNC Desktop" inurl:5800
"Warning: Bad arguments to (join|implode) () in" "on line" -help -forum
"Warning: Cannot modify header information - headers already sent"
"Warning: Division by zero in" "on line" -forum
"Warning: mysql_connect(): Access denied for user: '*@*" "on line" -help -forum
"Warning: mysql_query()" "invalid query"
"Warning: pg_connect(): Unable to connect to PostgreSQL server: FATAL"
"Warning: Supplied argument is not a valid File-Handle resource in"
"Warning:" "failed to open stream: HTTP request failed" "on line"
"Warning:" "SAFE MODE Restriction in effect." "The s?ri?t whose uid is" "is not allowed to access owned by uid 0 in" "on line"
"Warning:" "SAFE MODE Restriction in effect." "The script whose uid is" "is not allowed to access owned by uid 0 in" "on line"
"Web File Browser" "Use regular expression"
"Web-Based Management" "Please input password to login" -inurl:johnny.ihackstuff.com
"WebExplorer Server - Login" "Welcome to WebExplorer Server"
"WebSTAR Mail - Please Log In"
"Welcome to Administration" "General" "Local Domains" "SMTP Authentication" inurl:admin
"Welcome to Intranet"
"Welcome to PHP-Nuke" congratulations
"Welcome to the Prestige Web-Based Configurator"
"xampp/phpinfo
"YaBB SE Dev Team"
"you can now password" | "this is a special page only seen by you. your profile visitors" inurl:imchaos
"You have an error in your SQL syntax near"
"You have requested access to a restricted area of our website. Please authenticate yourself to continue."
"You have requested to access the management functions" -.edu
"Your password is * Remember this for later use"
"your password is" filetype:log
( filetype:mail | filetype:eml | filetype:mbox | filetype:mbx ) intext:password|subject
("Indexed.By"|"Monitored.By") hAcxFtpScan
((inurl:ifgraph "Page generated at") OR ("This page was built using ifgraph"))
(intitle:"Please login - Forums
(intitle:"PRTG Traffic Grapher" inurl:"allsensors")|(intitle:"PRTG Traffic Grapher - Monitoring Results")
(intitle:"rymo Login")|(intext:"Welcome to rymo") -family
(intitle:"WmSC e-Cart Administration")|(intitle:"WebMyStyle e-Cart Administration")
(intitle:WebStatistica inurl:main.php) | (intitle:"WebSTATISTICA server") -inurl:statsoft -inurl:statsoftsa -inurl:statsoftinc.com -edu -software -rob
(inurl:"ars/cgi-bin/arweb?O=0" | inurl:arweb.jsp) -site:remedy.com -site:mil
(inurl:"robot.txt" | inurl:"robots.txt" ) intext:disallow filetype:txt
(inurl:/shop.cgi/page=) | (inurl:/shop.pl/page=)
[WFClient] Password= filetype:ica
*.php?include=
*.php?secc=
********.php?cid=
********s_in_area.php?area_id=
***zine/board.php?board=
*inc*.php?adresa=
*inc*.php?base_dir=
*inc*.php?body=
*inc*.php?c=
*inc*.php?category=
*inc*.php?doshow=
*inc*.php?ev=
*inc*.php?get=
*inc*.php?i=
*inc*.php?inc=
*inc*.php?include=
*inc*.php?j=
*inc*.php?k=
*inc*.php?ki=
*inc*.php?left=
*inc*.php?m=
*inc*.php?menu=
*inc*.php?modo=
*inc*.php?open=
*inc*.php?pg=
*inc*.php?rub=
*inc*.php?sivu=
*inc*.php?start=
*inc*.php?str=
*inc*.php?to=
*inc*.php?type=
*inc*.php?y=
/addpost_newpoll.php?addpoll=preview&thispath=
/admin_modules/admin_module_deldir.inc.php?config[path_src_include]=
/administrator/components/com_serverstat/install.serverstat.php?mosConfig_absolute_path=
/administrator/components/com_uhp/uhp_config.php?mosConfig_absolute_path=
/app/common/lib/codeBeautifier/Beautifier/Core.php?BEAUT_PATH=
/bz/squito/photolist.inc.php?photoroot=
/class.mysql.php?path_to_bt_dir=
/classes.php?LOCAL_PATH=
/classes/adodbt/sql.php?classes_dir=
/classified_right.php?language_dir=
/coin_includes/constants.php?_CCFG[_PKG_PATH_INCL]=
/components/com_cpg/cpg.php?mosConfig_absolute_path=
/components/com_extended_registration/registration_detailed.inc.php?mosConfig_absolute_path=
/components/com_facileforms/facileforms.frame.php?ff_compath=
/components/com_mtree/Savant2/Savant2_Plugin_textarea.php?mosConfig_absolute_path=
/components/com_rsgallery/rsgallery.html.php?mosConfig_absolute_path=
/components/com_smf/smf.php?mosConfig_absolute_path=
/components/com_zoom/includes/database.php?mosConfig_absolute_path=
/contrib/yabbse/poc.php?poc_root_path=
/embed/day.php?path=
/extensions/moblog/moblog_lib.php?basedir=
/functions.php?include_path=
/header.php?abspath=
/include/footer.inc.php?_AMLconfig[cfg_serverpath]=
/include/main.php?config[search_disp]=true&include_dir=
/include/write.php?dir=
/includes/dbal.php?eqdkp_root_path=
/includes/functions_portal.php?phpbb_root_path=
/includes/kb_constants.php?module_root_path=
/includes/orderSuccess.inc.php?glob=1&cart_order_id=1&glob[rootDir]=
/index.php?_REQUEST=&_REQUEST[option]=com_content&_REQUEST[Itemid]=1&GLOBALS=&mosConfig_absolute_path=
/jscript.php?my_ms[root]=
/login.php?dir=
/main.php?sayfa=
/mcf.php?content=
/modules/4nAlbum/public/displayCategory.php?basepath=
/modules/agendax/addevent.inc.php?agendax_path=
/modules/coppermine/include/init.inc.php?CPG_M_DIR=
/modules/Forums/admin/admin_styles.php?phpbb_root_path=
/modules/My_eGallery/public/displayCategory.php?basepath=
/modules/newbb_plus/class/forumpollrenderer.php?bbPath[path]=
/modules/PNphpBB2/includes/functions_admin.php?phpbb_root_path=
/modules/TotalCalendar/about.php?inc_dir=
/modules/vwar/admin/admin.php?vwar_root=
/modules/vwar/admin/admin.php?vwar_root=index.php?loc=
/modules/xgallery/upgrade_album.php?GALLERY_BASEDIR=
/modules/xoopsgallery/upgrade_album.php?GALLERY_BASEDIR=
/photoalb/lib/static/header.php?set_menu=
/phpopenchat/contrib/yabbse/poc.php?sourcedir=
/popup_window.php?site_isp_root=
/ppa/inc/functions.inc.php?config[ppa_root_path]=
/skin/zero_vote/error.php?dir=
/sources/functions.php?CONFIG[main_path]=
/sources/join.php?FORM[url]=owned&CONFIG[captcha]=1&CONFIG[path]=
/sources/template.php?CONFIG[main_path]=
/spid/lang/lang.php?lang_path=
/squirrelcart/cart_content.php?cart_isp_root=
/squito/photolist.inc.php?photoroot=
/surveys/survey.inc.php?path=
/tags.php?BBCodeFile=
/templates/headline_temp.php?nst_inc=
/tools/send_reminders.php?includedir=
/tools/send_reminders.php?includedir= allinurl:day.php?date=
/yabbse/Sources/Packages.php?sourcedir=
/zipndownload.php?PP_PATH=
4images Administration Control Panel
94FBR "ADOBE PHOTOSHOP"
about_us.php?id=
about.php?cartID=
aboutbook.php?id=
aboutchiangmai/details.php?id=
aboutprinter.shtml
abroad/page.php?cid=
accinfo.php?cartId=
acclogin.php?cartID=
add_cart.php?num=
add-to-cart.php?ID=
add.php?bookid=
addcart.php?
addItem.php
addToCart.php?idProduct=
addtomylist.php?ProdId=
admin.php?page=
admin/doeditconfig.php?thispath=../includes&config[path]=
admin/index.php?o=
adminEditProductFields.php?intProdID=
administrator/components/com_a6mambocredits/admin.a6mambocredits.php?mosConfig_live_site=
administrator/components/com_comprofiler/plugin.class.php?mosConfig_absolute_path=
administrator/components/com_comprofiler/plugin.class.php?mosConfig_absolute_path= /tools/send_reminders.php?includedir= allinurl:day.php?date=
administrator/components/com_cropimage/admin.cropcanvas.php?cropimagedir=
administrator/components/com_cropimage/admin.cropcanvas.php?cropimagedir=modules/My_eGallery/index.php?basepath=
administrator/components/com_linkdirectory/toolbar.linkdirectory.html.php?mosConfig_absolute_path=
administrator/components/com_mgm/help.mgm.php?mosConfig_absolute_path=
administrator/components/com_peoplebook/param.peoplebook.php?mosConfig_absolute_path=
administrator/components/com_remository/admin.remository.php?mosConfig_absolute_path=
administrator/components/com_remository/admin.remository.php?mosConfig_absolute_path= /tags.php?BBCodeFile=
administrator/components/com_webring/admin.webring.docs.php?component_dir=
advSearch_h.php?idCategory=
affiliate-agreement.cfm?storeid=
affiliate.php?ID=
affiliates.php?id=
AIM buddy lists
akocomments.php?mosConfig_absolute_path=
aktuelles/meldungen-detail.php?id=
aktuelles/veranstaltungen/detail.php?id=
al_initialize.php?alpath=
allintitle: "index of/admin"
allintitle: "index of/root"
allintitle: restricted filetype :mail
allintitle: restricted filetype:doc site:gov
allintitle: sensitive filetype:doc
allintitle:.."Test page for Apache Installation.."
allintitle:"Network Camera NetworkCamera"
allintitle:"Welcome to the Cyclades"
allintitle:*.php?filename=*
allintitle:*.php?logon=*
allintitle:*.php?page=*
allintitle:admin.php
allinurl: admin mdb
allinurl:.br/index.php?loc=
allinurl:".r{}_vti_cnf/"
allinurl:"exchange/logon.asp"
allinurl:"index.php" "site=sglinks"
allinurl:*.php?txtCodiInfo=
allinurl:/examples/jsp/snp/snoop.jsp
allinurl:admin mdb
allinurl:auth_user_file.txt
allinurl:cdkey.txt
allinurl:control/multiview
allinurl:install/install.php
allinurl:intranet admin
allinurl:servlet/SnoopServlet
allinurl:wps/portal/ login
An unexpected token "END-OF-STATEMENT" was found
Analysis Console for Incident Databases
ancillary.php?ID=
announce.php?id=
answer/default.php?pollID=
AnyBoard" intitle:"If you are a new user:" intext:"Forum
AnyBoard" inurl:gochat -edu
archive.php?id=
archive/get.php?message_id=
art.php?id=
article_preview.php?id=
article.php?id=
article.php?ID=
articlecategory.php?id=
articles.php?id=
artikelinfo.php?id=
artist_art.php?id=
ASP.login_aspx "ASP.NET_SessionId"
auction/item.php?id=
auth_user_file.txt
authorDetails.php?bookID=
avatar.php?page=
avd_start.php?avd=
band_info.php?id=
base.php?*[*]*=
base.php?abre=
base.php?adresa=
base.php?base_dir=
base.php?basepath=
base.php?body=
base.php?category=
base.php?chapter=
base.php?choix=
base.php?cont=
base.php?disp=
base.php?doshow=
base.php?ev=
base.php?eval=
base.php?filepath=
base.php?home=
base.php?id=
base.php?incl=
base.php?include=
base.php?ir=
base.php?itemnav=
base.php?k=
base.php?ki=
base.php?l=
base.php?lang=
base.php?link=
base.php?loc=
base.php?mid=
base.php?middle=
base.php?middlePart=
base.php?module=
base.php?name=
base.php?numero=
base.php?oldal=
base.php?opcion=
base.php?pa=
base.php?pag=
base.php?pageweb=
base.php?panel=
base.php?path=
base.php?phpbb_root_path=
base.php?play=
base.php?pname=
base.php?rub=
base.php?seccion=
base.php?second=
base.php?seite=
base.php?sekce=
base.php?sivu=
base.php?str=
base.php?subject=
base.php?t=
base.php?texto=
base.php?to=
base.php?v=
base.php?var=
base.php?w=
basket.php?id=
bayer/dtnews.php?id=
bb_usage_stats/include/bb_usage_stats.php?phpbb_root_path=
bbs/bbsView.php?id=
bbs/view.php?no=
beitrag_D.php?id=
beitrag_F.php?id=
bid/topic.php?TopicID=
big.php?pathtotemplate=
blank.php?abre=
blank.php?action=
blank.php?base_dir=
blank.php?basepath=
blank.php?body=
blank.php?category=
blank.php?channel=
blank.php?corpo=
blank.php?destino=
blank.php?dir=
blank.php?filepath=
blank.php?get=
blank.php?goFile=
blank.php?goto=
blank.php?h=
blank.php?header=
blank.php?id=
blank.php?in=
blank.php?incl=
blank.php?ir=
blank.php?itemnav=
blank.php?j=
blank.php?ki=
blank.php?lang=
blank.php?left=
blank.php?link=
blank.php?loader=
blank.php?menu=
blank.php?mod=
blank.php?name=
blank.php?o=
blank.php?oldal=
blank.php?open=
blank.php?OpenPage=
blank.php?pa=
blank.php?page=
blank.php?pagina=
blank.php?panel=
blank.php?path=
blank.php?phpbb_root_path=
blank.php?pname=
blank.php?pollname=
blank.php?pr=
blank.php?pre=
blank.php?pref=
blank.php?qry=
blank.php?read=
blank.php?ref=
blank.php?rub=
blank.php?section=
blank.php?sivu=
blank.php?sp=
blank.php?strona=
blank.php?subject=
blank.php?t=
blank.php?url=
blank.php?var=
blank.php?where=
blank.php?xlink=
blank.php?z=
blog_detail.php?id=
blog.php?blog=
blog/index.php?idBlog=
board_view.html?id=
board_view.php?s_board_id=
board/board.html?table=
board/kboard.php?board=
board/read.php?tid=
board/showthread.php?t=
board/view_temp.php?table=
board/view.php?no=
boardView.php?bbs=
book_detail.php?BookID=
book_list.php?bookid=
book_view.php?bookid=
book.html?isbn=
Book.php?bookID=
book.php?ID=
book.php?id=
book.php?ISBN=
book.php?isbn=
book/bookcover.php?bookid=
BookDetails.php?ID=
bookDetails.php?id=
bookmark/mybook/bookmark.php?bookPageNo=
bookpage.php?id=
books.php?id=
books/book.php?proj_nr=
bookview.php?id=
bp_ncom.php?bnrep=
bpac/calendar/event.php?id=
brand.php?id=
browse_item_details.php
Browse_Item_Details.php?Store_Id=
browse.php?catid=
browse/book.php?journalID=
browsepr.php?pr=
buy.php?
