FBI’s Encrypted Phone Platform ANØM Infiltrated Hundreds of Criminal Syndicates; Result is Massive Worldwide Takedown
SAN DIEGO – A wave of hundreds of arrests that began in Australia and stretched across Europe culminated today with the unsealing of a federal grand jury indictment in San Diego charging 17 foreign nationals with distributing thousands of encrypted communication devices to criminal syndicates.
The 500-plus arrests that took place during a worldwide two-day takedown were possible because of a San Diego-based investigation like no other. For the first time, the FBI operated its own encrypted device company, called “ANOM,” which was promoted by criminal groups worldwide. These criminals sold more than 12,000 ANOM encrypted devices and services to more than 300 criminal syndicates operating in more than 100 countries, including Italian organized crime, Outlaw Motorcycle Gangs, and various international drug trafficking organizations, according to court records.
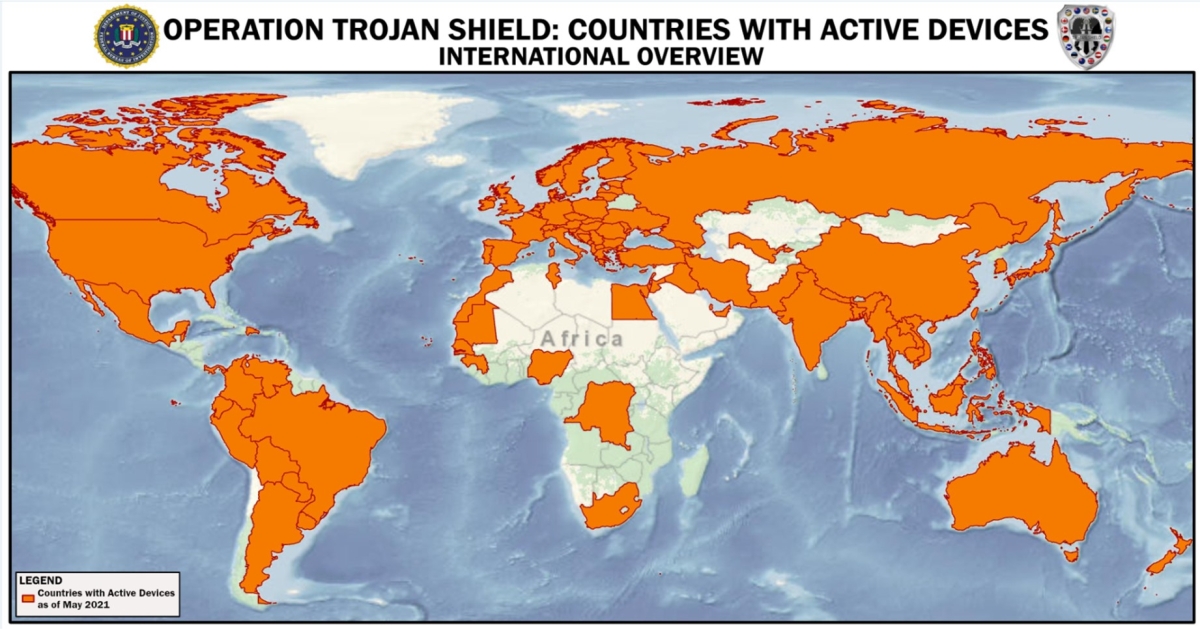
During the course of the investigation, while ANOM’s criminal users unknowingly promoted and communicated on a system operated lawfully by the FBI, agents catalogued more than 27 million messages between users around the world who had their criminal discussions reviewed, recorded, and translated by the FBI, until the platform was taken down yesterday.
