The Tor Browser takes online privacy to extremes. With an encrypted and anonymous connection, Tor helps you access the unindexed part of the internet known as the dark web. But how does this dark web browser work, and is it safe? Learn more about Tor and its pros and cons — then get Avast Secure Browser for cleaner and faster private browsing.
The Onion Router (Tor) is free and open-source software that allows users to browse the internet anonymously. Tor uses a peer-to-peer (P2P) overlay network that consists of over seven thousand relays. The network uses multiple layers of encryption to conceal the source and destination of information sent over the network.
Tor works by:
- Redirecting web traffic through a series of different routers known as nodes
- Hiding your IP address and browsing activity
- Encapsulating messages in layers of encryption
Tor was developed in the mid 1990s by US Naval Research Laboratory employees Paul Syverson, Michael Reed, and David Goldschlag. The original purpose of Tor was to protect the identity of US Navy intelligence agents.
Tor is legal in many places as long as it’s used with good intentions. However, misusing Tor could lead to problems.
Tor is different from a VPN because:
- Tor nodes are randomly allocated, making it difficult to choose a server location.
- VPN services provide servers in dozens of locations worldwide, allowing you to manually choose your preferred server location.
Inception
Tor was originally designed, implemented, and deployed as a third-generation onion routing project of the Naval Research Laboratory. It was originally developed with the U.S. Navy in mind, for the primary purpose of protecting government communications. Today, it is used every day for a wide variety of purposes by the military, journalists, law enforcement officers, activists, and many others. Here are some of the specific uses we’ve seen or recommend.
We need your good Tor stories! What do you use Tor for? Why do you need it? What has Tor done for you? We need your stories.

Normal people use Tor
- They protect their privacy from unscrupulous marketers and identity thieves. Internet Service Providers (ISPs) sell your Internet browsing records to marketers or anyone else willing to pay for it. ISPs typically say that they anonymize the data by not providing personally identifiable information, but this has proven incorrect. A full record of every site you visit, the text of every search you perform, and potentially userid and even password information can still be part of this data. In addition to your ISP, the websites (and search engines) you visit have their own logs, containing the same or more information.
- They protect their communications from irresponsible corporations. All over the Internet, Tor is being recommended to people newly concerned about their privacy in the face of increasing breaches and betrayals of private data. From lost backup tapes, to giving away the data to researchers, your data is often not well protected by those you are supposed to trust to keep it safe.
- They protect their children online. You’ve told your kids they shouldn’t share personally identifying information online, but they may be sharing their location simply by not concealing their IP address. Increasingly, IP addresses can be literally mapped to a city or even street location, and can reveal other information about how you are connecting to the Internet. In the United States, the government is pushing to make this mapping increasingly precise.
- They research sensitive topics. There’s a wealth of information available online. But perhaps in your country, access to information on AIDS, birth control, Tibetan culture, or world religions is behind a national firewall.
- They skirt surveillance. Even harmless web browsing can sometimes raise red flags for suspicious observers. Using Tor protects your privacy by making it extremely dificult for an observer to correlate the sites you visit with your physical-world identity.
- They circumvent censorship. If you live in a country that has ever blocked Facebook or Youtube, you might need to use Tor to get basic internet functionality.

Journalists and their audience use Tor
- Reporters without Borders tracks Internet prisoners of conscience and jailed or harmed journalists all over the world. They advise journalists, sources, bloggers, and dissidents to use Tor to ensure their privacy and safety.
- Tor is part of SecureDrop, an open-source whistleblower submission system that media organizations can use to securely accept documents from and communicate with anonymous sources. Many news organizations use SecureDrop, including the Associated Press, The Washington Post, The New York Times, The CBC, ProPublica, Dagbladet, and more.
- Tor preserves the ability of people behind national firewalls or under the surveillance of repressive regimes to obtain a global perspective on controversial topics including democracy, economics and religion.
- Citizen journalists in China use Tor to write about local events to encourage social change and political reform.
- Citizens and journalists in Internet black holes use Tor to research state propaganda and opposing viewpoints, to file stories with non-State controlled media, and to avoid risking the personal consequences of intellectual curiosity.
Law enforcement officers use Tor
- Online surveillance: Tor allows officials to surf questionable web sites and services without leaving tell-tale tracks. If the system administrator of an illegal gambling site, for example, were to see multiple connections from government or law enforcement IP addresses in usage logs, investigations may be hampered.
- Sting operations: Similarly, anonymity allows law officers to engage in online “undercover ” operations. Regardless of how good an undercover officer’s “street cred” may be, if the communications include IP ranges from police addresses, the cover is blown.
- Truly anonymous tip lines: While online anonymous tip lines are popular, without anonymity software, they are far less useful. Sophisticated sources understand that although a name or email address is not attached to information, server logs can identify them very quickly. As a result, tip line web sites that do not encourage anonymity are limiting the sources of their tips.

Activists & Whistleblowers use Tor
- Human rights activists use Tor to anonymously report abuses from danger zones. Internationally, labor rights workers use Tor and other forms of online and offline anonymity to organize workers in accordance with the Universal Declaration of Human Rights. Even though they are within the law, it does not mean they are safe. Tor provides the ability to avoid persecution while still raising a voice.