buy.php?bookid=
buy.php?category=
bycategory.php?id=
calendar/event.php?id=
camera linksys inurl:main.cgi
Canon Webview netcams
cardinfo.php?card=
cart_additem.php?id=
cart_validate.php?id=
cart.php?action=
cart.php?cart_id=
cart.php?id=
cart/addToCart.php?cid=
cart/product.php?productid=
cartadd.php?id=
cat.php?cat_id=
cat.php?iCat=
cat/?catid=
catalog_item.php?ID=
catalog_main.php?catid=
catalog.php
catalog.php?CatalogID=
catalog/main.php?cat_id=
catalog/product.php?cat_id=
catalog/product.php?pid=
categories.php?cat=
category_list.php?id=
category.php
category.php?c=
category.php?catid=
category.php?CID=
category.php?cid=
Category.php?cid=
category.php?id_category=
category.php?id=
categorydisplay.php?catid=
cats.php?cat=
cbmer/congres/page.php?LAN=
cei/cedb/projdetail.php?projID=
cemetery.php?id=
CGI:IRC Login
cgiirc.conf
channel_id=
channel/channel-layout.php?objId=
chappies.php?id=
checkout_confirmed.php?order_id=
checkout.php?cartid=
checkout.php?UserID=
checkout1.php?cartid=
clan_page.php?cid=
clanek.php4?id=
classes/adodbt/sql.php?classes_dir=
classifieds/detail.php?siteid=
classifieds/showproduct.php?product=
cloudbank/detail.php?ID=
club.php?cid=
clubpage.php?id=
Coldfusion Error Pages
collectionitem.php?id=
colourpointeducational/more_details.php?id=
comersus_listCategoriesAndProducts.php?idCategory=
comersus_optEmailToFriendForm.php?idProduct=
comersus_optReviewReadExec.php?idProduct=
comersus_viewItem.php?idProduct=
Comersus.mdb database
comments_form.php?ID=
comments.php?id=
communique_detail.php?id=
community/calendar-event-fr.php?id=
components/com_artlinks/artlinks.dispnew.php?mosConfig_absolute_path=
components/com_cpg/cpg.php?mosConfig_absolute_path=
components/com_extcalendar/admin_events.php?CONFIG_EXT[LANGUAGES_DIR]=
components/com_extended_registration/registration_detailed.inc.php?mosConfig_absolute_path=
components/com_forum/download.php?phpbb_root_path=
components/com_galleria/galleria.html.php?mosConfig_absolute_path=
components/com_mtree/Savant2/Savant2_Plugin_stylesheet.php?mosConfig_absolute_path=
components/com_performs/performs.php?mosConfig_absolute_path=
components/com_phpshop/toolbar.phpshop.html.php?mosConfig_absolute_path=
components/com_rsgallery/rsgallery.html.php?mosConfig_absolute_path=
components/com_simpleboard/image_upload.php?sbp=
Computer Science.php?id=
confidential site:mil
config.php
config.php?_CCFG[_PKG_PATH_DBSE]=
ConnectionTest.java filetype:html
constructies/product.php?id=
contact.php?cartId=
contacts ext:wml
contenido.php?sec=
content.php?arti_id=
content.php?categoryId=
content.php?cID=
content.php?cid=
content.php?cont_title=
content.php?id
content.php?id=
content.php?ID=
content.php?p=
content.php?page=
content.php?PID=
content/conference_register.php?ID=
content/detail.php?id=
content/index.php?id=
content/pages/index.php?id_cat=
content/programme.php?ID=
content/view.php?id=
coppercop/theme.php?THEME_DIR=
corporate/newsreleases_more.php?id=
county-facts/diary/vcsgen.php?id=
cps/rde/xchg/tm/hs.xsl/liens_detail.html?lnkId=
cryolab/content.php?cid=
csc/news-details.php?cat=
customer/board.htm?mode=
customer/home.php?cat=
customerService.php?****ID1=
CuteNews" "2003..2005 CutePHP"
data filetype:mdb -site:gov -site:mil
db.php?path_local=
db/CART/product_details.php?product_id=
de/content.php?page_id=
deal_coupon.php?cat_id=
debate-detail.php?id=
declaration_more.php?decl_id=
default.php?*root*=
default.php?abre=
default.php?base_dir=
default.php?basepath=
default.php?body=
default.php?catID=
default.php?channel=
default.php?chapter=
default.php?choix=
default.php?cmd=
default.php?cont=
default.php?cPath=
default.php?destino=
default.php?e=
default.php?eval=
default.php?f=
default.php?goto=
default.php?header=
default.php?inc=
default.php?incl=
default.php?include=
default.php?index=
default.php?ir=
default.php?itemnav=
default.php?k=
default.php?ki=
default.php?l=
default.php?left=
default.php?load=
default.php?loader=
default.php?loc=
default.php?m=
default.php?menu=
default.php?menue=
default.php?mid=
default.php?mod=
default.php?module=
default.php?n=
default.php?name=
default.php?nivel=
default.php?oldal=
default.php?opcion=
default.php?option=
default.php?p=
default.php?pa=
default.php?pag=
default.php?page=
default.php?pageweb=
default.php?panel=
default.php?param=
default.php?play=
default.php?pr=
default.php?pre=
default.php?read=
default.php?ref=
default.php?rub=
default.php?secao=
default.php?secc=
default.php?seccion=
default.php?seite=
default.php?showpage=
default.php?sivu=
default.php?sp=
default.php?str=
default.php?strona=
default.php?t=
default.php?thispage=
default.php?TID=
default.php?tipo=
default.php?to=
default.php?type=
default.php?v=
default.php?var=
default.php?x=
default.php?y=
description.php?bookid=
designcenter/item.php?id=
detail.php?id=
detail.php?ID=
detail.php?item_id=
detail.php?prodid=
detail.php?prodID=
detail.php?siteid=
detailedbook.php?isbn=
details.php?BookID=
details.php?id=
details.php?Press_Release_ID=
details.php?prodId=
details.php?ProdID=
details.php?prodID=
details.php?Product_ID=
details.php?Service_ID=
directory/contenu.php?id_cat=
discussions/10/9/?CategoryID=
display_item.php?id=
display_page.php?id=
display.php?ID=
displayArticleB.php?id=
displayproducts.php
displayrange.php?rangeid=
docDetail.aspx?chnum=
down*.php?action=
down*.php?addr=
down*.php?channel=
down*.php?choix=
down*.php?cmd=
down*.php?corpo=
down*.php?disp=
down*.php?doshow=
down*.php?ev=
down*.php?filepath=
down*.php?goFile=
down*.php?home=
down*.php?in=
down*.php?inc=
down*.php?incl=
down*.php?include=
down*.php?ir=
down*.php?lang=
down*.php?left=
down*.php?nivel=
down*.php?oldal=
down*.php?open=
down*.php?OpenPage=
down*.php?pa=
down*.php?pag=
down*.php?pageweb=
down*.php?param=
down*.php?path=
down*.php?pg=
down*.php?phpbb_root_path=
down*.php?pollname=
down*.php?pr=
down*.php?pre=
down*.php?qry=
down*.php?r=
down*.php?read=
down*.php?s=
down*.php?second=
down*.php?section=
down*.php?seite=
down*.php?showpage=
down*.php?sp=
down*.php?strona=
down*.php?subject=
down*.php?t=
down*.php?texto=
down*.php?to=
down*.php?u=
down*.php?url=
down*.php?v=
down*.php?where=
down*.php?x=
down*.php?z=
download.php?id=
downloads_info.php?id=
downloads.php?id=
downloads/category.php?c=
downloads/shambler.php?id=
downloadTrial.php?intProdID=
Duclassified" -site:duware.com "DUware All Rights reserved"
duclassmate" -site:duware.com
Dudirectory" -site:duware.com
dudownload" -site:duware.com
DUpaypal" -site:duware.com
DWMail" password intitle:dwmail
e_board/modifyform.html?code=
edatabase/home.php?cat=
edition.php?area_id=
education/content.php?page=
eggdrop filetype:user user
Elite Forum Version *.*"
els_/product/product.php?id=
emailproduct.php?itemid=
emailToFriend.php?idProduct=
en/main.php?id=
en/news/fullnews.php?newsid=
en/publications.php?id=
enable password | secret "current configuration" -intext:the
enc/content.php?Home_Path=
eng_board/view.php?T****=
eng/rgboard/view.php?&bbs_id=
english/board/view****.php?code=
english/fonction/print.php?id=
english/print.php?id=
english/publicproducts.php?groupid=
enter.php?a=
enter.php?abre=
enter.php?addr=
enter.php?b=
enter.php?base_dir=
enter.php?body=
enter.php?chapter=
enter.php?cmd=
enter.php?content=
enter.php?e=
enter.php?ev=
enter.php?get=
enter.php?go=
enter.php?goto=
enter.php?home=
enter.php?id=
enter.php?incl=
enter.php?include=
enter.php?index=
enter.php?ir=
enter.php?itemnav=
enter.php?lang=
enter.php?left=
enter.php?link=
enter.php?loader=
enter.php?menue=
enter.php?mid=
enter.php?middle=
enter.php?mod=
enter.php?module=
enter.php?name=
enter.php?numero=
enter.php?open=
enter.php?pa=
enter.php?page=
enter.php?pagina=
enter.php?panel=
enter.php?path=
enter.php?pg=
enter.php?phpbb_root_path=
enter.php?play=
enter.php?pname=
enter.php?pr=
enter.php?pref=
enter.php?qry=
enter.php?r=
enter.php?read=
enter.php?ref=
enter.php?s=
enter.php?sec=
enter.php?second=
enter.php?seite=
enter.php?sivu=
enter.php?sp=
enter.php?start=
enter.php?str=
enter.php?strona=
enter.php?subject=
enter.php?texto=
enter.php?thispage=
enter.php?type=
enter.php?viewpage=
enter.php?w=
enter.php?y=
etc (index.of)
event_details.php?id=
event_info.php?p=
event.php?id=
events?id=
events.php?ID=
events/detail.php?ID=
events/event_detail.php?id=
events/event.php?id=
events/event.php?ID=
events/index.php?id=
events/unique_event.php?ID=
exhibition_overview.php?id=
exhibitions/detail.php?id=
exported email addresses
ext:(doc | pdf | xls | txt | ps | rtf | odt | sxw | psw | ppt | pps | xml) (intext:confidential salary | intext:"budget approved") inurl:confidential
ext:asa | ext:bak intext:uid intext:pwd -"uid..pwd" database | server | dsn
ext:asp inurl:pathto.asp
ext:ccm ccm -catacomb
ext:CDX CDX
ext:cfg radius.cfg
ext:cgi intext:"nrg-" " This web page was created on "
ext:cgi intitle:"control panel" "enter your owner password to continue!"
ext:cgi inurl:editcgi.cgi inurl:file=
ext:conf inurl:rsyncd.conf -cvs -man
ext:conf NoCatAuth -cvs
ext:dat bpk.dat
ext:gho gho
ext:ics ics
ext:inc "pwd=" "UID="
ext:ini eudora.ini
ext:ini intext:env.ini
ext:ini Version=4.0.0.4 password
ext:jbf jbf
ext:ldif ldif
ext:log "Software: Microsoft Internet Information Services *.*"
ext:mdb inurl:*.mdb inurl:fpdb shop.mdb
ext:nsf nsf -gov -mil
ext:passwd -intext:the -sample -example
ext:plist filetype:plist inurl:bookmarks.plist
ext:pqi pqi -database
ext:pwd inurl:(service | authors | administrators | users) "# -FrontPage-"
ext:reg "username=*" putty
ext:txt "Final encryption key"
ext:txt inurl:dxdiag
ext:txt inurl:unattend.txt
ext:vmdk vmdk
ext:vmx vmx
ext:yml database inurl:config
ez Publish administration
faq_list.php?id=
faq.php?cartID=
faq2.php?id=
faqs.php?id=
fatcat/home.php?view=
feature.php?id=
features/view.php?id=
feedback.php?title=
fellows.php?id=
FernandFaerie/index.php?c=
fiche_spectacle.php?id=
Fichier contenant des informations sur le r?seau :
file.php?action=
file.php?basepath=
file.php?body=
file.php?channel=
file.php?chapter=
file.php?choix=
file.php?cmd=
file.php?cont=
file.php?corpo=
file.php?disp=
file.php?doshow=
file.php?ev=
file.php?eval=
file.php?get=
file.php?id=
file.php?inc=
file.php?incl=
file.php?include=
file.php?index=
file.php?ir=
file.php?ki=
file.php?left=
file.php?load=
file.php?loader=
file.php?middle=
file.php?modo=
file.php?n=
file.php?nivel=
file.php?numero=
file.php?oldal=
file.php?pagina=
file.php?param=
file.php?pg=
file.php?play=
file.php?pollname=
file.php?pref=
file.php?q=
file.php?qry=
file.php?ref=
file.php?seccion=
file.php?second=
file.php?showpage=
file.php?sivu=
file.php?sp=
file.php?start=
file.php?strona=
file.php?texto=
file.php?to=
file.php?type=
file.php?url=
file.php?var=
file.php?viewpage=
file.php?where=
file.php?y=
filemanager.php?delete=
filetype:asp "Custom Error Message" Category Source
filetype:asp + "[ODBC SQL"
filetype:ASP ASP
filetype:asp DBQ=" * Server.MapPath("*.mdb")
filetype:ASPX ASPX
filetype:bak createobject sa
filetype:bak inurl:"htaccess|passwd|shadow|htusers"
filetype:bkf bkf
filetype:blt "buddylist"
filetype:blt blt +intext:screenname
filetype:BML BML
filetype:cfg auto_inst.cfg
filetype:cfg ks intext:rootpw -sample -test -howto
filetype:cfg mrtg "target
filetype:cfm "cfapplication name" password
filetype:CFM CFM
filetype:CGI CGI
filetype:cgi inurl:"fileman.cgi"
filetype:cgi inurl:"Web_Store.cgi"
filetype:cnf inurl:_vti_pvt access.cnf
filetype:conf inurl:firewall -intitle:cvs
filetype:conf inurl:psybnc.conf "USER.PASS="
filetype:conf oekakibbs
filetype:conf slapd.conf
filetype:config config intext:appSettings "User ID"
filetype:config web.config -CVS
filetype:ctt Contact
filetype:ctt ctt messenger
filetype:dat "password.dat
filetype:dat "password.dat"
filetype:dat inurl:Sites.dat
filetype:dat wand.dat
filetype:DIFF DIFF
filetype:DLL DLL
filetype:DOC DOC
filetype:eml eml +intext:"Subject" +intext:"From" +intext:"To"
filetype:FCGI FCGI
filetype:fp3 fp3
filetype:fp5 fp5 -site:gov -site:mil -"cvs log"
filetype:fp7 fp7
filetype:HTM HTM
filetype:HTML HTML
filetype:inc dbconn
filetype:inc intext:mysql_connect
filetype:inc mysql_connect OR mysql_pconnect
filetype:inf inurl:capolicy.inf
filetype:inf sysprep
filetype:ini inurl:"serv-u.ini"
filetype:ini inurl:flashFXP.ini
filetype:ini ServUDaemon
filetype:ini wcx_ftp
filetype:ini ws_ftp pwd
filetype:JHTML JHTML
filetype:JSP JSP
filetype:ldb admin
filetype:lic lic intext:key
filetype:log "PHP Parse error" | "PHP Warning" | "PHP Error"
filetype:log "See `ipsec --copyright"
filetype:log access.log -CVS
filetype:log cron.log
filetype:log intext:"ConnectionManager2"
filetype:log inurl:"password.log"
filetype:log inurl:password.log
filetype:mbx mbx intext:Subject
filetype:mdb inurl:users.mdb
filetype:mdb wwforum
filetype:MV MV
filetype:myd myd -CVS
filetype:netrc password
filetype:ns1 ns1
filetype:ora ora
filetype:ora tnsnames
filetype:pass pass intext:userid
filetype:pdb pdb backup (Pilot | Pluckerdb)
filetype:pdf "Assessment Report" nessus
filetype:PDF PDF
filetype:pem intext:private
filetype:php inurl:"logging.php" "Discuz" error
filetype:php inurl:"webeditor.php"
filetype:php inurl:index inurl:phpicalendar -site:sourceforge.net
filetype:php inurl:ipinfo.php "Distributed Intrusion Detection System"
filetype:php inurl:nqt intext:"Network Query Tool"
filetype:php inurl:vAuthenticate
filetype:PHP PHP
filetype:PHP3 PHP3
filetype:PHP4 PHP4
filetype:PHTML PHTML
filetype:pl "Download: SuSE Linux Openexchange Server CA"
filetype:pl intitle:"Ultraboard Setup"
filetype:PL PL
filetype:pot inurl:john.pot
filetype:PPT PPT
filetype:properties inurl:db intext:password
filetype:PS ps
filetype:PS PS
filetype:pst inurl:"outlook.pst"
filetype:pst pst -from -to -date
filetype:pwd service
filetype:pwl pwl
filetype:qbb qbb
filetype:QBW qbw
filetype:r2w r2w
filetype:rdp rdp
filetype:reg "Terminal Server Client"
filetype:reg reg +intext:"defaultusername" +intext:"defaultpassword"
filetype:reg reg +intext:â? WINVNC3â?