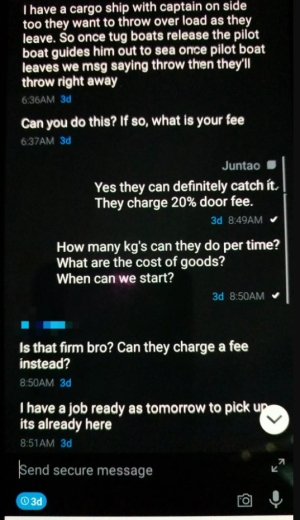
The users, believing their ANOM devices were protected from law enforcement by the shield of impenetrable encryption, openly discussed narcotics concealment methods, shipments of narcotics, money laundering, and in some groups—violent threats, the indictment said. Some users negotiated drug deals via these encrypted messages and sent pictures of drugs, in one instance hundreds of kilograms of cocaine concealed in shipments of pineapples and bananas, and in another instance, in cans of tuna, in order to evade law enforcement.
The indictment charges 17 alleged distributors of the FBI’s devices and platform. They are charged with conspiring to violate the Racketeer Influenced and Corrupt Organizations Act (RICO), pertaining to their alleged involvement in marketing and distributing thousands of encrypted communication devices to transnational criminal organizations worldwide.
During the last 24 to 48 hours, in addition to the more than 500 arrests around the world, authorities searched more than 700 locations deploying more than 9,000 law enforcement officers worldwide and seized multi-ton quantities of illicit drugs.
CLICK HERE – Video Messages from International Partners
Grand totals for the entire investigation include 800 arrests; and seizures of more than 8 tons of cocaine; 22 tons of marijuana; 2 tons of methamphetamine/amphetamine; six tons of precursor chemicals; 250 firearms; and more than $48 million in various worldwide currencies. Dozens of public corruption cases have been initiated over the course of the investigation. And, during the course of the investigation, more than 50 clandestine drug labs have been dismantled. One of the labs hit yesterday was one of the largest clandestine labs in German history.
“This was an unprecedented operation in terms of its massive scale, innovative strategy and technological and investigative achievement,” said Acting U.S. Attorney Randy Grossman. “Hardened encrypted devices usually provide an impenetrable shield against law enforcement surveillance and detection. The supreme irony here is that the very devices that these criminals were using to hide from law enforcement were actually beacons for law enforcement. We aim to shatter any confidence in the hardened encrypted device industry with our indictment and announcement that this platform was run by the FBI.”


“Today marks the culmination of more than five years of innovative and complex investigative work strategically aimed to disrupt the encrypted communications space that caters to the criminal element,” said Suzanne Turner, Special Agent in Charge of the Federal Bureau of Investigation (FBI) – San Diego Field Office. “The FBI has brought together a network of dedicated international law enforcement partners who are steadfast in combating the global threat of organized crime. The immense and unprecedented success of Operation Trojan Shield should be a warning to international criminal organizations – your criminal communications may not be secure; and you can count on law enforcement worldwide working together to combat dangerous crime that crosses international borders.”
“Operation Trojan Shield is a perfect example of an OCDETF case – an investigation driven by intelligence and maximizing the strengths of partner law enforcement agencies in coordinated efforts to dismantle command and control elements of criminal networks,” said OCDETF Director Adam W. Cohen. “Coordination is the cornerstone of the OCDETF program, and the impressiveness of the combined efforts of the U.S. Attorney’s Office, FBI, and our foreign partners cannot be overstated. This effort has created lasting disruptive impacts to these transnational criminal organizations.”
“The AFP and FBI have been working together on a world-first operation to bring to justice the organised crime gangs flooding our communities with drugs, guns and violence,” said AFP Commissioner Reece Kershaw APM. “The FBI provided an encrypted communications platform while the AFP deployed the technical capability which helped unmask some of the biggest criminals in the world. This week the AFP and our state police partners will execute hundreds of warrants and we expect to arrest hundreds of offenders linked to the platform. This is the culmination of hard work, perseverance and an invaluable, trusted relationship with the FBI.
We thank the FBI for their long and integral partnership with the AFP.”
Europol’s Deputy Executive Director Jean-Philippe Lecouffe: “This operation is an exceptional success by the authorities in the United States, Sweden, the Netherlands, Australia, New Zealand and the other European members of the Operational Task Force. Europol coordinated the international law enforcement community, enriched the information picture and brought criminal intelligence into ongoing operations to target organised crime and drug trafficking organisations, wherever they are and however they choose to communicate. I am very satisfied to see Europol supporting this operation and strengthen law enforcement partnerships by emphasizing the multi-agency aspect of the case.”