- When groups such as the Friends Service Committee and environmental groups are increasingly falling under surveillance in the United States under laws meant to protect against terrorism, many peaceful agents of change rely on Tor for basic privacy during legitimate activities.
- Human Rights Watch recommends Tor in their report, “ Race to the Bottom: Corporate Complicity in Chinese Internet Censorship.” The study co-author interviewed Roger Dingledine, Tor project leader, on Tor use. They cover Tor in the section on how to breach the “Great Firewall of China,” and recommend that human rights workers throughout the globe use Tor for “secure browsing and communications.”
- Tor has consulted with and volunteered help to Amnesty International’s past corporate responsibility campaign. See also their 2006 full report on China Internet issues.
- Global Voices recommends Tor, especially for anonymous blogging, throughout their web site.
- In the US, the Supreme Court recently stripped legal protections from government whistleblowers. But whistleblowers working for governmental transparency or corporate accountability can use Tor to seek justice without personal repercussions.
- A contact of ours who works with a public health nonprofit in Africa reports that his nonprofit must budget 10% to cover various sorts of corruption, mostly bribes and such. When that percentage rises steeply, not only can they not afford the money, but they can not afford to complain — this is the point at which open objection can become dangerous. So his nonprofit has been working to use Tor to safely whistleblow on government corruption in order to continue their work.
- At a recent conference, a Tor staffer ran into a woman who came from a “company town” in the eastern United States. She was attempting to blog anonymously to rally local residents to urge reform in the company that dominated the town’s economic and government affairs. She is fully cognizant that the kind of organizing she was doing could lead to harm or “fatal accidents.”
- In east Asia, some labor organizers use anonymity to reveal information regarding sweatshops that produce goods for western countries and to organize local labor.
- Tor can help activists avoid government or corporate censorship that hinders organization. In one such case, a Canadian ISP blocked access to a union website used by their own employees to help organize a strike.
High & low profile people use Tor
- Does being in the public spotlight shut you off from having a private life, forever, online? A rural lawyer in a New England state keeps an anonymous blog because, with the diverse clientele at his prestigious law firm, his political beliefs are bound to offend someone. Yet, he doesn’t want to remain silent on issues he cares about. Tor helps him feel secure that he can express his opinion without consequences to his public role.
- People living in poverty often don’t participate fully in civil society — not out of ignorance or apathy, but out of fear. If something you write were to get back to your boss, would you lose your job? If your social worker read about your opinion of the system, would she treat you differently? Anonymity gives a voice to the voiceless. Although it’s often said that the poor do not use online access for civic engagement, failing to act in their self-interests, it is our hypothesis (based on personal conversations and anecdotal information) that it is precisely the “permanent record ” left online that keeps many of the poor from speaking out on the Internet. We hope to show people how to engage more safely online, and then at the end of the year, evaluate how online and offline civic engagement has changed, and how the population sees this continuing into the future.

Business executives use Tor
- Security breach information clearinghouses: Say a financial institution participates in a security clearinghouse of information on Internet attacks. Such a repository requires members to report breaches to a central group, who correlates attacks to detect coordinated patterns and send out alerts. But if a specific bank in St. Louis is breached, they don’t want an attacker watching the incoming traffic to such a repository to be able to track where information is coming from. Even though every packet were encrypted, the IP address would betray the location of a compromised system. Tor allows such repositories of sensitive information to resist compromises.
- Seeing your competition as your market does: If you try to check out a competitor’s pricing, you may find no information or misleading information on their web site. This is because their web server may be keyed to detect connections from competitors, and block or spread disinformation to your staff. Tor allows a business to view their sector as the general public would view it.
- Keeping strategies confidential: An investment bank, for example, might not want industry snoopers to be able to track what web sites their analysts are watching. The strategic importance of traffic patterns, and the vulnerability of the surveillance of such data, is starting to be more widely recognized in several areas of the business world.
- Accountability: In an age when irresponsible and unreported corporate activity has undermined multi-billion dollar businesses, an executive exercising true stewardship wants the whole staff to feel free to disclose internal malfeasance. Tor facilitates internal accountability before it turns into whistleblowing.
Bloggers use Tor
- Frequently we hear about bloggers who are sued or fired for saying perfectly legal things online, in their blog.
- We recommend the EFF Legal Guide for Bloggers.
- Global Voices maintains a guide to anonymous blogging with WordPress and Tor.

Militaries use Tor
- Field agents: It is not difficult for insurgents to monitor Internet traffic and discover all the hotels and other locations from which people are connecting to known military servers. Military field agents deployed away from home use Tor to mask the sites they are visiting, protecting military interests and operations, as well as protecting themselves from physical harm.
- Onion services: When the Internet was designed by DARPA, its primary purpose was to be able to facilitate distributed, robust communications in case of local strikes. However, some functions must be centralized, such as command and control sites. It’s the nature of the Internet protocols to reveal the geographic location of any server that is reachable online. Tor’s onion services capacity allows military command and control to be physically secure from discovery and takedown.
- Intelligence gathering: Military personnel need to use electronic resources run and monitored by insurgents. They do not want the webserver logs on an insurgent website to record a military address, thereby revealing the surveillance.