filetype:reg reg HKEY_CURRENT_USER SSHHOSTKEYS
filetype:SHTML SHTML
filetype:sql "insert into" (pass|passwd|password)
filetype:sql ("values * MD5" | "values * password" | "values * encrypt")
filetype:sql +"IDENTIFIED BY" -cvs
filetype:sql password
filetype:STM STM
filetype:SWF SWF
filetype:TXT TXT
filetype:url +inurl:"ftp://" +inurl:";@"
filetype:vcs vcs
filetype:vsd vsd network -samples -examples
filetype:wab wab
filetype:xls -site:gov inurl:contact
filetype:xls inurl:"email.xls"
filetype:xls username password email
filetype:XLS XLS
Financial spreadsheets: finance.xls
Financial spreadsheets: finances.xls
folder.php?id=
forum_bds.php?num=
forum.php?act=
forum/profile.php?id=
forum/showProfile.php?id=
fr/commande-liste-categorie.php?panier=
free_board/board_view.html?page=
freedownload.php?bookid=
front/bin/forumview.phtml?bbcode=
frontend/category.php?id_category=
fshstatistic/index.php?PID=
fullDisplay.php?item=
FullStory.php?Id=
galerie.php?cid=
Gallery in configuration mode
gallery.php?*[*]*=
gallery.php?abre=
gallery.php?action=
gallery.php?addr=
gallery.php?base_dir=
gallery.php?basepath=
gallery.php?chapter=
gallery.php?cont=
gallery.php?corpo=
gallery.php?disp=
gallery.php?ev=
gallery.php?eval=
gallery.php?filepath=
gallery.php?get=
gallery.php?go=
gallery.php?h=
gallery.php?id=
gallery.php?index=
gallery.php?itemnav=
gallery.php?ki=
gallery.php?left=
gallery.php?loader=
gallery.php?menu=
gallery.php?menue=
gallery.php?mid=
gallery.php?mod=
gallery.php?module=
gallery.php?my=
gallery.php?name=
gallery.php?nivel=
gallery.php?oldal=
gallery.php?open=
gallery.php?option=
gallery.php?pag=
gallery.php?page=
gallery.php?pageweb=
gallery.php?panel=
gallery.php?param=
gallery.php?pg=
gallery.php?phpbb_root_path=
gallery.php?pname=
gallery.php?pollname=
gallery.php?pre=
gallery.php?pref=
gallery.php?qry=
gallery.php?redirect=
gallery.php?ref=
gallery.php?rub=
gallery.php?sec=
gallery.php?secao=
gallery.php?seccion=
gallery.php?seite=
gallery.php?showpage=
gallery.php?sivu=
gallery.php?sp=
gallery.php?strona=
gallery.php?thispage=
gallery.php?tipo=
gallery.php?to=
gallery.php?url=
gallery.php?var=
gallery.php?viewpage=
gallery.php?where=
gallery.php?xlink=
gallery.php?y=
gallery/detail.php?ID=
gallery/gallery.php?id=
gallerysort.php?iid=
game.php?id=
games.php?id=
Ganglia Cluster Reports
garden_equipment/Fruit-Cage/product.php?pr=
garden_equipment/pest-weed-control/product.php?pr=
gb/comment.php?gb_id=
general.php?abre=
general.php?addr=
general.php?adresa=
general.php?b=
general.php?base_dir=
general.php?body=
general.php?channel=
general.php?chapter=
general.php?choix=
general.php?cmd=
general.php?content=
general.php?doshow=
general.php?e=
general.php?f=
general.php?get=
general.php?goto=
general.php?header=
general.php?id=
general.php?inc=
general.php?include=
general.php?ir=
general.php?itemnav=
general.php?left=
general.php?link=
general.php?menu=
general.php?menue=
general.php?mid=
general.php?middle=
general.php?modo=
general.php?module=
general.php?my=
general.php?name=
general.php?nivel=
general.php?opcion=
general.php?p=
general.php?page=
general.php?pageweb=
general.php?pollname=
general.php?pr=
general.php?pre=
general.php?qry=
general.php?read=
general.php?redirect=
general.php?ref=
general.php?rub=
general.php?secao=
general.php?seccion=
general.php?second=
general.php?section=
general.php?seite=
general.php?sekce=
general.php?sivu=
general.php?strona=
general.php?subject=
general.php?texto=
general.php?thispage=
general.php?tipo=
general.php?to=
general.php?type=
general.php?var=
general.php?w=
general.php?where=
general.php?xlink=
getbook.php?bookid=
GetItems.php?itemid=
giftDetail.php?id=
gig.php?id=
global_projects.php?cid=
global/product/product.php?gubun=
gnu/?doc=
goboard/front/board_view.php?code=
goods_detail.php?data=
haccess.ctl (one way)
haccess.ctl (VERY reliable)
hall.php?file=
hall.php?page=
Hassan Consulting's Shopping Cart Version 1.18
head.php?*[*]*=
head.php?abre=
head.php?adresa=
head.php?b=
head.php?base_dir=
head.php?c=
head.php?choix=
head.php?cmd=
head.php?content=
head.php?corpo=
head.php?d=
head.php?dir=
head.php?disp=
head.php?ev=
head.php?filepath=
head.php?g=
head.php?goto=
head.php?inc=
head.php?incl=
head.php?include=
head.php?index=
head.php?ir=
head.php?ki=
head.php?lang=
head.php?left=
head.php?load=
head.php?loader=
head.php?loc=
head.php?middle=
head.php?middlePart=
head.php?mod=
head.php?modo=
head.php?module=
head.php?numero=
head.php?oldal=
head.php?opcion=
head.php?pag=
head.php?pageweb=
head.php?play=
head.php?pname=
head.php?pollname=
head.php?read=
head.php?ref=
head.php?rub=
head.php?sec=
head.php?sekce=
head.php?sivu=
head.php?start=
head.php?str=
head.php?strona=
head.php?tipo=
head.php?viewpage=
head.php?where=
head.php?y=
help.php?CartId=
help.php?css_path=
help/com_view.html?code=
historialeer.php?num=
HistoryStore/pages/item.php?itemID=
hm/inside.php?id=
home.php?a=
home.php?action=
home.php?addr=
home.php?base_dir=
home.php?basepath=
home.php?body=
home.php?cat=
home.php?category=
home.php?channel=
home.php?chapter=
home.php?choix=
home.php?cmd=
home.php?content=
home.php?disp=
home.php?doshow=
home.php?e=
home.php?ev=
home.php?eval=
home.php?g=
home.php?h=
home.php?id=
home.php?ID=
home.php?in=
home.php?include=
home.php?index=
home.php?ir=
home.php?itemnav=
home.php?k=
home.php?link=
home.php?loader=
home.php?loc=
home.php?menu=
home.php?middle=
home.php?middlePart=
home.php?module=
home.php?my=
home.php?oldal=
home.php?opcion=
home.php?pa=
home.php?page=
home.php?pageweb=
home.php?pagina=
home.php?panel=
home.php?path=
home.php?play=
home.php?pollname=
home.php?pr=
home.php?pre=
home.php?qry=
home.php?read=
home.php?recipe=
home.php?redirect=
home.php?ref=
home.php?rub=
home.php?sec=
home.php?secao=
home.php?section=
home.php?seite=
home.php?sekce=
home.php?showpage=
home.php?sp=
home.php?str=
home.php?thispage=
home.php?tipo=
home.php?w=
home.php?where=
home.php?x=
home.php?z=
homepage.php?sel=
hosting_info.php?id=
ht://Dig htsearch error
html/print.php?sid=
html/scoutnew.php?prodid=
htmlpage.php?id=
htmltonuke.php?filnavn=
htpasswd
htpasswd / htgroup
htpasswd / htpasswd.bak
humor.php?id=
i-know/content.php?page=
ibp.php?ISBN=
ICQ chat logs, please...
idlechat/message.php?id=
ihm.php?p=
IIS 4.0 error messages
IIS web server error messages
IlohaMail"
impex/ImpExData.php?systempath=
inc/cmses/aedating4CMS.php?dir[inc]=
inc/cmses/aedating4CMS.php?dir[inc]= inurl:flashchat site:br bp_ncom.php?bnrep=
inc/cmses/aedatingCMS.php?dir[inc]=
inc/functions.inc.php?config[ppa_root_path]=
inc/header.php/step_one.php?server_inc=
inc/pipe.php?HCL_path=
include.php?*[*]*=
include.php?adresa=
include.php?b=
include.php?basepath=
include.php?channel=
include.php?chapter=
include.php?cmd=
include.php?cont=
include.php?content=
include.php?corpo=
include.php?destino=
include.php?dir=
include.php?eval=
include.php?filepath=
include.php?go=
include.php?goFile=
include.php?goto=
include.php?header=
include.php?in=
include.php?include=
include.php?index=
include.php?ir=
include.php?ki=
include.php?left=
include.php?loader=
include.php?loc=
include.php?mid=
include.php?middle=
include.php?middlePart=
include.php?module=
include.php?my=
include.php?name=
include.php?nivel=
include.php?numero=
include.php?oldal=
include.php?option=
include.php?pag=
include.php?pageweb=
include.php?panel=
include.php?path=
include.php?phpbb_root_path=
include.php?play=
include.php?read=
include.php?redirect=
include.php?ref=
include.php?sec=
include.php?secao=
include.php?seccion=
include.php?second=
include.php?sivu=
include.php?tipo=
include.php?to=
include.php?u=
include.php?url=
include.php?w=
include.php?x=
include/editfunc.inc.php?NWCONF_SYSTEM[server_path]=
include/new-visitor
include/new-visitor.inc.php?lvc_include_dir=
include/write.php?dir=
includes/functions.php?phpbb_root_path=
includes/header.php?systempath=
includes/search.php?GlobalSettings[templatesDirectory]=
Index of phpMyAdmin
index of: intext:Gallery in Configuration mode
index_en.php?id=
index_en.php?ref=
index_principal.php?pagina=
index.of passlist
index.php?_REQUEST=&_REQUEST%5boption%5d=com_content&_REQUEST%5bItemid%5d=1&GLOBALS=&mosConfig_absolute_path=
index.php?=
index.php?a=
index.php?action=
index.php?addr=
index.php?adresa=
index.php?area_id=
index.php?arquivo=
index.php?b=
index.php?base_dir=
index.php?basepath=
index.php?body=
index.php?book=
index.php?c=
index.php?canal=
index.php?cart=
index.php?cartID=
index.php?cat=
index.php?channel=
index.php?chapter=
index.php?cid=
index.php?cmd=
index.php?configFile=
index.php?cont=
index.php?content=
index.php?conteudo=
index.php?cPath=
index.php?dept=
index.php?disp=
index.php?do=
index.php?doc=
index.php?dsp=
index.php?ev=
index.php?file=
index.php?filepath=
index.php?go=
index.php?goto=
index.php?i=
index.php?ID=
index.php?id=
index.php?inc=
index.php?incl=
index.php?include=
index.php?index=
index.php?inhalt=
index.php?j=
index.php?kobr=
index.php?l=
index.php?lang=
index.php?lang=gr&file
index.php?langc=
index.php?Language=
index.php?lg=
index.php?link=
index.php?load=
index.php?Load=
index.php?loc=
index.php?meio.php=
index.php?meio=
index.php?menu=
index.php?menu=deti&page=
index.php?mid=
index.php?middlePart=
index.php?mode=
index.php?modo=
index.php?module=
index.php?modus=
index.php?news=
index.php?nic=
index.php?offs=
index.php?oldal=
index.php?op=
index.php?opcao=
index.php?opcion=
index.php?open=
index.php?openfile=
index.php?option=
index.php?ort=
index.php?p=
index.php?pag=
index.php?page=
index.php?pageid=
index.php?pageId=
index.php?pagename=
index.php?pageurl=
index.php?pagina=
index.php?param=
index.php?path=
index.php?pg_t=
index.php?pg=
index.php?pid=
index.php?pilih=
index.php?place=
index.php?play=
index.php?pname=
index.php?pollname=
index.php?pr=
index.php?pre=
index.php?pref=
index.php?principal=
index.php?r=
index.php?rage=
index.php?recipe=
index.php?RP_PATH=
index.php?screen=
index.php?secao=
index.php?section=
index.php?sekce=
index.php?sel=
index.php?show=
index.php?side=
index.php?site=
index.php?sivu=
index.php?str=
index.php?stranica=
index.php?strona=
index.php?sub=
index.php?sub=index.php?id=index.php?t=
index.php?t=
index.php?template=
index.php?tipo=
index.php?to=
index.php?topic=
index.php?type=
index.php?u=
index.php?u=administrator/components/com_linkdirectory/toolbar.linkdirectory.html.php?mosConfig_absolute_path=
index.php?url=
index.php?var=
index.php?visualizar=
index.php?w=
index.php?where=
index.php?x=
index.php?x= index.php?mode=index.php?stranica=
index.php?y=
index.php/en/component/pvm/?view=
index.phpmain.php?x=
index0.php?show=
index1.php?*[*]*=
index1.php?*root*=
index1.php?=
index1.php?abre=
index1.php?action=
index1.php?adresa=
index1.php?b=
index1.php?body=
index1.php?c=
index1.php?chapter=
index1.php?choix=
index1.php?cmd=
index1.php?d=
index1.php?dat=
index1.php?dir=
index1.php?filepath=
index1.php?get=
index1.php?go=
index1.php?goFile=
index1.php?home=
index1.php?incl=
index1.php?itemnav=
index1.php?l=
index1.php?link=
index1.php?load=
index1.php?loc=
index1.php?menu=
index1.php?mod=
index1.php?modo=
index1.php?my=
index1.php?nivel=
index1.php?o=
index1.php?oldal=
index1.php?op=
index1.php?OpenPage=
index1.php?pa=
index1.php?pagina=
index1.php?param=
index1.php?path=
index1.php?pg=
index1.php?pname=
index1.php?pollname=
index1.php?pr=
index1.php?pre=
index1.php?qry=
index1.php?read=
index1.php?recipe=
index1.php?redirect=
index1.php?second=
index1.php?seite=
index1.php?sekce=
index1.php?showpage=
index1.php?site=
index1.php?str=
index1.php?strona=
index1.php?subject=
index1.php?t=
index1.php?texto=
index1.php?tipo=
index1.php?type=
index1.php?url=
index1.php?v=
index1.php?var=
index1.php?x=
index2.php?action=
index2.php?adresa=
index2.php?ascii_seite=
index2.php?base_dir=
index2.php?basepath=