“I am exceptionally proud of our New Zealand Police staff who supported Operation Trojan Shield,” said New Zealand Police Commissioner Andrew Coster. “This operation will have an unprecedented impact on organised crime syndicates across the globe. We value our strong relationship with the FBI, AFP and Europol and it is through these partnerships and the unrelenting efforts by law enforcement agencies from multiple countries that this operation has seen such incredible success This is a fantastic result and reiterates the importance of our transnational partnerships with law enforcement agencies across the globe in our common ongoing efforts to dismantle organised crime groups and the enormous harm they cause to our communities.”
“This remarkably successful operation demonstrates what can be accomplished when law enforcement agencies throughout the world work together,” said DEA Los Angeles Division Special Agent in Charge Bill Bodner. “Through strong relationships with our partners in more than 67 countries, professionals throughout the DEA, including experts in the Los Angeles Division, supported this unprecedented collaboration and our own mission to disrupt and dismantle the criminal organizations that profit from the distribution of illegal drugs.”
According to the San Diego indictment, ANOM’s administrators, distributors, and agents described the platform to potential users as “designed by criminals for criminals” and targeted the sale of ANOM to individuals that they knew participated in illegal activities.
All defendants are foreign nationals located outside of the U.S. In total, eight of the indicted defendants were taken into custody last night. Authorities are continuing to search for the remaining nine defendants.
The indictment alleges the defendants knew the devices they distributed were being used exclusively by criminals to coordinate drug trafficking and money laundering, including in the U.S. The defendants personally fielded “wipe requests” from users when devices fell into the hands of law enforcement.
The FBI’s review of ANOM users’ communications worked like a blind carbon copy function in an email. A copy of every message being sent from each device was sent to a server in a third-party country where the messages were collected and stored. The data was then provided to the FBI on a regular basis pursuant to an international cooperation agreement. Communications such as text messages, photos, audio messages, and other digital information were reviewed by the FBI for criminal activity and disseminated to partner law enforcement agencies in other countries. Each user was using ANOM for a criminal purpose. Those countries have built their own cases against ANOM users, many of whom were arrested in takedowns in Europe, Australia and New Zealand over the last several days.
Intelligence derived from the FBI’s communications platform presented opportunities to disrupt major drug trafficking, money laundering, and other criminal activity while the platform was active. For example, over 150 unique threats to human life were mitigated.
This operation was led by the FBI and coordinated with the U.S. Drug Enforcement Administration, the U.S. Marshals Service, Australian Federal Police, Swedish Police Authority, National Police of the Netherlands, Lithuanian Criminal Police Bureau, Europol, and numerous other law enforcement partners from over a dozen other countries.
This investigation began after Canada-based encrypted device company Phantom Secure was dismantled by the FBI in 2018 through a San Diego-based federal RICO indictment and court-authorized seizure of the Phantom Secure platform, forcing many criminals to seek other secret communication methods to avoid law enforcement detection. The FBI—along with substantial contributions by the Australian Federal Police—filled that void with ANOM.
When the FBI and the San Diego U.S. Attorney’s Office dismantled Sky Global in March 2021, the demand for ANOM devices grew exponentially as criminal users sought a new brand of hardened encryption device to plot their drug trafficking and money laundering transactions and to evade law enforcement. Demand for ANOM from criminal groups also increased after European investigators announced the dismantlement of the EncroChat platform in July 2020. The ANOM platform – unlike Phantom Secure, EncroChat, and Sky Global – was exploited by the FBI from the very beginning of ANOM’s existence and was not an infiltration of an existing popular encrypted communications company.
In October 2018, Phantom Secure’s CEO pleaded guilty to a RICO conspiracy in the Southern District of California. He was sentenced to nine years in prison and ordered to forfeit $80 million in proceeds from the sale of Phantom devices.
For further information, please see https://www.justice.gov/usao-sdca/pr/chief-executive-communications-company-sentenced-prison-providing-encryption-services and https://www.justice.gov/usao-sdca/pr/sky-global-executive-and-associate-indicted-providing-encrypted-communication-devices.