IT Professionals use Tor
- To verify IP based firewall rules: A firewall may have some policies that only allow certain IP addresses or ranges. Tor can be used to verify those configurations by using an IP number outside of the company’s alloted IP block.
- To bypass their own security systems for sensitive professional activities: For instance, a company may have a strict policy regarding the material employees can view on the internet. A log review reveals a possible violation. Tor can be used to verify the information without an exception being put into corporate security systems.
- To connect back to deployed services: A network engineer can use Tor to remotely connect back to services, without the need for an external machine and user account, as part of operational testing.
- To access internet resources: Acceptable use policy for IT Staff and normal employees is usually different. Tor can allow unfettered access to the internet while leaving standard security policies in place.
- To work around ISP network outages: Sometimes when an ISP is having routing or DNS problems, Tor can make internet resources available, when the actual ISP is malfunctioning. This can be invaluable in crisis situations.
Please do send us your success stories. They are very important because Tor provides anonymity. While it is thrilling to speculate about undesired effects of Tor, when it succeeds, nobody notices. This is great for users, but not so good for us, since publishing success stories about how people or organizations are staying anonymous could be counterproductive. For example, we talked to an FBI officer who explained that he uses Tor every day for his work — but he quickly followed up with a request not to provide details or mention his name.
Like any technology, from pencils to cellphones, anonymity can be used for both good and bad. You have probably seen some of the vigorous debate (pro, con, and academic) over anonymity. The Tor project is based on the belief that anonymity is not just a good idea some of the time — it is a requirement for a free and functioning society. The EFF maintains a good overview of how anonymity was crucial to the founding of the United States. Anonymity is recognized by US courts as a fundamental and important right. In fact, governments mandate anonymity in many cases themselves: police tip lines, some adoption services, police officer identities, and so forth. It would be impossible to rehash the entire anonymity debate here — it is too large an issue with too many nuances, and there are plenty of other places where this information can be found. We do have a Tor abuse page describing some of the possible abuse cases for Tor, but suffice it to say that if you want to abuse the system, you’ll either find it mostly closed for your purposes (e.g. the majority of Tor relays do not support SMTP in order to prevent anonymous email spamming), or if you’re one of the Four Horsemen of the Information Apocalypse, you have better options than Tor. While not dismissing the potential abuses of Tor, this page shows a few of the many important ways anonymity is used online today.
What is Tor Browser?
Tor (The Onion Router) is a network that anonymizes web traffic to provide truly private web browsing. The Tor Browser hides your IP address and browsing activity by redirecting web traffic through a series of different routers known as nodes. Because Tor hides browsing activity and blocks tracking, it’s used by whistleblowers, journalists, and others who want to protect their privacy online.
Tor anonymizes web traffic with a special encryption technique originally developed by the US Navy to help protect American intelligence communications. Today, Tor is an open-source, privacy platform available to everyone. Though some countries — like China — have banned its use outright.
Besides a web browser, Tor also provides onion services via its onion network to enable anonymity for websites and servers. A [dot]onion web address, which is exclusively accessible via the Tor Browser, protects the identity of both the website and visitors.
With a complex, encrypted connection that offers up anonymity for both hosts and visitors, Tor is often used to create and access the dark web. As such, Tor is the very definition of a dark web browser.
How does Tor, the dark web browser, work?
Tor uses onion routing to encrypt and reroute web traffic through Tor’s onion network. After your data is secured inside multiple layers of encryption, your web traffic is transmitted through a series of network nodes, called onion routers. Each router (or node) “peels away” a layer of encryption until the data reaches its final destination, fully decrypted.
Tor anonymously transmits encrypted data across three layers of international proxies that make up the Tor circuit. Let’s take a closer look at the three layers of network nodes:
- Entry/Guard node: First, Tor Browser randomly connects to a publicly known entry node. The entry node introduces your data into the Tor circuit.
- Middle nodes: Here your data is fully encrypted. Then it’s sent through a series of nodes which decrypt your data one layer at a time. To ensure anonymity, each middle node knows only the identity of the preceding and the subsequent middle nodes.
- Exit node: Once the last layer of encryption is peeled off, the decrypted data leaves the Tor network via an exit node and reaches its final server destination.