index2.php?category=
index2.php?channel=
index2.php?chapter=
index2.php?choix=
index2.php?cmd=
index2.php?content=
index2.php?corpo=
index2.php?d=
index2.php?DoAction=
index2.php?doshow=
index2.php?e=
index2.php?f=
index2.php?filepath=
index2.php?get=
index2.php?goto=
index2.php?home=
index2.php?ID=
index2.php?in=
index2.php?inc=
index2.php?incl=
index2.php?include=
index2.php?ir=
index2.php?itemnav=
index2.php?ki=
index2.php?left=
index2.php?link=
index2.php?load=
index2.php?loader=
index2.php?loc=
index2.php?module=
index2.php?my=
index2.php?oldal=
index2.php?open=
index2.php?OpenPage=
index2.php?option=
index2.php?p=
index2.php?pa=
index2.php?param=
index2.php?pg=
index2.php?phpbb_root_path=
index2.php?pname=
index2.php?pollname=
index2.php?pre=
index2.php?pref=
index2.php?qry=
index2.php?recipe=
index2.php?redirect=
index2.php?ref=
index2.php?rub=
index2.php?second=
index2.php?section=
index2.php?sekce=
index2.php?showpage=
index2.php?strona=
index2.php?texto=
index2.php?thispage=
index2.php?to=
index2.php?type=
index2.php?u=
index2.php?url_page=
index2.php?var=
index2.php?x=
index3.php?abre=
index3.php?addr=
index3.php?adresa=
index3.php?base_dir=
index3.php?body=
index3.php?channel=
index3.php?chapter=
index3.php?choix=
index3.php?cmd=
index3.php?d=
index3.php?destino=
index3.php?dir=
index3.php?disp=
index3.php?ev=
index3.php?get=
index3.php?go=
index3.php?home=
index3.php?inc=
index3.php?include=
index3.php?index=
index3.php?ir=
index3.php?itemnav=
index3.php?left=
index3.php?link=
index3.php?loader=
index3.php?menue=
index3.php?mid=
index3.php?middle=
index3.php?mod=
index3.php?my=
index3.php?name=
index3.php?nivel=
index3.php?oldal=
index3.php?open=
index3.php?option=
index3.php?p=
index3.php?pag=
index3.php?pageweb=
index3.php?panel=
index3.php?path=
index3.php?phpbb_root_path=
index3.php?pname=
index3.php?pollname=
index3.php?pre=
index3.php?pref=
index3.php?q=
index3.php?read=
index3.php?redirect=
index3.php?ref=
index3.php?rub=
index3.php?secao=
index3.php?secc=
index3.php?seccion=
index3.php?second=
index3.php?sekce=
index3.php?showpage=
index3.php?sivu=
index3.php?sp=
index3.php?start=
index3.php?t=
index3.php?thispage=
index3.php?tipo=
index3.php?type=
index3.php?url=
index3.php?var=
index3.php?x=
index3.php?xlink=
info.php?*[*]*=
info.php?adresa=
info.php?base_dir=
info.php?body=
info.php?c=
info.php?chapter=
info.php?content=
info.php?doshow=
info.php?ev=
info.php?eval=
info.php?f=
info.php?filepath=
info.php?go=
info.php?header=
info.php?home=
info.php?ID=
info.php?in=
info.php?incl=
info.php?ir=
info.php?itemnav=
info.php?j=
info.php?ki=
info.php?l=
info.php?loader=
info.php?menue=
info.php?mid=
info.php?middlePart=
info.php?o=
info.php?oldal=
info.php?op=
info.php?opcion=
info.php?option=
info.php?pageweb=
info.php?pagina=
info.php?param=
info.php?phpbb_root_path=
info.php?pname=
info.php?pref=
info.php?r=
info.php?read=
info.php?recipe=
info.php?redirect=
info.php?ref=
info.php?rub=
info.php?sec=
info.php?secao=
info.php?seccion=
info.php?start=
info.php?strona=
info.php?subject=
info.php?t=
info.php?texto=
info.php?url=
info.php?var=
info.php?xlink=
info.php?z=
install/index.php?lng=../../include/main.inc&G_PATH=
Interior/productlist.php?id=
interna/tiny_mce/plugins/ibrowser/ibrowser.php?tinyMCE_imglib_include=
Internal Server Error
intext:""BiTBOARD v2.0" BiTSHiFTERS Bulletin Board"
intext:"d.aspx?id" || inurl:"d.aspx?id"
intext:"enable password 7"
intext:"enable secret 5 $"
intext:"Error Message : Error loading required libraries."
intext:"EZGuestbook"
intext:"Fill out the form below completely to change your password and user name. If new username is left blank, your old one will be assumed." -edu
intext:"Mail admins login here to administrate your domain."
intext:"Master Account" "Domain Name" "Password" inurl:/cgi-bin/qmailadmin
intext:"Powered By : SE Software Technologies" filetype:php
intext:"powered by Web Wiz Journal"
intext:"Session Start * * * *:*:* *" filetype:log
intext:"SteamUserPassphrase=" intext:"SteamAppUser=" -"username" -"user"
intext:"Storage Management Server for" intitle:"Server Administration"
intext:"Tobias Oetiker" "traffic analysis"
intext:"vbulletin" inurl:admincp
intext:"Warning: * am able * write ** configuration file" "includes/configure.php" -
intext:"Warning: Failed opening" "on line" "include_path"
intext:"Web Wiz Journal"
intext:"Welcome to the Web V.Networks" intitle:"V.Networks [Top]" -filetype:htm
intext:"Welcome to" inurl:"cp" intitle:"H-SPHERE" inurl:"begin.html" -Fee
intext:(password | passcode) intext:(username | userid | user) filetype:csv
intext:gmail invite intext:http://gmail.google.com/gmail/a
intext:SQLiteManager inurl:main.php
intext:ViewCVS inurl:Settings.php
intitle:"--- VIDEO WEB SERVER ---" intext:"Video Web Server" "Any time & Any where" username password
intitle:"*- HP WBEM Login" | "You are being prompted to provide login account information for *" | "Please provide the information requested and press
intitle:"500 Internal Server Error" "server at"
intitle:"actiontec" main setup status "Copyright 2001 Actiontec Electronics Inc"
intitle:"Admin Login" "admin login" "blogware"
intitle:"Admin login" "Web Site Administration" "Copyright"
intitle:"admin panel" +"
intitle:"admin panel" +"RedKernel"
intitle:"ADSL Configuration page"
intitle:"AlternC Desktop"
intitle:"Apache Tomcat" "Error Report"
intitle:"Apache::Status" (inurl:server-status | inurl:status.html | inurl:apache.html)
intitle:"AppServ Open Project" -site:www.appservnetwork.com
intitle:"ASP Stats Generator *.*" "ASP Stats Generator" "2003-2004 weppos"
intitle:"Athens Authentication Point"
intitle:"Azureus : Java BitTorrent Client Tracker"
intitle:"b2evo > Login form" "Login form. You must log in! You will have to accept cookies in order to log in" -demo -site:b2evolution.net
intitle:"Belarc Advisor Current Profile" intext:"Click here for Belarc's PC Management products, for large and small companies."
intitle:"Big Sister" +"OK Attention Trouble"
intitle:"BNBT Tracker Info"
intitle:"Browser Launch Page"
intitle:"Cisco CallManager User Options Log On" "Please enter your User ID and Password in the spaces provided below and click the Log On button to co
intitle:"ColdFusion Administrator Login"
intitle:"communigate pro * *" intitle:"entrance"
intitle:"Connection Status" intext:"Current login"
intitle:"Content Management System" "user name"|"password"|"admin" "Microsoft IE 5.5" -mambo
intitle:"curriculum vitae" filetype:doc
intitle:"Default PLESK Page"
intitle:"Dell Remote Access Controller"
intitle:"DocuShare" inurl:"docushare/dsweb/" -faq -gov -edu
intitle:"Docutek ERes - Admin Login" -edu
intitle:"edna:streaming mp3 server" -forums
intitle:"Employee Intranet Login"
intitle:"eMule *" intitle:"- Web Control Panel" intext:"Web Control Panel" "Enter your password here."
intitle:"ePowerSwitch Login"
intitle:"Error Occurred While Processing Request" +WHERE (SELECT|INSERT) filetype:cfm
intitle:"Error Occurred" "The error occurred in" filetype:cfm
intitle:"Error using Hypernews" "Server Software"
intitle:"EverFocus.EDSR.applet"
intitle:"Execution of this s?ri?t not permitted"
intitle:"Execution of this script not permitted"
intitle:"eXist Database Administration" -demo
intitle:"EXTRANET * - Identification"
intitle:"EXTRANET login" -.edu -.mil -.gov
intitle:"EZPartner" -netpond
intitle:"Flash Operator Panel" -ext:php -wiki -cms -inurl:asternic -inurl:sip -intitle:ANNOUNCE -inurl:lists
intitle:"FTP root at"
intitle:"Gateway Configuration Menu"
intitle:"Horde :: My Portal" -"[Tickets"
intitle:"i-secure v1.1" -edu
intitle:"Icecast Administration Admin Page"
intitle:"iDevAffiliate - admin" -demo
intitle:"inc. vpn 3000 concentrator"
intitle:"Index of..etc" passwd
intitle:"Index Of" -inurl:maillog maillog size
intitle:"Index of" .bash_history
intitle:"Index of" .mysql_history
intitle:"Index of" .sh_history
intitle:"Index of" ".htpasswd" "htgroup" -intitle:"dist" -apache -htpasswd.c
intitle:"index of" +myd size
intitle:"Index of" cfide
intitle:"Index Of" cookies.txt size
intitle:"index of" etc/shadow
intitle:"index of" htpasswd
intitle:"index of" intext:connect.inc
intitle:"index of" intext:globals.inc
intitle:"index of" master.passwd
intitle:"index of" members OR accounts
intitle:"index of" mysql.conf OR mysql_config
intitle:"index of" passwd
intitle:"Index of" passwords modified
intitle:"index of" people.lst
intitle:"index of" pwd.db
intitle:"Index of" pwd.db
intitle:"Index of" sc_serv.conf sc_serv content
intitle:"index of" spwd
intitle:"Index of" spwd.db passwd -pam.conf
intitle:"Index of" upload size parent directory
intitle:"index of" user_carts OR user_cart
intitle:"index.of *" admin news.asp configview.asp
intitle:"index.of" .diz .nfo last modified
intitle:"ISPMan : Unauthorized Access prohibited"
intitle:"ITS System Information" "Please log on to the SAP System"
intitle:"iVISTA.Main.Page"
intitle:"Joomla - Web Installer"
intitle:"Kurant Corporation StoreSense" filetype:bok
intitle:"ListMail Login" admin -demo
intitle:"live view" intitle:axis
intitle:"Login -
intitle:"Login Forum
intitle:"Login to @Mail" (ext:pl | inurl:"index") -dwaffleman
intitle:"Login to Cacti"
intitle:"Login to the forums - @www.aimoo.com" inurl:login.cfm?id=
intitle:"LOGREP - Log file reporting system" -site:itefix.no
intitle:"Mail Server CMailServer Webmail" "5.2"
intitle:"MailMan Login"
intitle:"Member Login" "NOTE: Your browser must have cookies enabled in order to log into the site." ext:php OR ext:cgi
intitle:"Merak Mail Server Web Administration" -ihackstuff.com
intitle:"microsoft certificate services" inurl:certsrv
intitle:"Microsoft Site Server Analysis"
intitle:"MikroTik RouterOS Managing Webpage"
intitle:"Multimon UPS status page"
intitle:"MvBlog powered"
intitle:"MX Control Console" "If you can't remember"
intitle:"Nessus Scan Report" "This file was generated by Nessus"
intitle:"network administration" inurl:"nic"
intitle:"Novell Web Services" "GroupWise" -inurl:"doc/11924" -.mil -.edu -.gov -filetype:pdf
intitle:"Novell Web Services" intext:"Select a service and a language."
intitle:"OfficeConnect Cable/DSL Gateway" intext:"Checking your browser"
intitle:"oMail-admin Administration - Login" -inurl:omnis.ch
intitle:"OnLine Recruitment Program - Login"
intitle:"Philex 0.2*" -s?ri?t -site:freelists.org
intitle:"Philex 0.2*" -script -site:freelists.org
intitle:"PHP Advanced Transfer" (inurl:index.php | inurl:showrecent.php )
intitle:"PHP Advanced Transfer" inurl:"login.php"
intitle:"php icalendar administration" -site:sourceforge.net
intitle:"PHPBTTracker Statistics" | intitle:"PHPBT Tracker Statistics"
intitle:"phpinfo()" +"mysql.default_password" +"Zend s?ri?ting Language Engine"
intitle:"PhpMyExplorer" inurl:"index.php" -cvs
intitle:"phpPgAdmin - Login" Language
intitle:"PHProjekt - login" login password
intitle:"please login" "your password is *"
intitle:"remote assessment" OpenAanval Console
intitle:"Remote Desktop Web Connection"
intitle:"Remote Desktop Web Connection" inurl:tsweb
intitle:"Retina Report" "CONFIDENTIAL INFORMATION"
intitle:"Samba Web Administration Tool" intext:"Help Workgroup"
intitle:"SFXAdmin - sfx_global" | intitle:"SFXAdmin - sfx_local" | intitle:"SFXAdmin - sfx_test"
intitle:"SHOUTcast Administrator" inurl:admin.cgi
intitle:"site administration: please log in" "site designed by emarketsouth"
intitle:"start.managing.the.device" remote pbx acc
intitle:"statistics of" "advanced web statistics"
intitle:"Supero Doctor III" -inurl:supermicro
intitle:"supervisioncam protocol"
intitle:"SuSE Linux Openexchange Server" "Please activate Javas?ri?t!"
intitle:"SuSE Linux Openexchange Server" "Please activate JavaScript!"
intitle:"switch login" "IBM Fast Ethernet Desktop"
intitle:"SWW link" "Please wait....."
intitle:"sysinfo * " intext:"Generated by Sysinfo * written by The Gamblers."