Operation Trojan Shield is an Organized Crime Drug Enforcement Task Forces (OCDETF) investigation. OCDETF identifies, disrupts, and dismantles the highest-level drug traffickers, money launderers, gangs, and transnational criminal organizations that threaten the United States by using a prosecutor-led, intelligence-driven, multi-agency approach that leverages the strengths of federal, state, and local law enforcement agencies against criminal networks.
Assistant U.S. Attorneys Meghan E. Heesch, Joshua C. Mellor, Shauna Prewitt, and Mikaela Weber of the U.S. Attorney’s Office for the Southern District of California are prosecuting the case, with assistance from Paralegal Specialist Tracie Jarvis. Former Assistant U.S. Attorney Andrew P. Young made invaluable contributions during his tenure on the case team.
Acting U.S. Attorney Grossman praised federal prosecutors and FBI agents and international law enforcement partners for their relentless pursuit of justice in this extraordinary case. Additionally, Acting U.S. Attorney Grossman thanked the coordinated efforts of the Department of Justice’s Office of International Affairs which facilitated many international components of this complex investigation.
The charges and allegations contained in an indictment are merely accusations, and the defendants are considered innocent unless and until proven guilty.
DEFENDANTS 21-CR-1623-JLS |
COUNTRY |
|---|---|
| *Joseph Hakan Ayik (1) | |
| Domenico Catanzariti (2) | Australia |
| *Maximilian Rivkin (3) | |
| Abdelhakim Aharchaou (4) | The Netherlands |
| *Seyyed Hossein Hosseini (5) | |
| Alexander Dmitrienko (6) | Spain |
| *Baris Tukel (7) | |
| *Erkan Yusef Dogan (8) | |
| *Shane Geoffrey May (9) | |
| Aurangzeb Ayub (10) | The Netherlands |
| James Thomas Flood (11) | Spain |
| *Srdjan Todorovic aka Dr. Djek (12) | |
| *Shane Ngakuru (13) | |
| Edwin Harmendra Kumar (14) | Australia |
| Omar Malik (15) | The Netherlands |
| Miwand Zakhimi (16) | The Netherlands |
| *Osemah Elhassen (17) | |
| *Fugitive |
SUMMARY OF CHARGES
Conspiracy to Conduct Enterprise Affairs Through Pattern of Racketeering Activity (RICO Conspiracy), in violation of 18 U.S.C. § 1962(d)
Maximum Penalty: Twenty years in prion
AGENCIES
Federal Bureau of Investigation
Drug Enforcement Administration
United States Marshals Service
Department of Justice, Office of International Affairs
Australian Federal Police
Swedish Police Authority
Lithuanian Criminal Police Bureau
National Police of the Netherlands
EUROPOL
For further information, please see
https://www.afp.gov.au/news-media/media-releases/afp-led-operation-ironside-smashes-organised-crime
Encrypted Phone Company Was Secretly Commandeered by FBI to Track Criminals’ GPS Data
The agency’s backdoor access to Anom phones collected the locations of users across the world, transferring the data to authorities.
FBI Sold Criminals Fake Encrypted Phones That Actually Copied Their Messages
The Anom company helped international law enforcement arrest over 800 suspected criminals in what marks the FBI’s latest attempt to overcome encryption.
An encrypted chat platform that catered to criminals is actually an FBI sting operation.
Since 2019, the FBI has been secretly operating Anom, a company that pretended to offer encrypted messaging to criminal organizations. In reality, the Anom app would relay to federal investigators a copy of every message sent.
The operation enabled the FBI and international law enforcement to arrest over 800 suspected criminals across the globe, according to Europol.
Anom ended up serving more than 12,000 devices belonging to over 300 criminal organizations, including the Italian mafia, outlaw motorcycle gangs, and crime syndicates based in Asia. The encrypted chat platform recorded messages covering assassination plots, mass drug trafficking, and illegal gun distribution.

The operation marks US law enforcement’s latest attempt to circumvent encryption on smartphones. For years now, the FBI has been urging Apple to create a backdoor into its iPhones, citing the need to collect evidence against suspected criminals. Apple has thus far refused, so the agency has contracted professional smartphone hacking services to help it unlock devices seized in investigations.