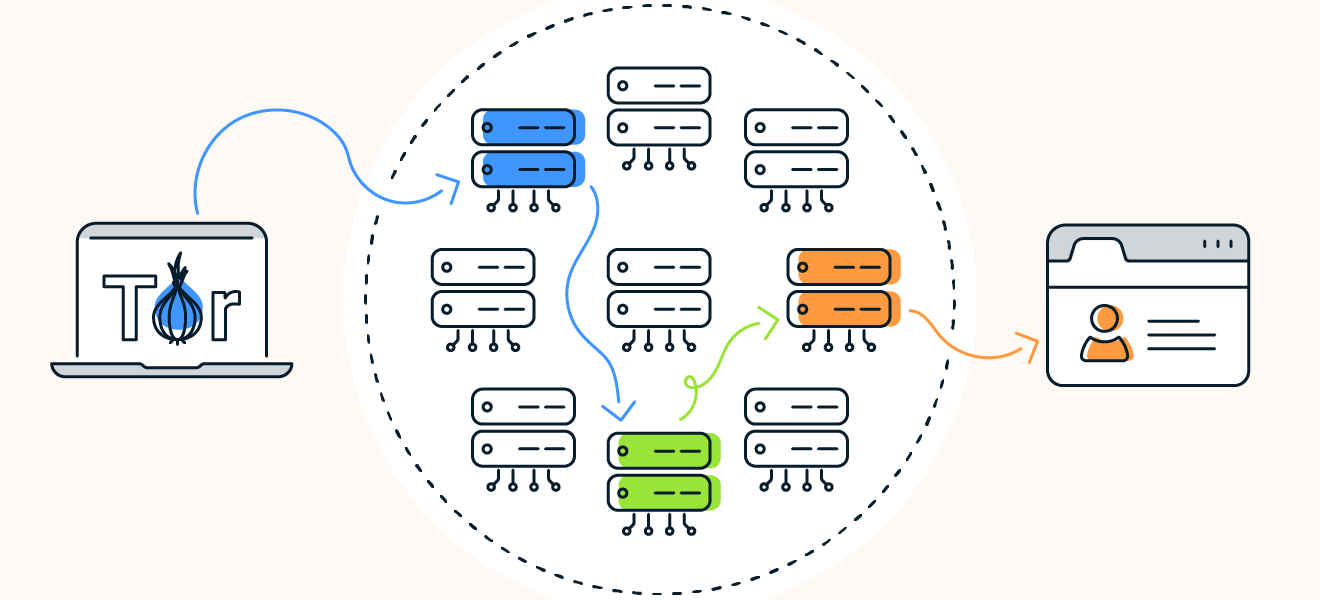 Tor Browser sends web traffic through an entry node (blue), middle node (green), and exit node (orange) to encrypt and decrypt traffic.
Tor Browser sends web traffic through an entry node (blue), middle node (green), and exit node (orange) to encrypt and decrypt traffic.
Sounds complicated, right? That’s because it is. But fortunately knowing how to use Tor Browser doesn’t require a PhD in computer science — it’s surprisingly easy and user-friendly.
Does Tor Browser hide your IP and how?
Tor Browser’s onion routing technology is extremely effective at concealing your IP address from network surveillance or traffic analysis. In addition to relaying your data through network nodes to hide your location and identity, onion routing uses multi-layered encryption to provide even more robust privacy protection.
Because Tor-encrypted data needs to be “peeled“ through more than 7,000 independent network relays before it’s fully decrypted, by the time internet traffic reaches its destination, its origin is completely obscured. This elaborate process shows how secure Tor is at protecting data and hiding your IP address from websites, your ISP, and even the government.
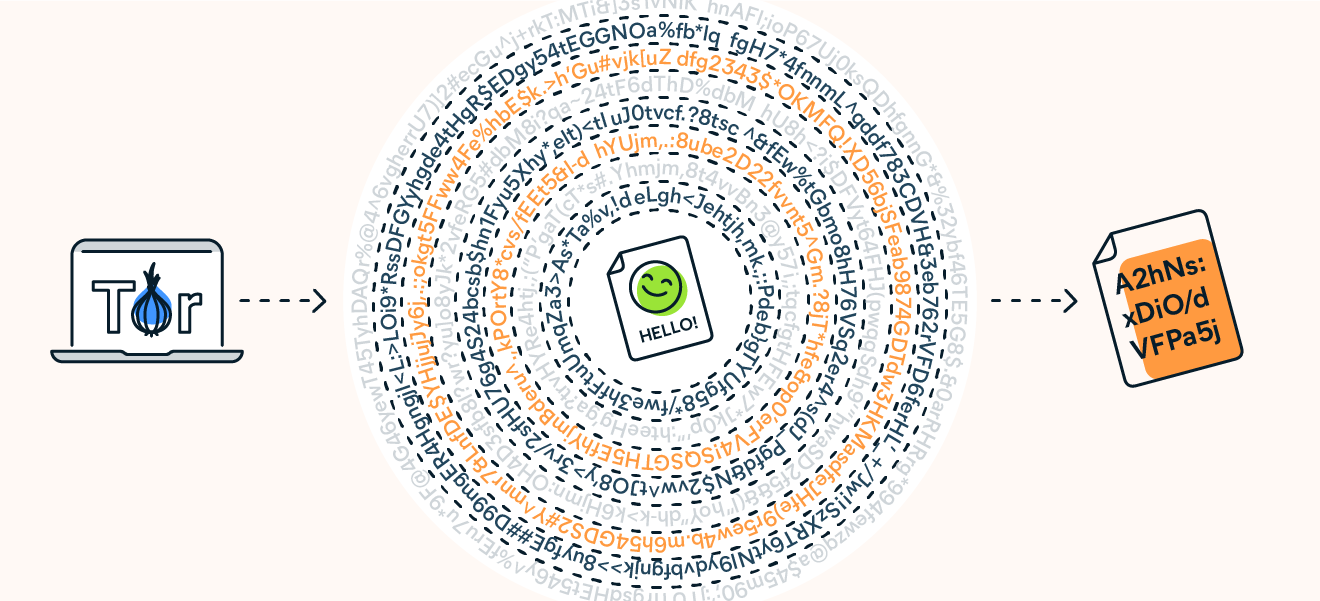 Your web traffic goes through thousands of layers of decryption when connecting to the internet via Tor Browser.