intitle:"System Statistics" +"System and Network Information Center"
intitle:"teamspeak server-administration
intitle:"Terminal Services Web Connection"
intitle:"Tomcat Server Administration"
intitle:"TOPdesk ApplicationServer"
intitle:"TUTOS Login"
intitle:"TWIG Login"
intitle:"twiki" inurl:"TWikiUsers"
intitle:"Under construction" "does not currently have"
intitle:"Uploader - Uploader v6" -pixloads.com
intitle:"urchin (5|3|admin)" ext:cgi
intitle:"Usage Statistics for" "Generated by Webalizer"
intitle:"vhost" intext:"vHost . 2000-2004"
intitle:"Virtual Server Administration System"
intitle:"VisNetic WebMail" inurl:"/mail/"
intitle:"VitalQIP IP Management System"
intitle:"VMware Management Interface:" inurl:"vmware/en/"
intitle:"VNC viewer for Java"
intitle:"wbem" compaq login "Compaq Information Technologies Group"
intitle:"Web Server Statistics for ****"
intitle:"web server status" SSH Telnet
intitle:"web-cyradm"|"by Luc de Louw" "This is only for authorized users" -tar.gz -site:web-cyradm.org
intitle:"WebLogic Server" intitle:"Console Login" inurl:console
intitle:"Welcome Site/User Administrator" "Please select the language" -demos
intitle:"Welcome to F-Secure Policy Manager Server Welcome Page"
intitle:"Welcome to Mailtraq WebMail"
intitle:"welcome to netware *" -site:novell.com
intitle:"Welcome to the Advanced Extranet Server, ADVX!"
intitle:"Welcome to Windows 2000 Internet Services"
intitle:"welcome.to.squeezebox"
intitle:"WJ-NT104 Main Page"
intitle:"WorldClient" intext:"? (2003|2004) Alt-N Technologies."
intitle:"xams 0.0.0..15 - Login"
intitle:"XcAuctionLite" | "DRIVEN BY XCENT" Lite inurl:admin
intitle:"XMail Web Administration Interface" intext:Login intext:password
intitle:"Zope Help System" inurl:HelpSys
intitle:"ZyXEL Prestige Router" "Enter password"
intitle:("TrackerCam Live Video")|("TrackerCam Application Login")|("Trackercam Remote") -trackercam.com
intitle:admin intitle:login
intitle:asterisk.management.portal web-access
intitle:axis intitle:"video server"
intitle:Bookmarks inurl:bookmarks.html "Bookmarks
intitle:Configuration.File inurl:softcart.exe
intitle:dupics inurl:(add.asp | default.asp | view.asp | voting.asp) -site:duware.com
intitle:endymion.sak?.mail.login.page | inurl:sake.servlet
intitle:Group-Office "Enter your username and password to login"
intitle:ilohamail "
intitle:ilohamail intext:"Version 0.8.10" "
intitle:IMP inurl:imp/index.php3
intitle:index.of "Apache" "server at"
intitle:index.of administrators.pwd
intitle:index.of cgiirc.config
intitle:index.of cleanup.log
intitle:index.of dead.letter
intitle:Index.of etc shadow
intitle:Index.of etc shadow site:passwd
intitle:index.of inbox
intitle:index.of inbox dbx
intitle:index.of intext:"secring.skr"|"secring.pgp"|"secring.bak"
intitle:index.of master.passwd
intitle:index.of passwd passwd.bak
intitle:index.of people.lst
intitle:index.of trillian.ini
intitle:index.of ws_ftp.ini
intitle:intranet inurl:intranet +intext:"phone"
intitle:liveapplet
intitle:Login * Webmailer
intitle:Login intext:"RT is ? Copyright"
intitle:Node.List Win32.Version.3.11
intitle:Novell intitle:WebAccess "Copyright *-* Novell, Inc"
intitle:open-xchange inurl:login.pl
intitle:opengroupware.org "resistance is obsolete" "Report Bugs" "Username" "password"
intitle:osCommerce inurl:admin intext:"redistributable under the GNU" intext:"Online Catalog" -demo -site:oscommerce.com
intitle:Ovislink inurl:private/login
intitle:phpMyAdmin "Welcome to phpMyAdmin ***" "running on * as root@*"
intitle:phpnews.login
intitle:plesk inurl:login.php3
intitle:rapidshare intext:login
inurl::2082/frontend -demo
inurl:":10000" intext:webmin
inurl:"/admin/configuration. php?" Mystore
inurl:"/axs/ax-admin.pl" -s?ri?t
inurl:"/axs/ax-admin.pl" -script
inurl:"/catalog.nsf" intitle:catalog
inurl:"/cricket/grapher.cgi"
inurl:"/NSearch/AdminServlet"
inurl:"/slxweb.dll/external?name=(custportal|webticketcust)"
inurl:"1220/parse_xml.cgi?"
inurl:"631/admin" (inurl:"op=*") | (intitle:CUPS)
inurl:"8003/Display?what="
inurl:"Activex/default.htm" "Demo"
inurl:"auth_user_file.txt"
inurl:"bookmark.htm"
inurl:"cacti" +inurl:"graph_view.php" +"Settings Tree View" -cvs -RPM
inurl:"calendar.asp?action=login"
inurl:"calendars?ri?t/users.txt"
inurl:"default/login.php" intitle:"kerio"
inurl:"editor/list.asp" | inurl:"database_editor.asp" | inurl:"login.asa" "are set"
inurl:"GRC.DAT" intext:"password"
inurl:"gs/adminlogin.aspx"
inurl:"id=" & intext:"Warning: array_merge()
inurl:"id=" & intext:"Warning: filesize()
inurl:"id=" & intext:"Warning: getimagesize()
inurl:"id=" & intext:"Warning: ilesize()
inurl:"id=" & intext:"Warning: is_writable()
inurl:"id=" & intext:"Warning: mysql_fetch_array()
inurl:"id=" & intext:"Warning: mysql_fetch_assoc()
inurl:"id=" & intext:"Warning: mysql_num_rows()
inurl:"id=" & intext:"Warning: mysql_query()
inurl:"id=" & intext:"Warning: mysql_result()
inurl:"id=" & intext:"Warning: pg_exec()
inurl:"id=" & intext:"Warning: preg_match()
inurl:"id=" & intext:"Warning: require()
inurl:"id=" & intext:"Warning: session_start()
inurl:"id=" & intext:"Warning: Unknown()
inurl:"index.php? module=ew_filemanager"
inurl:"install/install.php"
inurl:"map.asp?" intitle:"WhatsUp Gold"
inurl:"newsletter/admin/"
inurl:"newsletter/admin/" intitle:"newsletter admin"
inurl:"NmConsole/Login.asp" | intitle:"Login - Ipswitch WhatsUp Professional 2005" | intext:"Ipswitch WhatsUp Professional 2005 (SP1)" "Ipswitch, Inc"
inurl:"php121login.php"
inurl:"printer/main.html" intext:"settings"
inurl:"putty.reg"
inurl:"Sites.dat"+"PASS="
inurl:"sitescope.html" intitle:"sitescope" intext:"refresh" -demo
inurl:"slapd.conf" intext:"credentials" -manpage -"Manual Page" -man: -sample
inurl:"slapd.conf" intext:"rootpw" -manpage -"Manual Page" -man: -sample
inurl:"smb.conf" intext:"workgroup" filetype:conf conf
inurl:"suse/login.pl"
inurl:"typo3/index.php?u=" -demo
inurl:"usysinfo?login=true"
inurl:"utilities/TreeView.asp"
inurl:"ViewerFrame?Mode="
inurl:"vsadmin/login" | inurl:"vsadmin/admin" inurl:.php|.asp
inurl:"wvdial.conf" intext:"password"
inurl:"wwwroot/
inurl:*db filetype:mdb
inurl:/_layouts/settings
inurl:/*.php?id=
inurl:/adm-cfgedit.php
inurl:/admin/login.asp
inurl:/articles.php?id=
inurl:/calendar.php?token=
inurl:/careers-detail.asp?id=
inurl:/cgi-bin/finger? "In real life"
inurl:/cgi-bin/finger? Enter (account|host|user|username)
inurl:/cgi-bin/pass.txt
inurl:/cgi-bin/sqwebmail?noframes=1
inurl:/Citrix/Nfuse17/
inurl:/CollectionContent.asp?id=
inurl:/commodities.php?*id=
inurl:/Content.asp?id=
inurl:/counter/index.php intitle:"+PHPCounter 7.*"
inurl:/dana-na/auth/welcome.html
inurl:/db/main.mdb
inurl:/default.php?id=
inurl:/default.php?portalID=
inurl:/Details.asp?id=
inurl:/details.php?linkid=
inurl:/dosearch.asp?
inurl:/eprise/
inurl:/eventdetails.php?*=
inurl:/filedown.php?file=
inurl:/gallery.asp?cid=
inurl:/games.php?id= "Powered by PHPD Game Edition"
inurl:/gmap.php?id=
inurl:/imprimir.php?id=
inurl:/include/footer.inc.php?_AMLconfig[cfg_serverpath]=
inurl:/index.php?pgId=
inurl:/index.php?PID= "Powered By Dew-NewPHPLinks v.2.1b"
inurl:/list_blogs.php?sort_mode=
inurl:/Merchant2/admin.mv | inurl:/Merchant2/admin.mvc | intitle:"Miva Merchant Administration Login" -inurl:cheap-malboro.net
inurl:/modcp/ intext:Moderator+vBulletin
inurl:/mpfn=pdview&id=
inurl:/news.php?include=
inurl:/notizia.php?idArt=
inurl:/os_view_full.php?
inurl:/prodotti.php?id=
inurl:/publications.asp?type=
inurl:/recipe-view.php?id=
inurl:/reservations.php?id=
inurl:/shared/help.php?page=
inurl:/squirrelcart/cart_content.php?cart_isp_root=
inurl:/SUSAdmin intitle:"Microsoft Software upd?t? Services"
inurl:/SUSAdmin intitle:"Microsoft Software Update Services"
inurl:/view/lang/index.php?page=?page=
inurl:/viewfaqs.php?cat=
inurl:/webedit.* intext:WebEdit Professional -html
inurl:/WhatNew.asp?page=&id=
inurl:/wwwboard
inurl:/yabb/Members/Admin.dat
inurl:1810 "Oracle Enterprise Manager"
inurl:2000 intitle:RemotelyAnywhere -site:realvnc.com
inurl:aboutbook.php?id=
inurl:access
inurl:act=
inurl:action=
inurl:admin filetype:db
inurl:admin filetype:xls
inurl:admin intitle:login
inurl:administrator "welcome to mambo"
inurl:ages.php?id=
inurl:ajax.php?page=
inurl:announce.php?id=
inurl:aol*/_do/rss_popup?blogID=
inurl:API_HOME_DIR=
inurl:art.php?idm=
inurl:article.php?ID=
inurl:article.php?id=
inurl:artikelinfo.php?id=
inurl:asp
inurl:avd_start.php?avd=
inurl:axis-cgi/jpg
inurl:axis-cgi/mjpg (motion-JPEG)
inurl:backup filetype:mdb
inurl:band_info.php?id=
inurl:bin.welcome.sh | inurl:bin.welcome.bat | intitle:eHealth.5.0
inurl:board=
inurl:build.err
inurl:buy
inurl:buy.php?category=
inurl:cat=
inurl:category.php?id=
inurl:ccbill filetype:log
inurl:cgi
inurl:cgi-bin inurl:calendar.cfg
inurl:cgi-bin/printenv
inurl:cgi-bin/testcgi.exe "Please distribute TestCGI"
inurl:cgi-bin/ultimatebb.cgi?ubb=login
inurl:cgiirc.config
inurl:changepassword.asp
inurl:channel_id=
inurl:chap-secrets -cvs
inurl:chappies.php?id=
inurl:Citrix/MetaFrame/default/default.aspx
inurl:clanek.php4?id=
inurl:client_id=
inurl:clubpage.php?id=
inurl:cmd=
inurl:collectionitem.php?id=
inurl:communique_detail.php?id=
inurl:config.php dbuname dbpass
inurl:confixx inurl:login|anmeldung
inurl:cont=
inurl:coranto.cgi intitle:Login (Authorized Users Only)
inurl:CrazyWWWBoard.cgi intext:"detailed debugging information"
inurl:csCreatePro.cgi
inurl:current_frame=
inurl:curriculum.php?id=
inurl:data
inurl:date=
inurl:declaration_more.php?decl_id=
inurl:default.asp intitle:"WebCommander"
inurl:detail.php?ID=
inurl:detail=
inurl:dir=
inurl:display=
inurl:download
inurl:download.php?id=
inurl:download=
inurl:downloads_info.php?id=
inurl:ds.py
inurl:email filetype:mdb
inurl:event.php?id=
inurl:exchweb/bin/auth/owalogon.asp
inurl:f=
inurl:faq2.php?id=
inurl:fcgi-bin/echo
inurl:fellows.php?id=
inurl:fiche_spectacle.php?id=
inurl:file
inurl:file=
inurl:fileinclude=
inurl:filename=
inurl:filezilla.xml -cvs
inurl:firm_id=
inurl:footer.inc.php
inurl:forum
inurl:forum filetype:mdb
inurl:forum_bds.php?num=
inurl:forward filetype:forward -cvs
inurl:g=
inurl:galeri_info.php?l=
inurl:gallery.php?id=
inurl:game.php?id=
inurl:games.php?id=
inurl:getdata=
inurl:getmsg.html intitle:hotmail
inurl:gnatsweb.pl
inurl:go=
inurl:historialeer.php?num=
inurl:home
inurl:home.php?pagina=
inurl:hosting_info.php?id=