“When we took down Phantom Secure in 2018, we found the criminal organizations moved quickly to back-up options with other encrypted platforms,” said FBI San Diego Assistant Special Agent in Charge Jamie Arnold in a statement.
As a result, the FBI and its law enforcement partners attempted to fill the void with Anom. According to Vice, a confidential source who sold phones using Phantom Secure had been developing their own encrypted chat platform; the source then offered up the platform to the FBI, which began working to circulate Anom in criminal underground circles.
According to Australian Federal Police, the Anom encrypted messaging app was installed on special phones that had been stripped of other capabilities. “The mobile phones, which were bought on the black market, could not make calls or send emails. It could only send messages to another device that had the organized crime app. Criminals needed to know a criminal to get a device,” Australian Federal Police added.
To market itself, Anom also had its own YouTube, Twitter, Facebook, and Reddit pages, which advertised the app as a secure communications platform.
The FBI has since replaced the Anom.io website with a notice that says: “Law enforcement has been monitoring messages and attachments from the ANØM platform. A number of investigations have been initiated and are ongoing.” Users of Anom can learn if they’re under investigation by typing in their username and smartphone details into a form on the site. SOURCE
We Got the Phone the FBI Secretly Sold to Criminals
Unlocking the Google Pixel 4a with a PIN code reveals some common apps: Tinder, Instagram, Facebook, Netflix, and even Candy Crush. But none of those apps work, and tapping their icons doesn’t do anything. Resetting the phone and typing in another PIN opens up an entirely different section of the device, with a new background and new apps. Now in place of the old apps sit a clock, a calculator, and the device’s settings.
“Enter Anom ID” and a password, the screen reads. Hidden in the calculator is a concealed messaging app called Anom, which last month we learned was an FBI honeypot. On Anom, criminals believed they could communicate securely, with the app encrypting their messages. They were wrong: an international group of law enforcement agencies including the FBI were monitoring their messages and announced hundreds of arrests last month. International authorities have held press conferences to tout the operation’s success, but have provided few details on how the phones actually functioned.
Motherboard has obtained and analyzed an Anom phone from a source who unknowingly bought one on a classified ads site. On that site, the phone was advertised as just a cheap Android device. But when the person received it, they realized it wasn’t an ordinary phone, and after being contacted by Motherboard, found that it contained the secret Anom app.
The person Motherboard bought the phone from said they panicked “when I realised what I had just purchased.” Motherboard granted the person anonymity to protect them from any retaliation.
When booting up the phone, it displays a logo for an operating system called “ArcaneOS.” Very little information is publicly available on ArcaneOS. It’s this detail that has helped lead several people who have ended up with Anom phones to realize something was unusual about their device. Most posts online discussing the operating system appear to be written by people who have recently inadvertently bought an Anom device, and found it doesn’t work like an ordinary phone. After the FBI announced the Anom operation, some Anom users have scrambled to get rid of their device, including selling it to unsuspecting people online. The person Motherboard obtained the phone from was in Australia, where authorities initially spread the Anom devices as a pilot before expanding into other countries. They said they contacted the Australian Federal Police (AFP) in case the phone or the person who sold it was of interest to them; when the AFP didn’t follow up, the person agreed to sell the phone to Motherboard for the same price they paid. They said they originally bought it from a site similar to Craigslist.
Another person Motherboard spoke to who bought one of the phones said they were in Lithuania.
“I bought this phone online, for ridiculously low price, now I understand why,” that second person said. That person also provided Motherboard with photos and a video of their device. In that case, the Anom login screen appeared inaccessible, but other settings such as the decoy PIN code remained. “Probably this phone was used by some drug dealer :D,” they said.
For the past few months, members of Android hobbyist and developer forums have been trying to help the people who bought the strange phones return them to a usable state.
“I cannot install any apps because there is no [App Store], everything has been removed,” one person who said they bought the phone second-hand wrote on a German language forum in March, before the FBI and its partners stopped the operation.