Your web traffic goes through thousands of layers of decryption when connecting to the internet via Tor Browser.
Is Tor Browser anonymous?
Tor Browser is anonymous in terms of hiding your location and browsing activity — but there are limits. Although they can’t see your browsing activity or Tor encrypted data, your ISP can still see that you’re using Tor. You can also be identified if you log in to an online account or provide details to a website while using Tor.
What is the difference between Tor Browser and a proxy server?
A proxy server acts as an intermediary between you and web sites and services. While proxies hide your IP address and location, they don’t encrypt internet traffic, meaning your data is still exposed in transit. Tor Browser is much more secure thanks to onion routing and multi-layer encryption, which anonymizes your location and protects your data from hackers, web trackers, and other snoops.
Using a proxy server in combination with Tor Browser can help to hide the fact that you’ve connected to Tor, but it won’t confer any additional cybersecurity benefits. Not sure which private browsing tool you need? Read our guide to see whether a VPN, proxy, or Tor is best.
Is Tor a VPN?
Tor is not the same as a VPN, though both tools provide encryption and reroute your web traffic to another network. A key difference between Tor and a VPN is that a VPN’s network is operated by a central service provider, while the Tor network is decentralized and run by volunteers.
In addition, Tor and VPNs take different approaches to rerouting data. A VPN sends your web traffic to a server, which transmits it to the internet. Tor’s onion routing method reroutes your data through a series of independent nodes. Though Tor is slower, the process of rerouting data through nodes makes it more difficult to trace your activity back to you.
What is Tor Browser used for?
Tor Browser is primarily used as a method of anonymous browsing. From journalists and civil society organizations seeking to escape spying or political repression, to regular individuals with online privacy concerns, Tor Browser users are a diverse group. But criminals also take advantage of Tor’s anonymity to carry out illegal activities both on and off the dark web.
Can I be tracked while using Tor?
Despite its impressive privacy features, there are still ways that you can be tracked while using Tor. Onion routing is a sophisticated means to prevent tracking your location, but there’s no such thing as perfect online anonymity.
Although your internet traffic is encrypted on Tor, your ISP can still see that you’re connected to Tor. Plus, Tor cannot protect against tracking at the entry and exit nodes of its network. Anyone who owns and operates the entry node will see your real IP address. And at the exit node, your decrypted traffic is vulnerable to interception.
You can reinforce Tor’s weak spots by pairing it with a VPN that provides end-to-end encryption. That means your web traffic will be fully encrypted at the entry and exit nodes of the Tor network, and using VPN-over-Tor will keep your real IP address safe from any prying eyes lurking at those gateways.
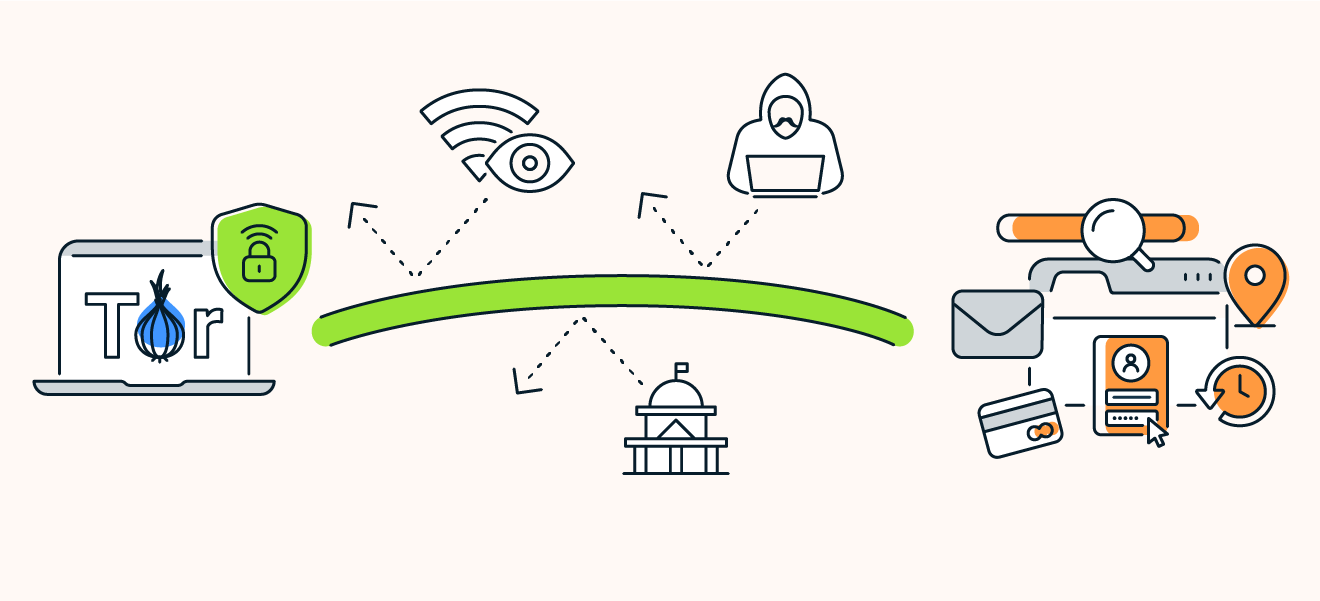 Use Tor alongside a VPN to ensure your web traffic is fully encrypted.