inurl:hp/device/this.LCDispatcher
inurl:HT=
inurl:html
inurl:htpasswd filetype:htpasswd
inurl:humor.php?id=
inurl:idd=
inurl:ids5web
inurl:iisadmin
inurl:inc
inurl:inc=
inurl:incfile=
inurl:incl=
inurl:include_file=
inurl:include_path=
inurl:index.cgi?aktion=shopview
inurl:index.php?=
inurl:index.php?conteudo=
inurl:index.php?id=
inurl:index.php?load=
inurl:index.php?opcao=
inurl:index.php?principal=
inurl:index.php?show=
inurl:index2.php?option=
inurl:index2.php?to=
inurl:indexFrame.shtml Axis
inurl:infile=
inurl:info
inurl:info.inc.php
inurl:info=
inurl:iniziativa.php?in=
inurl:ir=
inurl:irc filetype:cgi cgi:irc
inurl:item_id=
inurl:kategorie.php4?id=
inurl:labels.php?id=
inurl:lang=
inurl:language=
inurl:lilo.conf filetype:conf password -tatercounter2000 -bootpwd -man
inurl:link=
inurl:list
inurl:load=
inurl:loadpsb.php?id=
inurl:log.nsf -gov
inurl:login filetype:swf swf
inurl:login.asp
inurl:login.cfm
inurl:login.jsp.bak
inurl:login.php "SquirrelMail version"
inurl:look.php?ID=
inurl:mail
inurl:main.php phpMyAdmin
inurl:main.php Welcome to phpMyAdmin
inurl:main.php?id=
inurl:main=
inurl:mainspot=
inurl:ManyServers.htm
inurl:material.php?id=
inurl:memberInfo.php?id=
inurl:metaframexp/default/login.asp | intitle:"Metaframe XP Login"
inurl:mewebmail
inurl:midicart.mdb
inurl:msg=
inurl:names.nsf?opendatabase
inurl:netscape.hst
inurl:netscape.ini
inurl:netw_tcp.shtml
inurl:new
inurl:news_display.php?getid=
inurl:news_view.php?id=
inurl:news-full.php?id=
inurl:news.php?id=
inurl:newscat.php?id=
inurl:newsdesk.cgi? inurl:"t="
inurl:newsDetail.php?id=
inurl:newsid=
inurl:newsitem.php?num=
inurl:newsone.php?id=
inurl:newsticker_info.php?idn=
inurl:nuke filetype:sql
inurl:num=
inurl:ocw_login_username
inurl:odbc.ini ext:ini -cvs
inurl:offer.php?idf=
inurl:ogl_inet.php?ogl_id=
inurl:openfile=
inurl:opinions.php?id=
inurl:orasso.wwsso_app_admin.ls_login
inurl:order
inurl:ospfd.conf intext:password -sample -test -tutorial -download
inurl:ovcgi/jovw
inurl:p=
inurl:page.php?file=
inurl:page.php?id=
inurl:page=
inurl:pageid=
inurl:Pageid=
inurl:pages
inurl:pages.php?id=
inurl:pagina=
inurl:pap-secrets -cvs
inurl:participant.php?id=
inurl:pass.dat
inurl:passlist.txt
inurl:path_to_calendar=
inurl:path=
inurl:perform filetype:ini
inurl:perform.ini filetype:ini
inurl:perl/printenv
inurl:person.php?id=
inurl:pg=
inurl:php.ini filetype:ini
inurl:phpSysInfo/ "created by phpsysinfo"
inurl:play_old.php?id=
inurl:pls/admin_/gateway.htm
inurl:pop.php?id=
inurl:portscan.php "from Port"|"Port Range"
inurl:post.php?id=
inurl:postfixadmin intitle:"postfix admin" ext:php
inurl:preferences.ini "[emule]"
inurl:preview.php?id=
inurl:prod_detail.php?id=
inurl:prod_info.php?id=
inurl:product_ranges_view.php?ID=
inurl:product-item.php?id=
inurl:product.php?id=
inurl:product.php?mid=
inurl:productdetail.php?id=
inurl:productinfo.php?id=
inurl:Productinfo.php?id=
inurl:produit.php?id=
inurl:profile_view.php?id=
inurl:profiles filetype:mdb
inurl:proxy | inurl:wpad ext:pac | ext:dat findproxyforurl
inurl:Proxy.txt
inurl:public
inurl:publications.php?id=
inurl:qry_str=
inurl:ray.php?id=
inurl:read.php?=
inurl:read.php?id=
inurl:readnews.php?id=
inurl:reagir.php?num=
inurl:releases.php?id=
inurl:report "EVEREST Home Edition "
inurl:review.php?id=
inurl:rpSys.html
inurl:rub.php?idr=
inurl:rubp.php?idr=
inurl:rubrika.php?idr=
inurl:ruta=
inurl:safehtml=
inurl:search
inurl:search.php vbulletin
inurl:search/admin.php
inurl:secring ext:skr | ext:pgp | ext:bak
inurl:section.php?id=
inurl:section=
inurl:select_biblio.php?id=
inurl:sem.php3?id=
inurl:server-info "Apache Server Information"
inurl:server-status "apache"
inurl:server.cfg rcon password
inurl:servlet/webacc
inurl:shop
inurl:shop_category.php?id=
inurl:shop.php?do=part&id=
inurl:shopdbtest.asp
inurl:shopping.php?id=
inurl:show_an.php?id=
inurl:show.php?id=
inurl:showfile=
inurl:showimg.php?id=
inurl:shredder-categories.php?id=
inurl:side=
inurl:site_id=
inurl:skin=
inurl:snitz_forums_2000.mdb
inurl:software
inurl:spr.php?id=
inurl:sql.php?id=
inurl:ssl.conf filetype:conf
inurl:staff_id=
inurl:static=
inurl:statrep.nsf -gov
inurl:status.cgi?host=all
inurl:story.php?id=
inurl:str=
inurl:Stray-Questions-View.php?num=
inurl:strona=
inurl:sub=
inurl:support
inurl:sw_comment.php?id=
inurl:tdbin
inurl:tekst.php?idt=
inurl:testcgi xitami
inurl:textpattern/index.php
inurl:theme.php?id=
inurl:title.php?id=
inurl:top10.php?cat=
inurl:tradeCategory.php?id=
inurl:trainers.php?id=
inurl:transcript.php?id=
inurl:tresc=
inurl:url=
inurl:user
inurl:user=
inurl:vbstats.php "page generated"
inurl:ventrilo_srv.ini adminpassword
inurl:view_ad.php?id=
inurl:view_faq.php?id=
inurl:view_product.php?id=
inurl:view.php?id=
inurl:view/index.shtml
inurl:view/indexFrame.shtml
inurl:view/view.shtml
inurl:viewapp.php?id=
inurl:ViewerFrame?Mode=Refresh
inurl:viewphoto.php?id=
inurl:viewshowdetail.php?id=
inurl:vtund.conf intext:pass -cvs
inurl:vtund.conf intext:pass -cvs s
inurl:WCP_USER
inurl:web
inurl:webalizer filetype:png -.gov -.edu -.mil -opendarwin
inurl:webmail./index.pl "Interface"
inurl:website.php?id=
inurl:webutil.pl
inurl:webvpn.html "login" "Please enter your"
inurl:webvpn.html "login" "Please enter your" Login ("admin account info") filetype:log
inurl:wp-mail.php + "There doesn't seem to be any new mail."
inurl:XcCDONTS.asp
inurl:yapboz_detay.asp
inurl:yapboz_detay.asp + View Webcam User Accessing
inurl:zebra.conf intext:password -sample -test -tutorial -download
ipsec.conf
ipsec.secrets
irbeautina/product_detail.php?product_id=
item_book.php?CAT=
item_details.php?catid=
item_list.php?cat_id=
item_list.php?maingroup
item_show.php?code_no=
item_show.php?id=
item_show.php?lid=
item.php?eid=
item.php?id=
item.php?iid=
item.php?item_id=
item.php?itemid=
item.php?model=
item.php?prodtype=
item.php?shopcd=
item.php?sub_id=
item/detail.php?num=
itemDesc.php?CartId=
itemdetail.php?item=
itemdetails.php?catalogid=
Jetbox One CMS â?¢" | "
Jetstream ? *")
kategorie.php4?id=
kboard/kboard.php?board=
KM/BOARD/readboard.php?id=
knowledge_base/detail.php?id=
kshop/product.php?productid=
layout.php?abre=
layout.php?action=
layout.php?addr=
layout.php?basepath=
layout.php?c=
layout.php?category=
layout.php?chapter=
layout.php?choix=
layout.php?cmd=
layout.php?cont=
layout.php?disp=
layout.php?g=
layout.php?goto=
layout.php?incl=
layout.php?ir=
layout.php?link=
layout.php?loader=
layout.php?menue=
layout.php?modo=
layout.php?my=
layout.php?nivel=
layout.php?numero=
layout.php?oldal=
layout.php?opcion=
layout.php?OpenPage=
layout.php?page=
layout.php?pageweb=
layout.php?pagina=
layout.php?panel=
layout.php?path=
layout.php?play=
layout.php?pollname=
layout.php?pref=
layout.php?qry=
layout.php?secao=
layout.php?section=
layout.php?seite=
layout.php?sekce=
layout.php?strona=
layout.php?thispage=
layout.php?tipo=
layout.php?url=
layout.php?var=
layout.php?where=
layout.php?xlink=
layout.php?z=
LeapFTP intitle:"index.of./" sites.ini modified
learnmore.php?cartID=
lib/gore.php?libpath=
library.php?cat=
Link Department"
links.php?catid=
list.php?bookid=
List.php?CatID=
listcategoriesandproducts.php?idCategory=
listing.php?cat=
liveapplet
lmsrecords_cd.php?cdid=
loadpsb.php?id=
Login ("
login.php?dir=
Looking Glass
ls.php?id=
m_view.php?ps_db=
m2f/m2f_phpbb204.php?m2f_root_path=
magazin.php?cid=
magazine-details.php?magid=
magazines/adult_magazine_full_year.php?magid=
magazines/adult_magazine_single_page.php?magid=
mail filetype:csv -site:gov intext:name
main.php?action=
main.php?addr=
main.php?adresa=
main.php?basepath=
main.php?body=
main.php?category=
main.php?chapter=
main.php?content=
main.php?corpo=
main.php?dir=
main.php?disp=
main.php?doshow=
main.php?e=
main.php?eval=
main.php?filepath=
main.php?goto=
main.php?h=
main.php?id=
main.php?inc=
main.php?include=
main.php?index=
main.php?ir=
main.php?item=
main.php?itemnav=
main.php?j=
main.php?link=
main.php?load=
main.php?loc=
main.php?middle=
main.php?mod=
main.php?my=
main.php?name=
main.php?oldal=
main.php?opcion=
main.php?page=
main.php?pagina=
main.php?param=
main.php?path=
main.php?pg=
main.php?pname=
main.php?pre=
main.php?pref=
main.php?prodID=
main.php?r=
main.php?ref=
main.php?second=
main.php?section=
main.php?site=
main.php?start=
main.php?str=
main.php?strona=
main.php?subject=
main.php?thispage=
main.php?tipo=
main.php?type=
main.php?url=
main.php?v=
main.php?where=
main.php?x=
main.php?xlink=
main/index.php?action=
main/index.php?uid=
main/magpreview.php?id=
mall/more.php?ProdID=
master.passwd
mb_showtopic.php?topic_id=
mboard/replies.php?parent_id=
media.php?page=
media/pr.php?id=
melbourne_details.php?id=
memberInfo.php?id=
Merak Mail Server Software" -.gov -.mil -.edu -site:merakmailserver.com
message/comment_threads.php?postID=
Microsoft Money Data Files
Midmart Messageboard" "Administrator Login"
mod*.php?action=
mod*.php?addr=
mod*.php?b=
mod*.php?channel=
mod*.php?chapter=
mod*.php?choix=
mod*.php?cont=
mod*.php?content=
mod*.php?corpo=
mod*.php?d=
mod*.php?destino=
mod*.php?dir=
mod*.php?ev=
mod*.php?goFile=
mod*.php?home=
mod*.php?incl=
mod*.php?include=
mod*.php?index=
mod*.php?ir=
mod*.php?j=
mod*.php?lang=
mod*.php?link=
mod*.php?m=
mod*.php?middle=
mod*.php?module=
mod*.php?numero=
mod*.php?oldal=
mod*.php?OpenPage=
mod*.php?pag=
mod*.php?pageweb=
mod*.php?pagina=
mod*.php?path=
mod*.php?pg=
mod*.php?phpbb_root_path=
mod*.php?play=
mod*.php?pname=
mod*.php?pre=
mod*.php?qry=
mod*.php?recipe=
mod*.php?secao=
mod*.php?secc=
mod*.php?seccion=
mod*.php?section=
mod*.php?sekce=
mod*.php?start=
mod*.php?strona=
mod*.php?thispage=
mod*.php?tipo=
mod*.php?to=
mod*.php?v=
mod*.php?var=
modline.php?id=
module_db.php?pivot_path=
module/range/dutch_windmill_collection.php?rangeId=
modules.php?****=
modules.php?bookid=
modules/AllMyGuests/signin.php?_AMGconfig[cfg_serverpath]=
modules/content/index.php?id=
modules/coppermine/themes/coppercop/theme.php?THEME_DIR=
modules/forum/index.php?topic_id=
modules/My_eGallery/index.php?basepath=
modules/vwar/admin/admin.php?vwar_root=
Monster Top List" MTL numrange:200-
more_detail.php?id=
more_detail.php?X_EID=
More_Details.php?id=
more_details.php?id=
mt-db-pass.cgi files
mwchat/libs/start_lobby.php?CONFIG[MWCHAT_Libs]=
myaccount.php?catid=
myevent.php?myevent_path=
MYSQL error message: supplied argument....