Use Tor alongside a VPN to ensure your web traffic is fully encrypted.
Reasons to use Tor
One of the main reasons to use Tor is the high level of privacy provided by the onion network. Not only do Tor’s security protocols allow users to access sites safely and hide their IP address, but the browser is open-source, free, and simple to use, especially considering the complex protection it provides.
Is Tor Browser legal?
Tor Browser is legal to use in most countries, although there may be a stigma attached to using it, because Tor is often associated with dark web criminality. But despite its sometimes seedy reputation, the dark web is host to many legitimate resources, like the dark web wikipedia, secure email services, and research databases. If you’re not engaged in illicit activities, it’s not a crime to use the dark web to protect your privacy.
Still, Tor usage can call undue attention to your web activity, which could be counter-productive if you’re seeking privacy. ISPs have been known to throttle internet speeds and even contact customers about Tor usage. Your government may also track your activities if you use Tor.
In some countries, Tor itself is outlawed. China has banned anonymous browsing — making Tor illegal to use. Other countries like Russia and Venezuela actively try to block their citizens from using Tor. If you’re interested in anonymous browsing, first check whether Tor or VPNs are legal in your country.
Is Tor Browser safe?
The Tor Browser is generally considered safe and secure thanks to onion routing protocol that encrypts your data and hides your IP address. But Tor does have some vulnerabilities, and as with any browser, Tor users remain vulnerable to online threats, ranging from malware to phishing scams.
Knowing how to safely use Tor means using it alongside other cybersecurity tools, so set up a VPN to benefit from end-to-end encryption. And make sure your network’s protected by a firewall and the best antivirus software.
Tor Browser and the dark web
For many, Tor is synonymous with the dark web — the unindexed part of the internet that’s only accessible with certain browsers. The connection between Tor and the dark web started with the Silk Road, the first dark web market where customers could buy drugs and other illegal goods. When in operation, the notorious online marketplace could only be accessed through Tor.
As a browser that enables anonymity to both website hosts and visitors, the appeal of Tor to dark web participants is obvious. And though the dark web is not just a haven for illicit activity, accessing the dark web via the onion browser is popular with criminals.
But Tor was not designed with criminality in mind, or intended to be the “dark web browser.” Tor is a legitimate and effective online privacy tool that’s used by a variety of users who value their online privacy and data security.
The disadvantages of Tor Browser
Although Tor is a sophisticated privacy tool, it has several disadvantages — some of which counteract its cybersecurity advantages.
Here are the disadvantages of using Tor:
- Slow Speeds: Tor is a slow browser. Onion routing encrypts web traffic and sends it through a series of network nodes — this is great for privacy, but the elaborate process results in slow speeds compared to other browsers. Although there are ways of making Tor faster, you can’t significantly boost speeds.
- Stigma: Tor has acquired the unfortunate stigma of dark web illegality. ISPs and governments may take note of people who use the browser. For people seeking privacy, Tor may bring them the opposite.
- Blocking: Some network administrators block Tor. Some websites also keep track of and block web traffic coming from Tor exit nodes. But you can mask node usage by using Tor bridges or a VPN.
- Vulnerabilities: Though Tor is designed for anonymity, the onion network is vulnerable at the entry and exit nodes. Since internet traffic is not encrypted at these points, your data is liable to interception, and your IP address could be exposed.
Other dark web browsers
Though the Tor Browser has strong ties with dark web browsing, it also has competition. There are other browsers that can also access the dark web. Though Tor enables anonymity, these other browsers have their own advantages.
Here are the other dark web browsers:
- Subgraph OS: This open-source operating system is designed to be resistant to surveillance and other snoops. It’s been mentioned by whistleblower Edward Snowden as showing potential.
- Firefox: Though this popular and accessible browser can access the dark web, it lacks safety features.
- Waterfox: Based on Firefox, the Waterfox browser is fast and features tracking protection to safeguard your privacy.
- I2P – Invisible Internet Project: Similar to Tor, this is a fully-encrypted, private network layer.
How to use Tor Browser on Windows and Mac
Tor is currently available for Windows, Mac, and Linux. It’s a Firefox-based app that’s downloaded and installed on your computer. After installation, you can use Tor to access the public internet as well as .onion websites.
Here’s how to use Tor on Windows and Mac:
- On the Tor project website, go to the Tor Browser download page.
- Click on the download link for your OS.
- Once downloaded, install the Tor Browser application.

- Launch the Tor Browser application and connect to the Tor network.
Now that you’ve got Tor set up on your computer, you may want to change your default browser for maximum privacy. Check out our review of the best browsers for security and privacy.
How to use Tor on mobile
Tor is available on mobile only for Android devices, as there’s no Tor Browser for iPhone. The mobile Tor Browser is an application you can download on the Tor project website and the Google Play store.
Here’s how to access Tor on your Android device:
- On the Tor project website, go to the Tor Browser download page. Or, find and download the app in the Google Play store.
- Download the app on your Android device.

- Click the app icon on your home screen to launch the browser.
Browse securely and privately online
Though Tor is a powerful tool for anonymous browsing, it’s not without flaws. Tor is slow and can be vulnerable to attacks. And Tor may attract unwanted attention from your government or ISP. source
https://www.torproject.org/download/
Tor – The Onion Router
What is Tor?