mysql error with query
mysql history files
MySQL tabledata dumps
mystuff.xml - Trillian data files
n_replyboard.php?typeboard=
naboard/memo.php?bd=
natterchat inurl:home.asp -site:natterchat.co.uk
Netscape Application Server Error page
news_and_notices.php?news_id=
news_content.php?CategoryID=
news_detail.php?file=
news_item.php?id=
news_view.php?id=
news.php?id=
news.php?ID=
news.php?t=
news.php?type=
news/detail.php?id=
news/latest_news.php?cat_id=
news/news.php?id=
news/news/title_show.php?id=
news/newsitem.php?newsID=
news/newsletter.php?id=
news/shownewsarticle.php?articleid=
news/temp.php?id=
newsDetail.php?id=
newsite/pdf_show.php?id=
newsitem.php?newsid=
newsitem.php?newsID=
newsItem.php?newsId=
newsitem.php?num=
newsone.php?id=
NickServ registration passwords
nota.php?abre=
nota.php?adresa=
nota.php?b=
nota.php?base_dir=
nota.php?basepath=
nota.php?category=
nota.php?channel=
nota.php?chapter=
nota.php?cmd=
nota.php?content=
nota.php?corpo=
nota.php?destino=
nota.php?disp=
nota.php?doshow=
nota.php?eval=
nota.php?filepath=
nota.php?get=
nota.php?goFile=
nota.php?h=
nota.php?header=
nota.php?home=
nota.php?in=
nota.php?inc=
nota.php?include=
nota.php?ir=
nota.php?itemnav=
nota.php?ki=
nota.php?lang=
nota.php?left=
nota.php?link=
nota.php?m=
nota.php?mid=
nota.php?mod=
nota.php?modo=
nota.php?module=
nota.php?n=
nota.php?nivel=
nota.php?oldal=
nota.php?opcion=
nota.php?OpenPage=
nota.php?option=
nota.php?pag=
nota.php?pagina=
nota.php?panel=
nota.php?pg=
nota.php?play=
nota.php?pollname=
nota.php?pr=
nota.php?pre=
nota.php?qry=
nota.php?rub=
nota.php?sec=
nota.php?secc=
nota.php?seccion=
nota.php?second=
nota.php?seite=
nota.php?sekce=
nota.php?showpage=
nota.php?subject=
nota.php?t=
nota.php?tipo=
nota.php?url=
nota.php?v=
noticias.php?arq=
notify/notify_form.php?topic_id=
Novell NetWare intext:"netware management portal version"
nurl:/admin/login.asp
nyheder.htm?show=
obio/detail.php?id=
ogl_inet.php?ogl_id=
ogloszenia/rss.php?cat=
old_reports.php?file=
onlinesales/product.php?product_id=
opinions.php?id=
ORA-00921: unexpected end of SQL command
ORA-00936: missing expression
order.asp?lotid=
order.php?BookID=
order.php?id=
order.php?item_ID=
OrderForm.php?Cart=
ourblog.php?categoryid=
Outlook Web Access (a better way)
ov_tv.php?item=
OWA Public Folders (direct view)
packages_display.php?ref=
padrao.php?*[*]*=
padrao.php?*root*=
padrao.php?a=
padrao.php?abre=
padrao.php?addr=
padrao.php?base_dir=
padrao.php?basepath=
padrao.php?body=
padrao.php?c=
padrao.php?choix=
padrao.php?cont=
padrao.php?corpo=
padrao.php?d=
padrao.php?destino=
padrao.php?eval=
padrao.php?filepath=
padrao.php?h=
padrao.php?header=
padrao.php?incl=
padrao.php?index=
padrao.php?ir=
padrao.php?link=
padrao.php?loc=
padrao.php?menu=
padrao.php?menue=
padrao.php?mid=
padrao.php?middle=
padrao.php?n=
padrao.php?name=
padrao.php?nivel=
padrao.php?oldal=
padrao.php?op=
padrao.php?open=
padrao.php?OpenPage=
padrao.php?pag=
padrao.php?page=
padrao.php?path=
padrao.php?pname=
padrao.php?pre=
padrao.php?qry=
padrao.php?read=
padrao.php?redirect=
padrao.php?rub=
padrao.php?secao=
padrao.php?secc=
padrao.php?seccion=
padrao.php?section=
padrao.php?seite=
padrao.php?sekce=
padrao.php?sivu=
padrao.php?str=
padrao.php?strona=
padrao.php?subject=
padrao.php?texto=
padrao.php?tipo=
padrao.php?type=
padrao.php?u=
padrao.php?url=
padrao.php?var=
padrao.php?xlink=
page.php?*[*]*=
page.php?abre=
page.php?action=
page.php?addr=
page.php?adresa=
page.php?area_id=
page.php?base_dir=
page.php?chapter=
page.php?choix=
page.php?cmd=
page.php?cont=
page.php?doc=
page.php?e=
page.php?ev=
page.php?eval=
page.php?file=
page.php?g=
page.php?go=
page.php?goto=
page.php?id=
page.php?inc=
page.php?incl=
page.php?ir=
page.php?left=
page.php?link=
page.php?load=
page.php?loader=
page.php?mid=
page.php?middle=
page.php?mod=
page.php?modo=
page.php?modul=
page.php?module=
page.php?numero=
page.php?oldal=
page.php?OpenPage=
page.php?option=
page.php?p=
page.php?pa=
page.php?panel=
page.php?PartID=
page.php?phpbb_root_path=
page.php?pId=
page.php?pname=
page.php?pref=
page.php?q=
page.php?qry=
page.php?read=
page.php?recipe=
page.php?redirect=
page.php?secao=
page.php?section=
page.php?seite=
page.php?showpage=
page.php?sivu=
page.php?strona=
page.php?subject=
page.php?tipo=
page.php?url=
page.php?where=
page.php?z=
page/de/produkte/produkte.php?prodID=
page/venue.php?id=
pageid=
pages.php?ID=
pages.php?id=
pages.php?page=
pages/print.php?id=
pages/video.php?id=
Pages/whichArticle.php?id=
pagina.php?base_dir=
pagina.php?basepath=
pagina.php?category=
pagina.php?channel=
pagina.php?chapter=
pagina.php?choix=
pagina.php?cmd=
pagina.php?dir=
pagina.php?ev=
pagina.php?filepath=
pagina.php?g=
pagina.php?go=
pagina.php?goto=
pagina.php?header=
pagina.php?home=
pagina.php?id=
pagina.php?in=
pagina.php?incl=
pagina.php?include=
pagina.php?index=
pagina.php?ir=
pagina.php?k=
pagina.php?lang=
pagina.php?left=
pagina.php?link=
pagina.php?load=
pagina.php?loader=
pagina.php?loc=
pagina.php?mid=
pagina.php?middlePart=
pagina.php?modo=
pagina.php?my=
pagina.php?n=
pagina.php?nivel=
pagina.php?numero=
pagina.php?oldal=
pagina.php?OpenPage=
pagina.php?pagina=
pagina.php?panel=
pagina.php?path=
pagina.php?pr=
pagina.php?pre=
pagina.php?q=
pagina.php?read=
pagina.php?recipe=
pagina.php?ref=
pagina.php?sec=
pagina.php?secao=
pagina.php?seccion=
pagina.php?section=
pagina.php?sekce=
pagina.php?start=
pagina.php?str=
pagina.php?thispage=
pagina.php?tipo=
pagina.php?to=
pagina.php?type=
pagina.php?u=
pagina.php?v=
pagina.php?z=
participant.php?id=
passlist
passlist.txt (a better way)
passwd
passwd / etc (reliable)
past-event.php?id=
path.php?*[*]*=
path.php?action=
path.php?addr=
path.php?adresa=
path.php?body=
path.php?category=
path.php?channel=
path.php?chapter=
path.php?cmd=
path.php?destino=
path.php?disp=
path.php?doshow=
path.php?ev=
path.php?eval=
path.php?filepath=
path.php?goto=
path.php?header=
path.php?home=
path.php?id=
path.php?in=
path.php?incl=
path.php?ir=
path.php?left=
path.php?link=
path.php?load=
path.php?loader=
path.php?menue=
path.php?mid=
path.php?middle=
path.php?middlePart=
path.php?my=
path.php?nivel=
path.php?numero=
path.php?opcion=
path.php?option=
path.php?p=
path.php?pageweb=
path.php?panel=
path.php?path=
path.php?play=
path.php?pname=
path.php?pre=
path.php?pref=
path.php?qry=
path.php?recipe=
path.php?sec=
path.php?secao=
path.php?sivu=
path.php?sp=
path.php?start=
path.php?strona=
path.php?subject=
path.php?thispage=
path.php?tipo=
path.php?type=
path.php?var=
path.php?where=
path.php?xlink=
path.php?y=
payment.php?CartID=
pdetail.php?item_id=
pdf_post.php?ID=
people.lst
Peoples MSN contact lists
person.php?id=
pharmaxim/category.php?cid=
photogallery.php?id=
PhotoPost PHP Upload
PHP application warnings failing "include_path"
php-addressbook "This is the addressbook for *" -warning
php/event.php?id=
php/index.php?id=
PHPhotoalbum Statistics
PHPhotoalbum Upload
phpOpenTracker" Statistics
phpwcms/include/inc_ext/spaw/dialogs/table.php?spaw_root=
phpx?PageID
picgallery/category.php?cid=
pivot/modules/module_db.php?pivot_path=
play_old.php?id=
Please enter a valid password! inurl:polladmin
podcast/item.php?pid=
poem_list.php?bookID=
ponuky/item_show.php?ID=
pop.php?id=
port.php?content=
portafolio/portafolio.php?id=
post.php?id=
powersearch.php?CartId=
press_release.php?id=
press.php?*[*]*=
press.php?*root*=
press.php?abre=
press.php?addr=
press.php?base_dir=
press.php?category=
press.php?channel=
press.php?destino=
press.php?dir=
press.php?ev=
press.php?get=
press.php?goFile=
press.php?home=
press.php?i=
press.php?id=
press.php?inc=
press.php?incl=
press.php?include=
press.php?ir=
press.php?itemnav=
press.php?lang=
press.php?link=
press.php?loader=
press.php?menu=
press.php?mid=
press.php?middle=
press.php?modo=
press.php?module=
press.php?my=
press.php?nivel=
press.php?opcion=
press.php?OpenPage=
press.php?option=
press.php?pa=
press.php?page=
press.php?pageweb=
press.php?pagina=
press.php?panel=
press.php?param=
press.php?path=
press.php?pg=
press.php?pname=
press.php?pr=
press.php?pref=
press.php?redirect=
press.php?rub=
press.php?second=
press.php?seite=
press.php?strona=
press.php?subject=
press.php?t=
press.php?thispage=
press.php?to=
press.php?type=
press.php?where=
press.php?xlink=
prev_results.php?prodID=
preview.php?id=
price.php
principal.php?abre=
principal.php?addr=
principal.php?b=
principal.php?basepath=
principal.php?choix=
principal.php?cont=
principal.php?conteudo=
principal.php?corpo=
principal.php?d=
principal.php?destino=
principal.php?disp=
principal.php?ev=
principal.php?eval=
principal.php?f=
principal.php?filepath=
principal.php?goto=
principal.php?header=
principal.php?home=
principal.php?id=
principal.php?in=
principal.php?inc=
principal.php?index=
principal.php?ir=
principal.php?ki=
principal.php?l=
principal.php?left=
principal.php?link=
principal.php?load=
principal.php?loader=
principal.php?loc=
principal.php?menue=
principal.php?middle=
principal.php?middlePart=
principal.php?module=
principal.php?my=
principal.php?n=
principal.php?nivel=
principal.php?oldal=
principal.php?opcion=
principal.php?p=
principal.php?pag=
principal.php?pagina=
principal.php?param=
principal.php?phpbb_root_path=
principal.php?pollname=
principal.php?pr=
principal.php?pre=
principal.php?pref=
principal.php?q=
principal.php?read=
principal.php?recipe=
principal.php?ref=
principal.php?rub=
principal.php?s=
principal.php?secc=
principal.php?seccion=
principal.php?seite=
principal.php?strona=
principal.php?subject=
principal.php?tipo=
principal.php?to=
principal.php?type=
principal.php?url=
principal.php?viewpage=
principal.php?w=
principal.php?z=
print-story.php?id=
print.php?*root*=
print.php?addr=
print.php?base_dir=
print.php?basepath=
print.php?category=
print.php?chapter=
print.php?choix=
print.php?cont=
print.php?dir=
print.php?disp=
print.php?doshow=
print.php?g=
print.php?goFile=
print.php?goto=
print.php?header=
print.php?id=
print.php?ID=
print.php?in=
print.php?inc=
print.php?itemnav=
print.php?ki=
print.php?l=
print.php?left=
print.php?link=
print.php?loc=
print.php?menu=
print.php?menue=
print.php?middle=
print.php?middlePart=
print.php?module=
print.php?my=
print.php?name=
print.php?numero=
print.php?opcion=
print.php?open=
print.php?OpenPage=
print.php?option=
print.php?pag=
print.php?page=
print.php?param=
print.php?path=
print.php?play=
print.php?pname=
print.php?pollname=
print.php?pre=
print.php?r=
print.php?read=
print.php?rub=
print.php?s=
print.php?sekce=
print.php?sid=
print.php?sivu=
print.php?sp=
print.php?str=
print.php?strona=
print.php?thispage=
print.php?tipo=
print.php?type=
print.php?u=
print.php?where=
printcards.php?ID=
privacy.php?cartID=
private key files (.csr)
private key files (.key)
prod_detail.php?id=
prod_info.php?id=
prod.php?cat=
prodbycat.php?intCatalogID=
proddetails_print.php?prodid=
prodetails.php?prodid=
prodlist.php?catid=
prodotti.php?id_cat=
product_detail.php?product_id=
product_details.php?id=
product_details.php?prodid=
product_details.php?product_id=
product_info.php?id=
product_info.php?item_id=
product_info.php?products_id=
product_ranges_view.php?ID=
product-item.php?id=
product-list.php?category_id=
product-list.php?cid=
product-list.php?id=
product-range.php?rangeID=
product.php?****=
product.php?bid=
product.php?bookID=
product.php?cat=
product.php?id_h=
product.php?id=
product.php?intProdID=
product.php?intProductID=
product.php?ItemID=
product.php?ItemId=
product.php?pid=
product.php?prd=
product.php?prodid=
product.php?product_id=
product.php?product=
product.php?ProductID=
product.php?productid=
product.php?shopprodid=
product.php?sku=
product/detail.php?id=
product/list.php?pid=
product/product.php?cate=
product/product.php?product_no=
productdetail.php?id=
productDetails.php?idProduct=
productDisplay.php
productinfo.php?id=
productinfo.php?item=
productList.php?cat=
productlist.php?fid=
productlist.php?grpid=
productlist.php?id=
ProductList.php?id=
productList.php?id=
productlist.php?tid=
productlist.php?ViewType=Category&CategoryID=
productpage.php
products_category.php?CategoryID=
products_detail.php?CategoryID=
products-display-details.php?prodid=
products.php?act=
products.php?cat_id=
products.php?cat=
products.php?categoryID=
products.php?catid=
products.php?DepartmentID=
products.php?groupid=
products.php?ID=
products.php?keyword=
products.php?openparent=
products.php?p=
products.php?rub=
products.php?type=
products/?catID=
products/Blitzball.htm?id=
products/card.php?prodID=
products/index.php?rangeid=
products/parts/detail.php?id=
products/product-list.php?id=
products/product.php?id=
products/product.php?pid=
products/products.php?p=
productsByCategory.php?intCatalogID=
productsview.php?proid=
produit.php?id=
prodView.php?idProduct=
profile_print.php?id=
profile_view.php?id=
profile.php?id=
profiles/profile.php?profileid=
projdetails.php?id=
projects/event.php?id=
promo.php?id=
promotion.php?catid=
properties.php?id_cat=
property.php?id=
psyBNC config files
psychology/people/detail.php?id=
pub/pds/pds_view.php?start=
publications.php?Id=
publications.php?id=
publications.php?ID=
publications/book_reviews/full_review.php?id=
publications/publication.php?id=
publications/view.php?id=
purelydiamond/products/category.php?cat=
pview.php?Item=
pwd.db
pylones/item.php?item=
questions.php?questionid=
Quicken data files
rating.php?id=
rating/stat.php?id=
ray.php?id=
rdbqds -site:.edu -site:.mil -site:.gov
read.php?id=
readnews.php?id=
reagir.php?num=
recipe/category.php?cid=
redaktion/whiteteeth/detail.php?nr=
RedKernel"
referral/detail.php?siteid=
releases_headlines_details.php?id=
releases.php?id=
remixer.php?id=
reply.php?id=
resellers.php?idCategory=
resources/detail.php?id=
resources/index.php?cat=
resources/vulnerabilities_list.php?id=
results.php?cat=
review.php?id=
review/review_form.php?item_id=
reviews.php?id=
robots.txt
rounds-detail.php?id=
rss.php?cat=
rss/event.php?id=
rtfe.php?siteid=
rub.php?idr=
s.php?w=
Sales/view_item.php?id=
savecart.php?CartId=
schule/termine.php?view=
search.php?CartID=
search.php?cutepath=
search/display.php?BookID=
searchcat.php?search_id=
section.php?id=