Tor is a network of virtual tunnels that allows you to improve your privacy and security on the Internet.
Privarcy is a human right. We at Tor advance human rights and defend your privacy online through free software and open networks
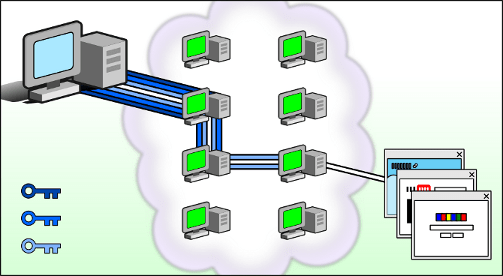
Tor works by sending your traffic through three random servers (also known as relays) in the Tor network. The last relay in the circuit (the exit relay) then sends the traffic out onto the public Internet.
The image above illustrates a user browsing to different websites over Tor. The green middle computers represent relays in the Tor network, while the three keys represent the layers of encryption between the user and each relay.
It protects you by bouncing your communications around a distributed network of relays run by volunteers all around the world, it prevents somebody watching your Internet connection from learning what sites you visit and it prevents the sites you visit from learning your physical location.
This collection of volunteer relays is called the Tor network.
The way most people use Tor is with the Tor Browser, which is based on Firefox ESR and comes bundled with privacy enhancing & anti-fingerprinting features.
So is Tor a VPN?
Nope. Tor is NOT a VPN and furthermore it is not recommended to use Tor and VPN together.
These are fundamentally very different. In the case of VPN, you’re just transferring your trust from your internet service provider (ISP) to the VPN provider.
The VPN provider can log any data while you use their network and anyone snooping on the VPN connection can also easily gain knowledge of your activities.
While using Tor, your connection is made to the website by bouncing the connection through three different relays so the website you’re connecting to can only see the IP address of the ‘exit’ relay
Some more about Tor
The Tor Browser furthermore comes bundled with features like: a different circuit of every different domain, i.e. a new circuit for every website you’re connecting to so as to mitigate cross-site tracking; ‘Security Settings’ with which you can also disable most of the harmful JavaScript.
The noteworthy part is that the idea is not to hide that you’re using the Tor network but to anonymize your activities on the Tor network.
Tor is an essential tool for privacy and anonymity on the internet. It is a tool used by millions of people all around the globe – from journalists to human rights activists to ordinary people
Challenges
Direct access to the Tor network may sometimes be blocked by your Internet Service Provider or by a government. Tor Browser includes some circumvention tools for getting around these blocks. These tools are called pluggable transports. source
The Onion Router – Tor Browser
A while ago I created a course, called Dark Web Expert. It is about the Onion Network/Tor Browser how it works, the history, how to use it in many different ways with different purposes, and the Tor vulnerabilities.
I never post it anywhere, I planned to post the videos on YouTube (for free), but I changed my mind because I don’t want to expose knowledge that people with bad intentions can use. But I am want to reveal how GREAT Tor network is. (In my opinion, the safest way to navigate on the internet nowadays is that we have trackers everywhere.)
The course that I created has about 2 hours, but I decide to post only 2 short videos (less than 5min.). These videos are a fundamental explanation of how the “surface web” (traditional internet) and how the Onion Networks (Tor) works.
Some people think that Tor is only used by criminals, they are completely wrong, you can easily download the Tor browser (https://www.torproject.org/) and navigate in the “surface web” and some big companies is there, like The New York Times, FaceBook, ProPublica, The Guardian, The Intercept, Vice… source
Also, I want to let you know that a strong market exists that monitors and explores this network to catch criminals and help companies stay safe. If you are interested in now more about those companies, please check:
Terbium Labs – https://terbiumlabs.com/
IBM X-Force Iris – https://www.ibm.com/security/services/threat-intelligence
AlienApp – https://cybersecurity.att.com/app/dark-web-monitoring
Forensic Pathways – https://www.forensic-pathways.com/
May you also be interested in the document “Wolves of the Internet – Where do fraudsters hunt for data online?” created by Cifas and Forensic Pathways
What Is the Tor Browser? A Guide to the Dark Web Browse
The Tor browser is a web browser that lets users stay anonymous online while on the dark web and protects them to a certain degree from being tracked by hackers, internet service providers, and even corporations and governments. This browser is the main offering of the Tor project, which focuses on creating open-source anonymity and privacy-focused technologies.
In this article, we walk you through the intricacies of the Tor browser, how to use it to access the dark web, and its advantages over other privacy-related solutions, like a proxy server. However, we will also delve into some of the drawbacks of using this browser.
What Is the Tor Browser?

The Tor browser, also known as the onion browser or dark web browser, is an abbreviation of the “The Onion Router.” It is a completely free, open-source browser that helps you surf the internet anonymously. It erases your browsing history automatically with every session and encrypts all your traffic.
With Tor, you can access the dark web — the hidden and un-indexed websites on the internet. Tor’s ability to enable users to access the internet freely has led to some countries blocking it entirely.
Originally, the Tor network was developed by the U.S. Navy to enable anonymous online communication for military organizations. In 2006, the military dropped the project, which has since been handled by a non-profit.