section.php?section=
select_biblio.php?id=
Select_Item.php?id=
sem.php3?id=
send_reminders.php?includedir=
server-dbs "intitle:index of"
Services.php?ID=
services.php?page=
shippinginfo.php?CartId=
shop_category.php?id=
shop_details.php?prodid=
shop_display_products.php?cat_id=
shop.php?a=
shop.php?action=
shop.php?bookid=
shop.php?cartID=
shop.php?do=part&id=
shop/books_detail.php?bookID=
shop/category.php?cat_id=
shop/eventshop/product_detail.php?itemid=
Shop/home.php?cat=
shop/home.php?cat=
shop/index.php?cPath=
shopaddtocart.php
shopaddtocart.php?catalogid=
shopbasket.php?bookid=
shopbycategory.php?catid=
shopcafe-shop-product.php?bookId=
shopcart.php?title=
shopcreatorder.php
shopcurrency.php?cid=
shopdc.php?bookid=
shopdisplaycategories.php
shopdisplayproduct.php?catalogid=
shopdisplayproducts.php
shopexd.php
shopexd.php?catalogid=
shopping_basket.php?cartID=
shopping.php?id=
shopprojectlogin.php
shopquery.php?catalogid=
shopremoveitem.php?cartid=
shopreviewadd.php?id=
shopreviewlist.php?id=
ShopSearch.php?CategoryID=
shoptellafriend.php?id=
shopthanks.php
shopwelcome.php?title=
show_an.php?id=
show_bug.cgi?id=
show_item_details.php?item_id=
show_item.php?id=
show_news.php?cutepath=
show-book.php?id=
show.php?*root*=
show.php?abre=
show.php?adresa=
show.php?b=
show.php?base_dir=
show.php?channel=
show.php?chapter=
show.php?cmd=
show.php?corpo=
show.php?d=
show.php?disp=
show.php?filepath=
show.php?get=
show.php?go=
show.php?header=
show.php?home=
show.php?id=
show.php?inc=
show.php?incl=
show.php?include=
show.php?index=
show.php?ir=
show.php?j=
show.php?ki=
show.php?l=
show.php?left=
show.php?loader=
show.php?m=
show.php?mid=
show.php?middlePart=
show.php?modo=
show.php?module=
show.php?my=
show.php?n=
show.php?nivel=
show.php?oldal=
show.php?page=
show.php?pageweb=
show.php?pagina=
show.php?param=
show.php?path=
show.php?play=
show.php?pname=
show.php?pre=
show.php?qry=
show.php?r=
show.php?read=
show.php?recipe=
show.php?redirect=
show.php?seccion=
show.php?second=
show.php?sp=
show.php?thispage=
show.php?to=
show.php?type=
show.php?x=
show.php?xlink=
show.php?z=
showbook.php?bookid=
showfeature.php?id=
showimg.php?id=
showproduct.php?cat=
showproduct.php?prodid=
showproduct.php?productId=
showStore.php?catID=
showsub.php?id=
shprodde.php?SKU=
shredder-categories.php?id=
signin filetype:url
sinformer/n/imprimer.php?id=
singer/detail.php?siteid=
site:.pk intext:Warning: mysql_fetch_array(): supplied argument is not a valid MySQL result resource in & “id”
site:.pk intext:Warning: mysql_free_result(): supplied argument is not a valid MySQL result resource in & “id”
site:edu admin grades
site:netcraft.com intitle:That.Site.Running Apache
site:www.mailinator.com inurl:ShowMail.do
site.php?id=
site/?details&prodid=
site/en/list_service.php?cat=
site/products.php?prodid=
sitebuildercontent
sitebuilderfiles
sitebuilderpictures
sitio.php?*root*=
sitio.php?abre=
sitio.php?addr=
sitio.php?body=
sitio.php?category=
sitio.php?chapter=
sitio.php?content=
sitio.php?destino=
sitio.php?disp=
sitio.php?doshow=
sitio.php?e=
sitio.php?ev=
sitio.php?get=
sitio.php?go=
sitio.php?goFile=
sitio.php?inc=
sitio.php?incl=
sitio.php?index=
sitio.php?ir=
sitio.php?left=
sitio.php?menu=
sitio.php?menue=
sitio.php?mid=
sitio.php?middlePart=
sitio.php?modo=
sitio.php?name=
sitio.php?nivel=
sitio.php?oldal=
sitio.php?opcion=
sitio.php?option=
sitio.php?pageweb=
sitio.php?param=
sitio.php?pg=
sitio.php?pr=
sitio.php?qry=
sitio.php?r=
sitio.php?read=
sitio.php?recipe=
sitio.php?redirect=
sitio.php?rub=
sitio.php?sec=
sitio.php?secao=
sitio.php?secc=
sitio.php?section=
sitio.php?sivu=
sitio.php?sp=
sitio.php?start=
sitio.php?strona=
sitio.php?t=
sitio.php?texto=
sitio.php?tipo=
sitio/item.php?idcd=
skins/advanced/advanced1.php?pluginpath[0]=
skunkworks/content.php?id=
smarty_config.php?root_dir=
Snitz! forums db path error
socsci/events/full_details.php?id=
socsci/news_items/full_story.php?id=
software_categories.php?cat_id=
solpot.html?body=
sources/join.php?FORM[url]=owned&CONFIG[captcha]=1&CONFIG[path]=
specials.php?id=
specials.php?osCsid=
sport.php?revista=
spr.php?id=
spwd.db / passwd
SQL data dumps
SQL syntax error
sql.php?id=
SQuery/lib/gore.php?libpath=
Squid cache server reports
staff_id=
staff/publications.php?sn=
standard.php?*[*]*=
standard.php?abre=
standard.php?action=
standard.php?base_dir=
standard.php?body=
standard.php?channel=
standard.php?chapter=
standard.php?cmd=
standard.php?cont=
standard.php?destino=
standard.php?dir=
standard.php?e=
standard.php?ev=
standard.php?eval=
standard.php?go=
standard.php?goFile=
standard.php?goto=
standard.php?home=
standard.php?in=
standard.php?include=
standard.php?index=
standard.php?j=
standard.php?lang=
standard.php?link=
standard.php?menu=
standard.php?middle=
standard.php?my=
standard.php?name=
standard.php?numero=
standard.php?oldal=
standard.php?op=
standard.php?open=
standard.php?pagina=
standard.php?panel=
standard.php?param=
standard.php?phpbb_root_path=
standard.php?pollname=
standard.php?pr=
standard.php?pre=
standard.php?pref=
standard.php?q=
standard.php?qry=
standard.php?ref=
standard.php?s=
standard.php?secc=
standard.php?seccion=
standard.php?section=
standard.php?showpage=
standard.php?sivu=
standard.php?str=
standard.php?subject=
standard.php?url=
standard.php?var=
standard.php?viewpage=
standard.php?w=
standard.php?where=
standard.php?xlink=
standard.php?z=
start.php?*root*=
start.php?abre=
start.php?addr=
start.php?adresa=
start.php?b=
start.php?base_dir=
start.php?basepath=
start.php?body=
start.php?chapter=
start.php?cmd=
start.php?corpo=
start.php?destino=
start.php?eval=
start.php?go=
start.php?header=
start.php?home=
start.php?in=
start.php?include=
start.php?index=
start.php?ir=
start.php?lang=
start.php?load=
start.php?loader=
start.php?mid=
start.php?modo=
start.php?module=
start.php?name=
start.php?nivel=
start.php?o=
start.php?oldal=
start.php?op=
start.php?option=
start.php?p=
start.php?pageweb=
start.php?panel=
start.php?param=
start.php?pg=
start.php?play=
start.php?pname=
start.php?pollname=
start.php?rub=
start.php?secao=
start.php?seccion=
start.php?seite=
start.php?showpage=
start.php?sivu=
start.php?sp=
start.php?str=
start.php?strona=
start.php?thispage=
start.php?tipo=
start.php?where=
start.php?xlink=
stat.php?id=
static.php?id=
stockists_list.php?area_id=
store_bycat.php?id=
store_listing.php?id=
Store_ViewProducts.php?Cat=
store-details.php?id=
store.php?cat_id=
store.php?id=
store/default.php?cPath=
store/description.php?iddesc=
store/home.php?cat=
store/index.php?cat_id=
store/product.php?productid=
store/view_items.php?id=
storefront.php?id=
storefronts.php?title=
storeitem.php?item=
storemanager/contents/item.php?page_code=
StoreRedirect.php?ID=
story.php?id=
Stray-Questions-View.php?num=
sub*.php?*[*]*=
sub*.php?*root*=
sub*.php?abre=
sub*.php?action=
sub*.php?adresa=
sub*.php?b=
sub*.php?base_dir=
sub*.php?basepath=
sub*.php?body=
sub*.php?category=
sub*.php?channel=
sub*.php?chapter=
sub*.php?cont=
sub*.php?content=
sub*.php?corpo=
sub*.php?destino=
sub*.php?g=
sub*.php?go=
sub*.php?goFile=
sub*.php?header=
sub*.php?id=
sub*.php?include=
sub*.php?ir=
sub*.php?itemnav=
sub*.php?j=
sub*.php?k=
sub*.php?lang=
sub*.php?left=
sub*.php?link=
sub*.php?load=
sub*.php?menue=
sub*.php?mid=
sub*.php?middle=
sub*.php?mod=
sub*.php?modo=
sub*.php?module=
sub*.php?my=
sub*.php?name=
sub*.php?oldal=
sub*.php?op=
sub*.php?open=
sub*.php?OpenPage=
sub*.php?option=
sub*.php?pa=
sub*.php?pag=
sub*.php?panel=
sub*.php?path=
sub*.php?phpbb_root_path=
sub*.php?play=
sub*.php?pname=
sub*.php?pre=
sub*.php?qry=
sub*.php?recipe=
sub*.php?rub=
sub*.php?s=
sub*.php?sec=
sub*.php?secao=
sub*.php?secc=
sub*.php?seite=
sub*.php?sp=
sub*.php?str=
sub*.php?thispage=
sub*.php?u=
sub*.php?viewpage=
sub*.php?where=
sub*.php?z=
subcategories.php?id=
summary.php?PID=
Supplied argument is not a valid PostgreSQL result
support/mailling/maillist/inc/initdb.php?absolute_path=
sw_comment.php?id=
tas/event.php?id=
tecdaten/showdetail.php?prodid=
tek9.php?
template.php?*[*]*=
template.php?a=
template.php?Action=Item&pid=
template.php?addr=
template.php?base_dir=
template.php?basepath=
template.php?c=
template.php?choix=
template.php?cont=
template.php?content=
template.php?corpo=
template.php?dir=
template.php?doshow=
template.php?e=
template.php?f=
template.php?goto=
template.php?h=
template.php?header=
template.php?ir=
template.php?k=
template.php?lang=
template.php?left=
template.php?load=
template.php?menue=
template.php?mid=
template.php?mod=
template.php?name=
template.php?nivel=
template.php?op=
template.php?opcion=
template.php?pag=
template.php?page=
template.php?pagina=
template.php?panel=
template.php?param=
template.php?path=
template.php?play=
template.php?pre=
template.php?qry=
template.php?ref=
template.php?s=
template.php?secao=
template.php?second=
template.php?section=
template.php?seite=
template.php?sekce=
template.php?showpage=
template.php?sp=
template.php?str=
template.php?t=
template.php?texto=
template.php?thispage=
template.php?tipo=
template.php?viewpage=
template.php?where=
template.php?y=
templet.php?acticle_id=
test.php?page=
theme.php?id=
things-to-do/detail.php?id=
today.php?eventid=
tools/print.php?id=
tools/send_reminders.php?includedir=
top10.php?cat=
topic.php?ID=
toynbeestudios/content.php?id=
tradeCategory.php?id=
trailer.php?id=
trainers.php?id=
transcript.php?id=
trillian.ini
tuangou.php?bookid=
type.php?iType=
UBB.threads")|(inurl:login.php "ubb")
UebiMiau" -site:sourceforge.net
Ultima Online loginservers
Unreal IRCd
updatebasket.php?bookid=
updates.php?ID=
usb/devices/showdev.php?id=
veranstaltungen/detail.php?id=
video.php?content=
video.php?id=
view_author.php?id=
view_cart.php?title=
view_detail.php?ID=
view_faq.php?id=
view_item.php?id=
view_item.php?item=
view_items.php?id=
view_newsletter.php?id=
view_product.php?id=
view-event.php?id=
view.php?*[*]*=
view.php?adresa=
view.php?b=
view.php?body=
view.php?channel=
view.php?chapter=
view.php?choix=
view.php?cid=
view.php?cmd=
view.php?content=
view.php?disp=
view.php?get=
view.php?go=
view.php?goFile=
view.php?goto=
view.php?header=
view.php?id=
view.php?incl=
view.php?ir=
view.php?ki=
view.php?lang=
view.php?load=
view.php?loader=
view.php?mid=
view.php?middle=
view.php?mod=
view.php?oldal=
view.php?option=
view.php?pag=
view.php?page=
view.php?pageNum_rscomp=
view.php?panel=
view.php?pg=
view.php?phpbb_root_path=
view.php?pollname=
view.php?pr=
view.php?qry=
view.php?recipe=
view.php?redirect=
view.php?sec=
view.php?secao=
view.php?seccion=
view.php?second=
view.php?seite=
view.php?showpage=
view.php?sp=
view.php?str=
view.php?to=
view.php?type=
view.php?u=
view.php?var=
view.php?where=
view/7/9628/1.html?reply=
viewapp.php?id=
viewcart.php?CartId=
viewCart.php?userID=
viewCat_h.php?idCategory=
viewevent.php?EventID=
viewitem.php?recor=
viewphoto.php?id=
viewPrd.php?idcategory=
ViewProduct.php?misc=
viewshowdetail.php?id=
viewthread.php?tid=
voteList.php?item_ID=
wamp_dir/setup/yesno.phtml?no_url=
warning "error on line" php sablotron
WebLog Referrers
website.php?id=
Welcome to ntop!
whatsnew.php?idCategory=
wiki/pmwiki.php?page****=
Windows 2000 web server error messages
WsAncillary.php?ID=
WsPages.php?ID=noticiasDetalle.php?xid=
www/index.php?page=
wwwboard WebAdmin inurl:passwd.txt wwwboard|webadmin
WWWThreads")|(inurl:"wwwthreads/login.php")|(inurl:"wwwthreads/login.pl?Cat=")
XOOPS Custom Installation
yacht_search/yacht_view.php?pid=
YZboard/view.php?id=
zb/view.php?uid=
zentrack/index.php?configFile=
2020 Google Dorks List
site:accounts..com/signin/ intitle:"index of" drupal intitle:"index of" admin inurl:login.cgi Pages Containing Login Portals site:/joomla/administrator
inurl:/login/index.jsp -site:hertz.*
intitle:"Index of" inurl:wp-json/oembed
intitle:"Index of" phpmyadmin
intitle:"Index of" wp-admin
intitle:index.of.?.sql
inurl: /filemanager/dialog.php
s3 site:amazonaws.com filetype:log
inurl:cgi/login.pl
inurl:zoom.us/j and intext:scheduled for
site:*/auth intitle:login
nurl: admin/login.aspx Pages Containing Login Portals
"Index of" inurl:webalizer
"Index of" inurl:phpmyadmin
"Index of" inurl:htdocs inurl:xampp
s3 site:amazonaws.com intext:dhcp filetype:txt inurl:apollo
inurl:/index.aspx/login
site:amazonaws.com inurl:login.php
intitle:"IIS Windows Server" -inurl:"IIS Windows Server"
intitle:"Apache2 Ubuntu Default Page: It works"
inurl:/filedown.php?file=
inurl:Dashboard.jspa intext:"Atlassian Jira Project Management Software"
inurl:app/kibana intext:Loading Kibana
site:https://docs.google.com/spreadsheets edit
inurl:8443 AND -intitle:8443 AND -intext:8443 prohibited|restricted|unauthorized
intitle:"index of" unattend.xml
inurl:/admin/index.php
inurl:bc.googleusercontent.com intitle:index of
inurl:office365 AND intitle:"Sign In | Login | Portal"
intext:"@gmail.com" AND intext:"@yahoo.com" filetype:sql
intitle:OmniDB intext:"user. pwd. Sign in."
intitle:"qBittorrent Web UI" inurl:8080
site:com inurl:jboss filetype:log -github.com
intitle:"index of" ".cpanel/caches/config/"
inurl:'/scopia/entry/index.jsp'
inurl:/index.aspx/login
intitle: "index of" "./" "./bitcoin"
inurl:/portal/apis/fileExplorer/
intitle:"index of" "/aws.s3/"
intitle:"index of" hosts.csv | firewalls.csv | linux.csv | windows.csv
intitle:Test Page for the Nginx HTTP Server on Fedora
inurl:_cpanel/forgotpwd
intitle:"index of /" intext:/backup
intitle:"Swagger UI - " + "Show/Hide"
site:drive.google.com /preview intext:movie inurl:flv | wmv | mp4 -pdf -edit -view
intext:"class JConfig {" inurl:configuration.php
"index of" "database.sql.zip"
The Google dorks list is a never-ending one and the list keeps on growing based on the new technologies and the vulnerabilities.
Conclusion
Google dorks is also known as Google hacking. We have tried our best to give you a most relevant Google Dorks list to query for best search results using about search operator and give you most of the information that is difficult to locate through simple search queries.
There are thousand of Google dorks are available online, here we have made a comprehensive list that helps you to test your network and helps to find more vulnerable sites.