These days, the Tor project mainly focuses its attention on its browser and the development of a few other privacy tools, which we’ll touch on later.
How does the Tor browser work?
Tor aims to improve your online privacy and, up to a point, your security. The browser uses Tor’s vast worldwide server network to hide your IP and secure your connection.
When using the Tor browser, your data goes through different Tor servers (or nodes):
- Entry node: This is the first node Tor connects with. Your IP address is visible here, but the entry node cannot see what you are connecting with.
- Relay node: This node passes along the traffic it receives.
- Exit node: This part of the Tor server forwards you to the website you want to see. Your IP address is not visible here, but your destination is.
The traffic is heavily encrypted at the first node and then slowly decoded — one layer at a time at the different nodes.
This means that, whoever is trying to identify you based on your online traffic, will just stumble on the last server your data traffic passed through (a.k.a. the “Tor exit node”). In other words: this browser makes it impossible — or at least very difficult — to identify Tor users. For surfing the web anonymously, using this dark web browser is better than using a normal web browser.

This triple-layered encryption comes with a disadvantage, though. The Tor browser is generally much slower than your bare internet connection. Because your online traffic is sent through different nodes, your internet connection will have to go the long way around and therefore become significantly slower.
Is the Tor browser legal?

The use of the Tor/dark web browser itself (and any other Tor project software) is completely legal in most jurisdictions, especially in countries with minimal censorship. However, some Tor users do engage in illegal activities.
Using the Tor browser doesn’t make these activities any less illegal. Therefore, we strongly advise you to refrain from such practices. You also need to understand the legal consequences of using Tor.
What Can I Do With the Tor Browser?

Many people use the Tor web browser to do the following:
- View geo-restricted content
- Bypass censorship
- Visit websites not available on the surface web but accessible on the dark web
The dark web consists largely of unregulated websites, although some of these dark net websites are worth visiting. The dark web also contains pirated content and illegal substances.
Besides visiting the dark web, many journalists and political activists use the Tor browser to circumvent censorship. The anonymity provided by Tor helps them avoid being spied on by interested parties and lets them publish articles and spread news about important events.
Popular news media like BBC News and ProPublica have “onion websites” (a.k.a. dark web versions of their regular websites).
Similarly, journalists use the Tor browser to protect their sources. People who don’t want to risk being revealed or tracked can communicate sensitive information through the Tor network.
The Tor browser and the dark web

The Tor browser is one of the best browsers for visiting the dark web anonymously.
The dark web generally features websites that you can’t access through a normal search engine or via a conventional browser. You must also know the exact web address to visit a dark web website.
As we’ve already mentioned, the dark web is home to unregulated websites, which means you can find anything from pirated movies to black markets, illegal drugs, and child pornography on there.
As such, we don’t advise visiting the dark net unless you know what you’re doing. source
The Main Stream Now Uses Tor
The New York Times is Now Available as a Tor Onion Service
During the fall of 2021, The New York Times rebuilt it’s existing Onion service, added the “Onions Por Favor” service to the public New York Times website, and issued a new V3 Onion address.
As with our previous Onion Service, visitors will not be able to create Times accounts or log in to their existing Times account via the V3 Onion service.
The current address for our Onion Service is https://www.nytimesn7cgmftshazwhfgzm37qxb44r64ytbb2dj3x62d2lljsciiyd.onion/
BBC News launches ‘dark web’ Tor mirror
The BBC has made its international news website available via the Tor network, in a bid to thwart censorship attempts.
The Tor browser is privacy-focused software used to access the dark web.
The browser can obscure who is using it and what data is being accessed, which can help people avoid government surveillance and censorship.
Countries including China, Iran and Vietnam are among those who have tried to block access to the BBC News website or programmes.
- BBC News in Ukrainian: https://www.bbcweb3hytmzhn5d532owbu6oqadra5z3ar726vq5kgwwn6aucdccrad.onion/ukrainian
- BBC News in Russian: https://www.bbcweb3hytmzhn5d532owbu6oqadra5z3ar726vq5kgwwn6aucdccrad.onion/russian
- BBC News internationally: https://www.bbcweb3hytmzhn5d532owbu6oqadra5z3ar726vq5kgwwn6aucdccrad.onion
Facebook onion address
The Facebook onion address located at facebookwkhpilnemxj7asaniu7vnjjbiltxjqhye3mhbshg7kx5tfyd.onion (formerly facebookcorewwwi. onion) is a site that allows access to Facebook through the Tor protocol, using its . onion top-level domain.
CIA’s Latest Layer: An Onion Site
ciadotgov4sjwlzihbbgxnqg3xiyrg7so2r2o3lt5wz5ypk4sxyjstad.onion
It’s hard to tell how many dark web sites there are really out there, but a lot of people agree on the most worthy ones to visit. According to our extensive research, these include:
- The Hidden Wiki: A handy overview with lots of links to relevant dark web websites
- DuckDuckGo: The search engine of choice on the dark web
- Ahmia: A dark web search engine that allows for detailed searches
- Daniel: Another overview of very convenient dark web links
- Keybase: Secure file sharing over the dark web
- SecureDrop: A safe haven for whistleblowers
Just remember: browsing the dark web is exciting but dangerous. If you’re not careful, you’ll put your device and data at risk.